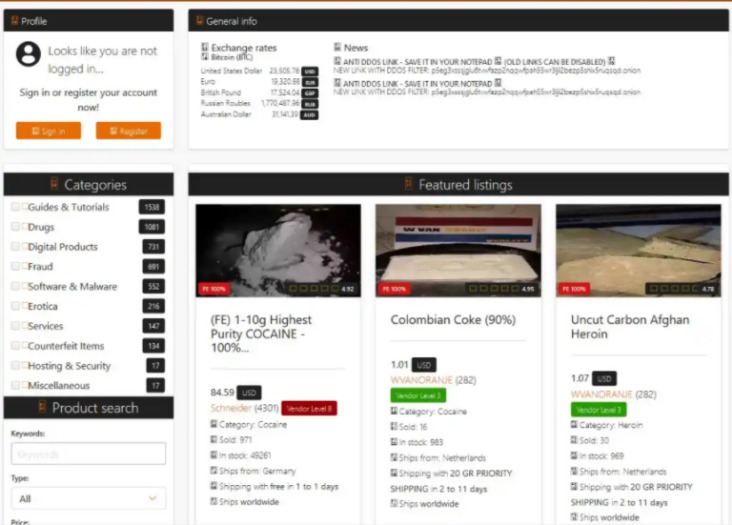
Nexus Darknet Market Overview
The Nexus Darknet Market is a well-known online marketplace that operates within the hidden segments of the internet, often accessed through specialized software. It provides a platform for various illegal and gray-market transactions, ranging from digital goods to other illicit services. As one of the more prominent markets in the darknet ecosystem, Nexus is recognized for its user-friendly interface and extensive product listings. For those interested in exploring further, more information about similar darknet markets can be found through resources like Nexus Darknet Market. Understanding its structure and operation offers valuable insights into how these clandestine markets function and their impact on cyber safety and law enforcement worldwide.
History and Background of Nexus
The Nexus darknet market emerged as a notable platform within the hidden online ecosystem, catering to users seeking anonymous trade and information exchange. Known for its structured environment and focus on user privacy, Nexus attracted a diverse user base involved in various categories of transactions. Its development marked a significant chapter in the evolution of darknet markets, emphasizing security measures to protect both vendors and buyers. Over time, Nexus established itself as a trusted name among darknet marketplaces, gaining recognition for its streamlined interface and commitment to confidentiality.
The history of Nexus dates back to its inception in the early 2010s, during a period when darknet markets were rapidly expanding. It was founded by a group of developers aiming to create a platform that prioritized security and ease of use. Throughout its operational years, Nexus faced numerous challenges, including law enforcement scrutiny and internal security threats, yet it managed to sustain its presence in the underground economy. Its background is marked by continuous updates and adaptations to stay ahead of detection techniques, making it a resilient player in the darknet scene.
Several key features distinguish Nexus from other darknet markets:
- Strong emphasis on user privacy and transaction security
- Comprehensive moderation and community standards
- Robust dispute resolution processes to ensure trustworthiness
- Multiple tiers of anonymity layers for both vendors and buyers
- A diverse range of available product and service categories
Understanding the background of Nexus provides insight into the broader dynamics of darknet markets, highlighting the ongoing arms race between security measures and law enforcement efforts. As a platform, Nexus continues to influence the design and operation of darknet marketplaces, embodying the persistent quest for privacy in digital transactions.
Market Structure and Organization
The Nexus Darknet Market is a notable platform within the realm of online illicit trade, operating on the hidden layers of the internet to facilitate the anonymous exchange of goods and services. It functions in a manner similar to conventional markets but is designed to maintain the privacy and security of its users through the use of encryption, decentralized hosting, and secure communication protocols. Such markets typically attract a diverse user base, including vendors and buyers seeking to buy or sell items outside legal boundaries, often utilizing cryptocurrencies for transactions to ensure anonymity.
The market structure of Nexus Darknet Market is generally organized into multiple tiers or categories, reflecting its complex and decentralized nature. Vendors are usually registered within specific categories based on the type of products they offer, such as narcotics, digital goods, or hacking services. Buyers browse through various listings, which are often accompanied by seller ratings, reviews, and feedback systems to promote transparency and trust within the anonymous environment. The platform usually employs escrow services to safeguard transactions, releasing funds only when both parties fulfill their obligations.
Behind the scenes, the organization of Nexus Darknet Market resembles a peer-to-peer network, with decentralized servers and layered security mechanisms to prevent detection by law enforcement agencies. Multiple layers of encryption and the frequent updating of operational protocols help maintain the market’s longevity and resilience against takedown efforts. The administration team typically exercises control over vendor registration, dispute resolution, and the overall functioning of the platform, ensuring that it remains operational for its user community. Despite its illegal activities, such markets often emphasize security, anonymity, and operational continuity to sustain their illicit economies.

Access and Entry Requirements
The Nexus Darknet Market is a well-known platform within the underground online marketplace ecosystem, primarily accessible through the Tor network. It offers a wide variety of goods and services, often including items that are illegal or heavily regulated in many jurisdictions. Due to its discreet and encrypted nature, accessing Nexus Darknet Market requires specific precautions and understanding of the entry process, emphasizing security and anonymity.
To access Nexus Darknet Market, users typically need to utilize the Tor Browser, which enables anonymous browsing by routing connection through multiple servers worldwide. This setup helps conceal the user’s IP address and location, providing a layer of protection against surveillance. When visiting the site, users are often required to authenticate via credentials that are usually obtained through invitation or membership systems, which help maintain the platform’s security and exclusivity.
Entry requirements for Nexus Darknet Market generally include creating a secure account and adhering to strict security protocols. It is highly recommended to use strong, unique passwords and consider employing additional security measures such as VPNs. Users should also ensure their system is free of malware or tracking tools before engaging with the platform. Transactions are mainly conducted using cryptocurrencies like Bitcoin or Monero, which provide further anonymity.
Overall, accessing Nexus Darknet Market involves a combination of specialized software, security measures, and knowledge of the marketplace’s operational procedures. While the platform promises privacy and a broad scope of offerings, users must remain vigilant and aware of legal and ethical considerations associated with their activities.
Malware Offerings on Nexus
Malware offerings have become an increasingly prevalent aspect of activities on various darknet markets, including the notorious Nexus darknet market. These marketplaces serve as platforms where malicious software, tools, and services are exchanged among cybercriminals. Such offerings can encompass a wide range of malware types, from ransomware and spyware to botnets and phishing kits, enabling users to conduct various illicit operations. Understanding the scope of malware available on Nexus is crucial for cybersecurity professionals and researchers aiming to unravel the complexities of cyber threats circulating in these hidden online environments. For those interested in exploring further, additional resources and related marketplaces can be found through relevant darknet links.
Types of Malware Available
Malware offerings on darknet markets like Nexus are a significant concern for cybersecurity professionals and users alike. These illicit platforms often serve as hubs where cybercriminals acquire malicious software to facilitate various cyber attacks. The variety of malware available can range from basic tools to complex packages designed to infiltrate, disrupt, or manipulate targeted systems.

Among the types of malware offered, there are trojans, which masquerade as legitimate software to gain unauthorized access; ransomware, designed to encrypt data and demand payment for decryption keys; keyloggers that record keystrokes to harvest confidential information; and spyware that clandestinely monitors user activity. Additionally, backdoors are sold to give attackers persistent access to compromised systems, while botnets—networks of infected devices—are assembled using malware to conduct large-scale denial-of-service attacks or spamming activities.
The marketplace dynamics on Nexus and similar platforms facilitate the exchange of these malicious tools, enabling even less technically skilled actors to deploy harmful campaigns. Sellers often provide support, updates, and customization options to enhance their malware’s effectiveness, making these offerings a continual threat to individuals and organizations. Cybersecurity efforts focus on monitoring and disrupting these illicit markets to prevent the proliferation and misuse of malware, thereby protecting digital environments from malicious activities.
Features of Commodity Malware
The darknet market known as Nexus has gained attention due to its diverse malware offerings, which are often used by cybercriminals for various malicious activities. Malware on these platforms typically includes a range of tools designed to compromise, control, or exploit targeted systems, making them attractive to hackers seeking flexible or ready-made solutions for cyberattacks. Understanding the characteristics of commodity malware available on such markets is essential for cybersecurity professionals and organizations aiming to defend their digital assets.
Commodity malware refers to widely available, pre-packaged malicious software that can be easily purchased or acquired on dark web marketplaces like Nexus. These malware types are often standardized and designed for mass deployment, making them accessible even to individuals with limited technical expertise. Common features include user-friendly interfaces, ready-to-use payloads, and the ability to customize certain aspects to target specific environments or objectives.
One prominent feature of commodity malware is its modular design, allowing cybercriminals to select and assemble different components based on their needs. This includes remote access trojans (RATs), keyloggers, ransomware, and spamming tools that can be tailored for different attack vectors. Many of these offerings include detailed documentation and support, further lowering the barrier to entry for perpetrators.
Another characteristic is the ease of deployment and versatility. These malware packages are often distributed through infected email attachments, malicious links, or bundled with other malicious software. Their compatibility with various operating systems and environments enhances their appeal, enabling threat actors to target multiple platforms efficiently. The convenience and affordability of commodity malware make it prevalent in underground markets, including the Nexus darknet market.
However, the proliferation of commodity malware represents a significant cybersecurity threat, emphasizing the need for robust defense strategies. Regular system updates, comprehensive threat detection, and user education are vital measures to mitigate risks associated with these widely available malicious tools.
Advanced Malware Listings and Capabilities
The Nexus darknet market has gained notoriety due to its diverse range of malicious software offerings available to its users. Among these offerings are advanced malware listings that demonstrate a high level of sophistication, enabling cybercriminals to execute complex and persistent attacks. Such malware often includes remote access tools, ransomware variants, trojans, and spyware, all designed to compromise systems, steal sensitive data, or disrupt operations.
Malware on this platform is typically categorized based on its capabilities and intended use. Some malware listings feature highly customizable options, allowing buyers to tailor the malicious code to specific targets or attack vectors. The capabilities of these malware offerings often include keylogging, credential theft, lateral movement within networks, and persistence mechanisms to ensure prolonged access. These features make them attractive tools for those engaged in corporate espionage, financial fraud, or other illicit activities.
The advanced malware listings found on the Nexus darknet market often come with detailed descriptions of their capabilities, along with usage instructions and customer support. Buyers can also find malware that is resistant to common detection methods, such as antivirus or intrusion detection systems, making it difficult for security teams to uncover or neutralize the threat. This level of sophistication highlights the importance for organizations to implement comprehensive cybersecurity measures and stay vigilant against emerging malware threats in the digital underground.
User Interaction and Transactions
User interaction and transactions are fundamental components of online marketplaces, especially those operating within the darknet environment. Successful engagement depends on secure, user-friendly interfaces that facilitate seamless communication and transfer of goods or services. In the context of darknet markets such as nexus darknet market, ensuring privacy and trustworthiness is paramount for both buyers and sellers. These platforms often employ advanced encryption methods and anonymity features to protect user identities and transaction details. For those interested in exploring further, numerous resources are available, including sites like Nexus darknet market, which exemplifies these operational standards and provides a secure environment for user interactions and transactions within the shadow economy. Effective management of these interactions helps sustain the functionality and reputation of darknet markets while highlighting the importance of security and privacy in such platforms.
- The convergence of cryptocurrency and the fentanyl crisis represents a troubling evolution in illicit activities.
- These measures significantly reduce the risk of interception, compromise, and cyber attacks.
- Despite increased TTPs available and low barrier to entry for new users, openly advertised malware offerings remain limited to commodity malware.
Buyers and Sellers’ Behavior

Understanding user interaction and transactions in darknet markets is essential for comprehending how buyers and sellers behave within these digital underground economies. Marketplaces like nexus darknet market facilitate the exchange of a wide range of goods and services, often emphasizing anonymity and privacy to protect participants. Buyer behavior typically revolves around seeking discreet communication channels, verifying seller reputation, and ensuring secure transactions to mitigate risks associated with illegal or unregulated activities.
Sellers, on the other hand, emphasize trust-building through feedback systems, prompt communication, and secure payment methods. They often adapt their strategies based on market trends, law enforcement activity, and technological advancements in privacy tools. Transactions are frequently conducted using cryptocurrencies to enhance anonymity, with both parties prioritizing discretion and security. The dynamics within these markets reflect a complex interplay of trust, anonymity, and risk mitigation, shaping how buyers and sellers interact and conduct transactions in the shadow online economy.
Reputation Systems and Validation
Understanding user interaction and transactions, reputation systems, and validation processes is essential when exploring the dynamics of darknet markets such as Nexus Darknet Market. These platforms operate in a clandestine digital environment where trust and security are paramount for both buyers and sellers. Effective user interaction mechanisms facilitate seamless communication, inquiries, and negotiations, enabling participants to establish confidence in transactions despite the anonymous setting.
Reputation systems play a critical role in maintaining integrity within the darknet marketplace ecosystem. They typically involve rating and feedback mechanisms that allow users to share their experiences regarding specific vendors or products. A robust reputation system helps in filtering trustworthy sellers from unreliable ones, fostering a safer trading environment. For instance, on platforms like Nexus Darknet Market, positive feedback boosts credibility, encouraging more users to engage confidently.
Validation processes are equally vital for ensuring transaction legitimacy and preventing fraudulent activities. These mechanisms may include escrow services, cryptographic verification, or multi-factor authentication, which serve to confirm product delivery and payment completion. Accurate validation maintains the functional integrity of darknet markets, safeguarding users involved in sensitive transactions. As a result, users can trust that their dealings are secure, fostering a more reliable marketplace experience.
Use of Cryptocurrencies for Anonymity
The nexus darknet market is a platform that facilitates various user interactions and transactions in an often anonymous environment. Users typically seek to buy and sell goods or services while maintaining privacy, which makes the security and efficiency of their transactions paramount. Cryptocurrencies have become a popular choice for this purpose, mainly due to their decentralized nature and potential for enhanced anonymity.
Utilizing cryptocurrencies in these transactions allows users to bypass traditional banking systems, reducing the risk of transaction tracing and financial surveillance. Many users prefer digital currencies like Bitcoin or privacy-focused coins such as Monero, which offer varying levels of anonymity and security. These digital assets enable seamless peer-to-peer exchanges that support the clandestine environment of platforms like the nexus darknet market.
However, while cryptocurrencies provide benefits for those seeking enhanced privacy, they also pose challenges for law enforcement agencies aiming to combat illegal activities. The use of cryptos in transactions can complicate tracking efforts, making it difficult to link operations to identifiable individuals. Consequently, users often employ multiple layers of obfuscation and privacy features to protect their identities during transactions.
Overall, the integration of cryptocurrencies in darknet markets like the nexus darknet market exemplifies a complex balance between user privacy and regulatory concerns. As these platforms evolve, ongoing developments in blockchain technology continue to influence the dynamics of user interaction and transaction security within this clandestine ecosystem.
Operational Security and Communication Methods
Operational security and effective communication methods are crucial components for navigating the complex and often clandestine environment of darknet markets. Ensuring confidentiality and safety helps protect users from potential threats and legal repercussions. In the context of a darknet market such as nexus darknet market, implementing robust security protocols and encrypted communication channels is essential to maintain anonymity and prevent unauthorized access. Utilizing specialized tools and adherence to best practices in digital security can significantly reduce risks associated with online transactions and interactions. For additional security resources, explore options like secure messaging services or dedicated encryption tools to enhance privacy when engaging with darknet marketplaces.
Private Channels and Encryption
Operational security (OPSEC) and secure communication methods are vital components for maintaining safety and anonymity when engaging with darknet markets like Nexus Darknet Market. Ensuring that sensitive information remains confidential can prevent exposure to malicious actors, law enforcement, or competitors. Proper OPSEC involves a combination of techniques such as avoiding personal identifiers, minimizing digital footprints, and regularly updating security practices to adapt to emerging threats.
Utilizing private channels for communication enhances security by limiting access to authorized individuals and reducing the risk of interception. Encrypted messaging platforms are commonly employed to safeguard conversations, ensuring that the transmitted data remains unreadable to unintended parties. This encryption provides a layer of confidentiality and integrity that is crucial when discussing sensitive transactions or operational details.
Advanced encryption methods, such as end-to-end encryption, are recommended for all communications involving sensitive information related to the Nexus darknet market. These methods ensure that only the intended recipients can decrypt and access the messages. Additionally, employing tools like virtual private networks (VPNs) can help obscure IP addresses and locations, further strengthening operational security.
In conclusion, maintaining strict operational security and using secure communication channels are indispensable practices for participants in darknet markets. By implementing encrypted private channels and adhering to best practices in anonymity, users can mitigate risks and protect their identities while navigating complex and often volatile online environments like the Nexus Darknet Market.
Vague Listings and Indirect Communication
Operational security and effective communication methods are critical components for maintaining safety and anonymity within darknet markets like nexus darknet market. Ensuring that sensitive information remains confidential requires careful planning and disciplined practices. Users should prioritize the use of secure, encrypted channels and avoid sharing personally identifiable information through insecure platforms, which could compromise both individual identities and the overall network. Vague listings and indirect communication strategies are essential tools that help obscure intentions and reduce the risk of detection by monitoring authorities or malicious actors.
Vague listings involve providing minimal details about products or services, making it harder for outsiders to glean specific information that could lead to suspicion. This approach reduces the likelihood of targeted analysis or investigation, allowing traders and buyers to operate more discreetly. Likewise, indirect communication involves using intermediary methods or anonymous messaging systems to relay messages instead of direct communication, further safeguarding identities and operational details. Such tactics are common in the darknet environment, where maintaining anonymity is paramount to prevent infiltration or legal action.
In the context of the nexus darknet market, employing these security measures is vital for ensuring long-term operational integrity. Participants must remain vigilant, adopting best practices for secure communication and being cautious about sharing sensitive information. By combining vague listings with indirect communication methods, users can significantly decrease their exposure to identification threats and mitigate potential risks associated with illicit trade activities.
Seller Vetting and Background Checks
Operational security (OpSec) and effective communication methods are critical components when engaging with any darknet market, including Nexus Darknet Market. Ensuring that your activities remain confidential requires a comprehensive understanding of digital security practices, such as using encrypted messaging channels, anonymizing tools like Tor, and practicing cautious online behavior. Proper OpSec helps prevent identification and reduces the risk of malicious activities or law enforcement intervention. Additionally, establishing secure communication methods minimizes the likelihood of information leaks that could compromise user anonymity and safety.
Seller vetting and background checks are essential to fostering a trustworthy environment on darknet markets. Conducting thorough background assessments of vendors helps to verify their reputation, reliability, and history of previous transactions. This process often involves reviewing user feedback, transaction histories, and assessing consistency in positive reviews. On platforms like Nexus Darknet Market, a transparent review system assists buyers in making informed decisions, while vendors with verified identities and strong track records are generally more reliable. Maintaining rigorous vetting procedures not only enhances buyer confidence but also discourages fraudulent activity, creating a safer marketplace for all participants.
Market Trends and Evolution
The landscape of online markets has undergone significant transformation over the past decade, especially within the realm of darknet platforms. As technology advances and user behaviors evolve, darknet markets continue to adapt their features and offerings to meet changing demands. This ongoing evolution reflects broader trends in digital anonymity, security, and the global approach to online commerce. Understanding these market trends is essential for grasping the dynamics of underground networks and the role of prominent platforms like nexus darknet market in shaping this space. To explore further, one can visit various sources that detail the structure and operations of these markets, including sites like nexus darknet market.
Steady State of Malware Sophistication
The landscape of darknet markets has evolved significantly over the past decade, reflecting broader shifts in technology, user behavior, and law enforcement tactics. One notable trend is the increasing sophistication of malware used by malicious actors to compromise systems and facilitate illegal activities. These advancements enable cybercriminals to deploy highly targeted and resilient tools that can evade traditional detection methods, making cybersecurity defenses more challenging than ever.
Despite rapid technological changes, the core methods employed by cybercriminals remain relatively steady, emphasizing the importance of understanding malware evolution. Attackers frequently refine their techniques, integrating automation, encryption, and stealth features to remain undetected while maximizing their impact. This steady state of malware sophistication underscores the ongoing arms race between cybersecurity professionals and cybercriminals, particularly on platforms like the nexus darknet market, where illegal activities and malware trading are prevalent.
On darknet markets such as the nexus, vendors often offer malware kits and exploit tools that cater to various criminal objectives, from data theft to ransomware deployment. These markets serve as hubs for the exchange of malicious software, reflecting the persistent demand for advanced malware that can bypass security measures. As malware techniques become more refined, law enforcement and security researchers must adapt continuously to combat these evolving threats effectively.
Emerging Threat Techniques
The landscape of darknet markets has experienced significant transformation over recent years, driven by evolving technologies, user demands, and security challenges. As digital anonymity tools become more sophisticated, marketplaces like Nexus Darknet Market have adapted to maintain their relevance. These platforms operate within a complex ecosystem where both innovation and threat techniques continuously compete. Understanding market trends and emerging threat techniques is crucial for comprehending the ongoing evolution within this clandestine sphere.
Market trends indicate a shift towards increased decentralization and heightened emphasis on security features, such as multi-signature transactions and encrypted communications. These innovations aim to protect user identities and financial assets against law enforcement activities and cyber threats. Additionally, the integration of cryptocurrencies that support enhanced privacy features, such as privacy-focused coins, has further contributed to the resilience of darknet markets. The ongoing development of decentralized marketplaces reduces reliance on centralized platforms, making takedowns more difficult and enabling continuous operation despite external pressures.
Emerging threat techniques pose significant risks to both users and operators within the darknet. Cybercriminals frequently employ advanced malware, such as ransomware and remote access Trojans, to target market infrastructure and user devices. Phishing campaigns and social engineering tactics are also intensifying to deceive users into revealing sensitive information. Moreover, threat actors are increasingly leveraging sophisticated methods like blockchain analysis to trace transactions and identify users involved in illegal activities. These tactics necessitate ongoing adaptation and heightened security protocols for marketplaces like Nexus Darknet Market to mitigate vulnerabilities.
Furthermore, the persistence of law enforcement efforts and technological advancements is driving threat actors to develop innovative countermeasures, including the use of anonymization tools and obfuscation techniques for transaction analysis. The continual arms race between security measures and malicious techniques underscores the dynamic nature of the darknet ecosystem. Staying informed of these trends is essential for understanding the risks and the resilience strategies employed by marketplaces and their users in this clandestine digital environment.
Law Enforcement Impact and Market Dynamics
The darknet market landscape is continuously evolving, driven by technological advancements, shifting user behaviors, and changing law enforcement strategies. With the rise of anonymous platforms, markets like Nexus Darknet Market have gained prominence for their focus on privacy and security, attracting a diverse user base seeking illicit goods and services. As these markets grow, they adapt quickly to new threats and opportunities, fueling ongoing innovation within the space.
Market trends indicate a move towards decentralization and the adoption of more sophisticated encryption methods. This evolution makes it increasingly challenging for law enforcement agencies to track transactions and identify participants, thereby impacting the effectiveness of crackdown efforts. On the other hand, authorities are leveraging advanced digital forensics, blockchain analysis, and international cooperation to combat illegal activities associated with darknet markets.
Law enforcement impact has significantly shaped the operational dynamics of darknet markets. Persistent shutdowns and seizures deter some users, but they also incentivize market operators to innovate with measures such as referral systems, escrow services, and decentralized architectures, including the emergence of markets like Nexus Darknet Market. These developments create a resilient ecosystem that continually adapts to enforcement pressures, emphasizing the need for ongoing technological and policy responses.
Market dynamics within the darknet are characterized by competition, trust-building mechanisms, and a constant search for stability amidst uncertainty. Vendors and buyers prioritize anonymity, security, and reliability, leading to the development of reputation systems and secure communication channels. Despite law enforcement efforts, the persistent demand for illicit products sustains a vibrant underground economy, driving further evolution in market structure and operational strategies.