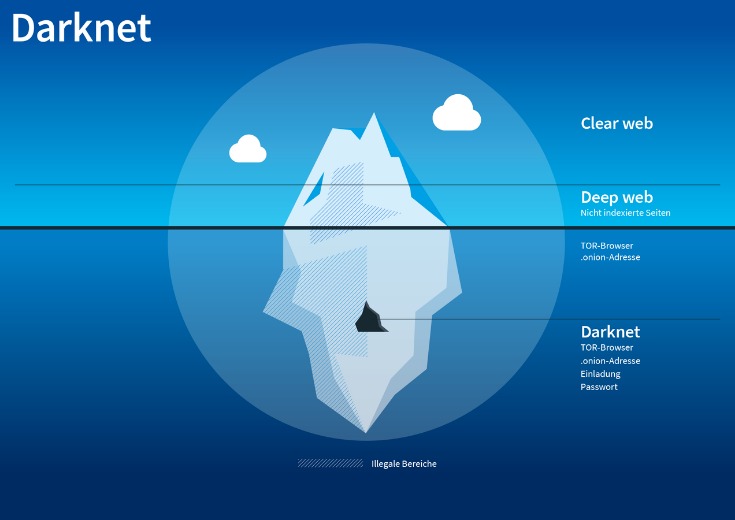
Overview of Darknet Markets on the Onion Network
Darknet markets operating on the Onion Network are part of a hidden internet ecosystem that facilitates the exchange of goods and services beyond traditional online platforms. These markets are accessible via specialized browsers that anonymize user activity, ensuring privacy and security for both buyers and sellers. The darknet markets onion sites provide a decentralized and often clandestine environment where various illicit and legitimate transactions occur. Navigating these markets requires knowledge of how to access them securely and understanding the associated risks and legal considerations. For those interested in exploring more, there are a variety of onion marketplaces, such as Darknet Markets Onion, which serve as hubs for different kinds of exchanges and communities.
Definition and Functionality of Onion Markets
The darknet markets on the Onion Network, often referred to as Onion Markets, are hidden online marketplaces that operate on the dark web using the Tor (The Onion Router) network. These markets provide a platform for the buying and selling of a wide range of goods and services, often including those that are illegal or regulated within certain jurisdictions. The primary purpose of such markets is to maintain anonymity and privacy for both buyers and sellers, making it difficult for authorities to track transactions or identify users.
Onion Markets function by utilizing the unique routing features of the Tor network, which encrypts and redirects internet traffic through multiple servers worldwide. This layered encryption, resembling the layers of an onion, ensures that user identities and locations remain concealed. Transactions within these markets are typically facilitated through cryptocurrencies, notably Bitcoin, which further enhances anonymity and reduces traceability. These markets operate through a web interface that is only accessible via the Tor browser, ensuring that users can access the marketplace securely and privately.
Overall, darknet markets on the Onion Network serve as clandestine hubs for various illicit activities, leveraging the inherent privacy benefits of the Tor system to facilitate anonymous exchanges. While they offer a degree of privacy and security for their users, they also pose significant risks and challenges for law enforcement agencies worldwide due to their hidden nature and the illegal transactions that often occur within these digital undergrounds.
Accessing Darknet Markets via Tor Network
Darknet markets on the Onion Network represent a unique facet of the internet that operates outside the reach of conventional search engines and standard web protocols. These underground marketplaces, accessible exclusively through the Tor network, facilitate a wide range of transactions, both legal and illegal, by providing users with enhanced privacy and anonymity. The Onion Network employs layered encryption techniques, known as onion routing, which allows users to browse and access sites without revealing their identity or location.
Accessing darknet markets via the Tor network requires downloading and installing the Tor Browser, a specialized web browser that enables anonymous communication by routing internet traffic through a volunteer overlay network. Once connected to the Tor network, users can navigate to specific onion addresses, which are a series of alphanumeric characters ending with the “.onion” extension. These addresses are not indexed by standard search engines, making discovery reliant on directories, forums, or trusted referrals within the community.
The darknet markets onion provide a platform for a variety of goods and services, often facilitated through cryptocurrencies such as Bitcoin to ensure financial privacy. Despite the association with illicit activities, some vendors use these markets for legitimate purposes, emphasizing the importance of understanding the technology and risks involved. For users interested in exploring these markets, it is essential to prioritize security measures, verify vendor reputability, and remain aware of the legal implications in their jurisdiction.
Overall, the darknet markets onion exemplify the complex intersection of privacy, technology, and commerce, highlighting the ongoing evolution of online anonymity tools and their impact on digital society. Navigating these markets requires a thorough understanding of the underlying technology and cautious execution to mitigate potential risks associated with their use.
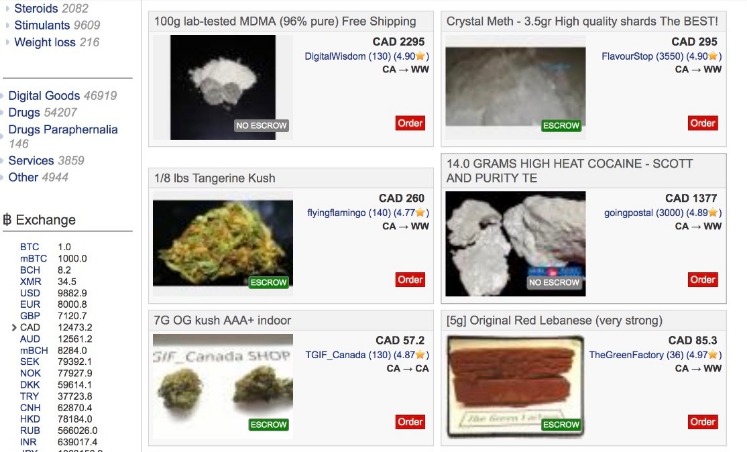
Common Use Cases and Types of Goods Sold
- It should be noted that the real amount of stolen money is higher because the trojanized Tor Browser also alters QIWI wallets.
- Others like Agora and Evolution filled the vacuum left by Silk Road after it was shut down through the efforts of the U.S. government, though since then, these have also been shuttered.
- The Australian Federal Police also mention that identity crime has been a key enabler to ‘organised crime’ which in turn has been costing Australia AUD $15 billion dollars annually.
- The veracity of the information posted is unclear and could easily be falsified.
- The payment is held in escrow by the site operator to discourage scammers.
Darknet markets on the Onion Network represent a segment of the internet that operates beyond the reach of traditional search engines and standard web browsers. These markets access the Deep Web using specialized software like Tor, enabling users to browse anonymously and conduct transactions with a high degree of privacy. The anonymity provided by the Onion Network fosters both legitimate and illicit activities, making it a hub for various online transactions that require discretion.
Common use cases for darknet markets include the buying and selling of a wide range of goods and services that are often inaccessible through conventional channels. These platforms are frequently utilized for purchasing contraband items, such as illegal drugs, weapons, and counterfeit currency. Additionally, they serve as venues for trading stolen data, hacking tools, and other cyber-criminal products. Beyond illicit items, some users access darknet markets for privacy-centric purchases, including certain types of digital content or services that require discretion.
The types of goods sold on darknet markets vary greatly but typically include illicit substances, forged documents, illegal pharmaceuticals, hacking tools, and stolen personal information. Marketplaces often categorize these items to streamline navigation and help buyers find specific products securely. Despite their infamy for illegal trade, these platforms also facilitate various gray-area transactions that operate within the fringes of legal boundaries. Overall, darknet markets on the Onion Network serve as a clandestine marketplace platform for diverse goods and services, often challenging law enforcement efforts to regulate or shut down these activities.
Popular Darknet Marketplaces Operating on the Onion Network
The darknet, often associated with anonymity and clandestine activities, hosts a variety of marketplaces accessible through the onion network. These darknet marketplaces onion sites facilitate the exchange of goods and services that are typically unavailable on conventional platforms. While some markets focus on legal items, many are known for trading illicit products. Despite the risks involved, these marketplaces continue to operate and attract a global user base. Exploring these sites requires caution and an understanding of the underlying technology, which ensures user anonymity and security. To learn more about the structure and functioning of these marketplaces, visit an example darknet market onion site for insights into their operations.
Market Launches and Historical Background
Darknet marketplaces operating on the Onion network have gained significant attention due to their anonymous and encrypted nature, which facilitates the buying and selling of various goods and services outside the reach of conventional law enforcement. These marketplaces typically operate as hidden websites accessible only through specialized browsers like Tor, ensuring user privacy and security. Over the years, they have evolved from small, obscure forums into complex online ecosystems that handle a wide range of transactions, from legal to illicit activities.
The launch of darknet markets on the Onion network can be traced back to the mid-2010s when the rise of cryptocurrencies provided a decentralized and untraceable payment method. Initial platforms emerged with the aim of providing discreet channels for purchasing illicit items, such as drugs, stolen data, and counterfeit currency. As these markets expanded, they developed sophisticated systems for user verification, escrow services, and dispute resolution, mirroring traditional e-commerce models but operating in a concealed environment.
Historically, some of the most well-known darknet markets have experienced rapid growth, frequent closures, and new launches, often driven by law enforcement crackdowns and internal conflicts. Notable cases include markets that have been shut down after authorities discovered their operations, only for new platforms to rise in their place with improved security measures. This ongoing cycle highlights the dynamic and resilient nature of darknet markets on the Onion network. Despite increased legal scrutiny, these marketplaces continue to adapt, leveraging the anonymity of the Onion network to sustain their operations and maintain user trust.
Main Features and Differentiators
Darknet marketplaces operating on the Onion network serve as clandestine digital hubs where a variety of goods and services are traded beyond the reach of traditional online platforms. These marketplaces are accessible through specialized web browsers that provide anonymity and encryption, ensuring privacy for both buyers and sellers. The popularity of these darknet markets stems from their ability to facilitate anonymous transactions and bypass conventional regulatory restrictions.
One of the key features of these darknet markets onion platforms is their emphasis on security and privacy. They typically utilize advanced encryption techniques, multi-layered access controls, and escrow services to protect user identities and financial transactions. Additionally, these marketplaces often operate with decentralized or semi-decentralized structures, which help resist shutdown attempts and maintain operational continuity over time.
Differences among early and modern darknet marketplaces include the range of products offered, user interface design, methods of dispute resolution, and levels of community moderation. Many platforms distinguish themselves through unique features such as reputation systems, integrated messaging tools, or multi-currency support. Some also emphasize particular niches, including illicit drugs, counterfeit documents, or hacking services.
Despite their reputation for illicit activity, these marketplaces also develop features aimed at increasing user safety, such as detailed vendor ratings, secure payment channels, and transparent transaction histories. The evolving landscape of darknet markets on the Onion network continues to adapt strategically to law enforcement efforts, technological advances, and user demand, cementing their role as significant yet controversial components of the internet ecosystem.
Reputation and Trust Mechanisms
Darknet marketplaces operating on the onion network have gained notoriety for facilitating anonymous transactions and trading a wide range of illegal goods and services. These platforms leverage the privacy features of the Tor network, ensuring user anonymity and making it challenging for authorities to track activities. Such marketplaces often function similarly to conventional e-commerce sites but operate exclusively on the dark web, which is accessible only through specialized browsers. The use of onion domains adds an extra layer of security, making it difficult for outsiders to monitor or shut down these sites.
Reputation and trust mechanisms are crucial components in the functioning of darknet markets on the onion network. Because of the illicit nature of many transactions, buyers and sellers rely heavily on review systems, escrow services, and vendor rating platforms to establish credibility. Users often leave feedback based on their experiences, which helps others make informed decisions in an environment where legal recourse is virtually nonexistent. Additionally, trusted vendors who maintain consistent quality and reliable service tend to amass high reputation scores, fostering a sense of reliability within the marketplace community.
Despite the efforts to enforce reputation systems, the dark web remains a risky environment. Many marketplaces implement security measures like PGP encryption for communication and multisignature escrow transactions to mitigate fraud. Nonetheless, the volatile and clandestine nature of these platforms means that trust is largely based on community reputation rather than formal legal protections. This dynamic compels vendors and buyers alike to exercise caution and rely heavily on peer feedback when engaging in transactions on darknet marketplaces operating on the onion network.
Categories of Illegal Goods and Services on Onion Markets
Darknet markets on onion networks serve as clandestine platforms where a wide range of illegal goods and services are exchanged. These underground marketplaces facilitate the trade of items that are prohibited by law, often operating beyond the reach of traditional law enforcement. The categories of illegal goods and services found on onion markets include narcotics, counterfeit documents, stolen data, hacking tools, and illegal weapons. Such markets are characterized by their pseudonymous nature, enabling vendors and buyers to interact with a degree of anonymity. For those interested in exploring more about these clandestine exchanges, various onion sites offer access to diverse marketplaces dedicated to illegal trading activities, such as the darknet markets onion, which demonstrates the range and covert nature of these illicit transactions.
Illegal Drugs and Substances
Darknet markets, often accessed through encrypted networks like Tor, facilitate the anonymous sale and purchase of various goods and services, some of which are illegal. Among the most prevalent illegal categories are goods and services that involve illicit substances. These darknet markets onion platforms have become known for offering a wide range of drugs, including narcotics, stimulants, and hallucinogens, often traded in unregulated and unsafe environments. Such marketplaces operate in a clandestine manner, making enforcement challenging for authorities.
Illegal drugs and substances represent one of the main categories of illicit goods exchanged on these hidden markets. They include prescription medications without prescriptions, controlled substances, and new psychoactive substances that are not yet regulated. The sale of narcotics on darknet markets is a major concern due to the potential for drug abuse, overdose, and the proliferation of illegal laboratories and distribution networks.
In addition to drugs, these markets may also host the trade of other illegal goods and services, such as stolen financial information, counterfeit currencies, and weapons. The anonymous nature of darknet markets onion allows sellers and buyers to operate with minimal risk of exposure, increasing the prevalence of illegal activities. Law enforcement agencies worldwide continue to monitor and target these platforms to curb the spread of illicit substances and other illegal goods in the digital underground.
Stolen Data and Credentials
Darknet markets on the onion network serve as platforms for a variety of illegal goods and services, operating outside the bounds of legal oversight and regulation. Among the categories of illegal items traded are illicit drugs, counterfeit documents, and unlicensed weapons. These markets facilitate transactions that are prohibited by law, often utilizing encryption and anonymity tools to conceal the identities of buyers and sellers. The use of onion sites provides a layer of security, making law enforcement interventions more challenging.
One prevalent category on darknet markets, including onion-based platforms, involves stolen data and credentials. Cybercriminals frequently trade in stolen banking information, social security numbers, credit card details, and login credentials for various online accounts. These items are highly sought after for identity theft, financial fraud, and unauthorized access to digital services. The exchange of such data underscores the significant cybersecurity risks associated with the darknet, where anonymous marketplaces serve as hubs for cybercrime activities.
It is important to understand that these categories of illegal goods and services pose serious legal and ethical concerns. The anonymous nature of onion markets complicates efforts by authorities to track and dismantle these illegal operations. Nevertheless, ongoing enforcement and technological advancements aim to reduce the prevalence of such illicit activities and safeguard digital security for users worldwide.
Counterfeit Items and Documents
Darknet markets, particularly those accessible through the Tor network and often referred to as onion markets, serve as platforms for the exchange of a variety of goods and services, some of which are illegal and pose significant legal and ethical concerns. These markets facilitate transactions that are typically beyond the scope of conventional online commerce, making them a hotspot for the trade of illicit items. As part of their operations, certain categories of illegal goods and services are frequently encountered, highlighting the need for understanding their nature and associated risks.
One prominent category involves the trade of counterfeit items and documents. This includes fake identification cards, passports, driver’s licenses, and other legal documents. These counterfeit items are often used for identity theft, fraudulent activities, or illegal entry into restricted areas, contributing to larger criminal networks. The production and distribution of such counterfeit documents are sophisticated and pose a challenge to law enforcement agencies worldwide.
In addition to counterfeit documents, counterfeit goods themselves are prevalent on onion markets. These include pirated electronic devices, designer clothing, luxury accessories, pharmaceuticals, and software. Such counterfeit goods can be of inferior quality, potentially dangerous, and violate intellectual property rights, causing economic losses for legitimate businesses.
The categories of illegal goods and services commonly found on darknet markets onion include:
- Counterfeit identification documents and legal papers
- Fake pharmaceuticals and unregulated medical products
- Counterfeit luxury goods, clothing, and accessories
- Illegal drugs and controlled substances
- Weapons and ammunition
- Stolen data and hacking services
- Child exploitation materials
- Unlicensed financial services and fraud schemes
Engaging in the trade of these illegal goods and services through onion markets not only involves significant legal risks but also often supports criminal enterprises responsible for various illicit activities. Awareness and vigilance are essential for law enforcement and the public to mitigate the impact of such illicit trade networks on society.
Hacking Tools and Malware
Darknet markets, often accessed through specialized networks like Tor, provide a platform for trading a variety of illegal goods and services. Among the most prevalent categories are banned substances, counterfeit items, and illicit digital products. These markets operate in secrecy to evade law enforcement and regulatory oversight, making them a hub for unlawful activities. A significant concern within these markets is the proliferation of hacking tools and malware, which are frequently sold to facilitate cybercrimes and data breaches.
Hacking tools include software and scripts designed to exploit security vulnerabilities in computer systems, allowing unauthorized access or control. These tools are often marketed on onion markets under the guise of legitimate cybersecurity research but are frequently used maliciously. Malware, on the other hand, encompasses viruses, ransomware, spyware, and other malicious programs intended to compromise or damage devices and networks. Criminals use malware to steal sensitive information, hijack systems for botnets, or ransom data for financial gain.
The illegal goods and services traded on darknet markets contribute significantly to cybercriminal activities, which threaten individual privacy and business security worldwide. The sale of hacking tools and malware is especially alarming, as it lowers the barrier for conducting cyberattacks and increases their sophistication. Efforts to combat these activities involve law enforcement agencies collaborating globally to shut down illicit marketplaces and apprehend those involved. Vigilance and cybersecurity awareness remain crucial for individuals and organizations to protect themselves from these emerging threats.
Security and Anonymity Measures in Onion Markets
Security and anonymity are fundamental concerns for users operating within darknet markets, particularly those accessible through the Tor network. As transactions often involve sensitive or illegal items, it is crucial to implement advanced measures to protect identities and maintain confidentiality. Darknet marketplaces, such as darknet markets onion sites, employ various techniques like encryption, secure communication channels, and decentralized listing systems to safeguard both buyers and sellers. These measures help minimize the risk of detection and prevent malicious activities. For example, utilizing trusted onion services can provide enhanced security and stability, ensuring continued access to marketplaces in the face of potential shutdowns or cyber threats. To explore further, many users turn to dedicated onion sites that prioritize security, such as this popular marketplace, which offers a range of security features to ensure safe trading environments.
Cryptocurrency Transactions
Security and anonymity are paramount concerns for users operating within darknet markets, especially those accessible via onion services. These markets function in a highly sensitive environment where safeguarding user identities and transaction details is crucial to prevent detection and legal repercussions. To achieve this, participants often employ a combination of sophisticated techniques designed to enhance privacy and security.
One of the foundational measures in onion markets involves the use of end-to-end encryption to protect communications between buyers and sellers. This ensures that any exchanged information remains confidential and cannot be intercepted by third parties. Additionally, onion services benefit from the Tor network, which anonymizes IP addresses by routing traffic through multiple relays, making it difficult to trace user activity back to a physical location.
Cryptocurrency transactions, particularly those conducted on darknet markets, are another critical aspect of maintaining anonymity. Users typically prefer privacy-focused coins such as Monero, which offer enhanced features like ring signatures and stealth addresses to obfuscate transaction details. While Bitcoin is still frequently used, it is often mixed through various tumblers or mixing services to break the link between the sender and receiver, further protecting user identities.
Security practices extend beyond technology; users are advised to employ strong, unique passwords for various accounts, enable two-factor authentication where possible, and minimize personal data disclosure. Market operators also implement security measures such as escrow services to hold funds securely until transaction completion, reducing the risk of fraud. Continuous updates to security protocols and vigilant monitoring for potential vulnerabilities help to sustain trust within these hidden marketplaces.
In conclusion, security and anonymity measures in onion markets revolve around a multi-layered approach involving encryption, anonymizing networks like Tor, privacy-centric cryptocurrencies, and strict operational protocols. These strategies collectively aim to create a safer environment for participants amid the risks inherent in the dark web ecosystem.
Encryption and Privacy Protocols
Darknet markets operating on the onion network prioritize security and anonymity measures to protect their users and vendors from legal and external threats. These platforms leverage a combination of advanced encryption methods and privacy protocols to maintain a secure environment for transactions and communications. Ensuring user privacy is central to their design, employing various layers of encryption to obscure identities, transaction details, and activities from potential surveillance or cyber threats.
Encryption forms the backbone of security in these markets, with end-to-end encryption techniques safeguarding all data exchanged on the platform. Communications between buyers and sellers are encrypted to prevent interception, while secure protocols protect sensitive information such as login credentials and transaction details. This layered encryption makes it extremely difficult for outside entities to decrypt or trace activities, thereby enhancing user anonymity.
In addition to encryption, onion routing technology provides an essential privacy protocol within darknet markets. This method routes user data through multiple servers across the network, with each relay adding a layer of encryption, similar to layers of an onion. As data passes through each node, layers of encryption are peeled away, revealing only the immediate destination, which helps conceal users’ IP addresses and locations. This process significantly diminishes the risk of users being tracked or identified by authorities or malicious actors.
Furthermore, these markets often implement robust security practices, including the use of pseudonymous identities, secure login procedures, and multi-layered access controls. Regular security audits and the use of specialized security tools help detect and mitigate potential vulnerabilities. The constant evolution of encryption and privacy protocols ensures that onion markets remain resilient against emerging threats, maintaining a high level of security and anonymity for all participants involved.
Vendor and User Verification Systems
Darknet markets on the onion network operate under a unique set of security and anonymity measures designed to protect both vendors and users. Given the sensitive nature of these platforms, maintaining privacy is paramount to prevent identification and potential legal repercussions. These markets employ a combination of technical safeguards and verification systems to uphold security and ensure trust among participants.
One of the primary security features is the use of the Tor network, which anonymizes user activity by routing communications through multiple servers, making it difficult to trace activities back to individuals. Additionally, many onion markets implement encrypted communication channels and enforce strict data handling protocols to safeguard personal information. Vendors and users are often encouraged or required to use PGP encryption for communications to further enhance privacy.
Vendor verification systems are a critical component in maintaining marketplace integrity. These systems often include multi-layered verification processes, such as identity proof submissions, reputation checks, and escrow services. Some platforms implement a vetting process where new vendors must undergo multiple levels of approval before gaining full selling privileges. This helps reduce fraudulent activities and enhances buyer confidence.
Similarly, user verification measures aim to deter malicious behavior and promote accountability within the marketplace. These may include anonymous account registration with limited information, reputation scores based on transaction history, and feedback systems. Such features incentivize honest interactions and help both vendors and buyers to make informed decisions.
Overall, the security and anonymity measures in darknet markets on the onion network are continually evolving to address emerging threats while striving to protect user identities. While these platforms face significant legal and security challenges, their implementation of robust verification and encryption protocols plays a vital role in providing a safer environment for transactions conducted on these hidden markets.
Protection Against Law Enforcement Actions
Darknet markets operating on the onion network prioritize robust security and anonymity measures to protect both vendors and buyers from external threats and surveillance. These markets utilize the Tor network to conceal IP addresses, ensuring user identities remain hidden and communications are encrypted. Implementing onion routing, which directs traffic through multiple nodes, significantly reduces the risk of digital fingerprinting and tracing attempts by law enforcement agencies or malicious actors.
To enhance security, many darknet markets employ multi-layered encryption protocols for all transactions and communications, making interception and decryption exceedingly difficult. User accounts and marketplace data are often protected through encryption, while access to the platform is restricted via strict authentication processes, including two-factor authentication where available. Regular security audits and prompt updates help identify and mitigate vulnerabilities, maintaining an environment aimed at preserving anonymity and integrity.
Protection against law enforcement actions is a critical concern for operators and users of onion markets. To evade detection and shutdown, markets frequently change domain addresses, utilize decentralized hosting methods, and implement complex operational security practices. Such measures include compartmentalizing operations, using pseudonymous communication channels, and avoiding the collection of personally identifiable information. These strategies collectively help in maintaining the market’s resilience against raids and takedowns by authorities.
Overall, darknet markets onion leverage advanced security and anonymity measures to sustain a clandestine ecosystem. While these techniques provide a degree of privacy, they also underscore the importance of continuous adaptation to evolving security challenges and law enforcement tactics in the digital underground.
Emerging Trends and Developments in Onion Marketplaces
The darknet marketplaces on the onion network are experiencing significant shifts driven by evolving technology, regulatory pressures, and user demand. As digital privacy concerns grow, newer trends such as increased security measures and the adoption of decentralized trading platforms are reshaping how transactions occur within these hidden online environments. The onion realm is constantly adapting to maintain anonymity and security, making it a dynamic space for buyers and sellers alike. Notably, among emerging developments is the rise of specialized marketplaces that focus on niche products and services, reflecting a diversification in offerings. Exploring these trends reveals how darknet markets onion are positioning themselves for future growth and resilience in a rapidly changing digital landscape.
Marketplace Evolution and New Entrants
The darknet onion marketplace landscape is experiencing significant shifts driven by technological advancements, changing user preferences, and evolving regulatory environments. As a hidden segment of the broader online marketplace ecosystem, darknet markets utilizing onion sites continue to adapt to maintain anonymity, security, and efficiency for their users. One notable trend is the increasing sophistication of security protocols and privacy features, which help protect both buyers and sellers from law enforcement efforts and cyber threats.
Marketplaces are also seeing a diversification of products and services offered, expanding beyond traditional illegal commodities to include a wider range of digital and physical goods. This evolution reflects a growing demand from users seeking anonymity in transactions that span various sectors. Additionally, the emergence of new platforms often incorporates advanced features such as decentralized architecture, multi-sig escrow systems, and cryptocurrencies to enhance transaction security and reduce vulnerabilities.
New entrants into the onion marketplace arena are typically driven by the need to fill gaps left by earlier platforms that may have been compromised or shut down. These new marketplaces often emphasize improved user experience, robust security measures, and innovative ways to facilitate access and transactions. As a result, a surge of fresh platforms appears regularly, challenging established players and diversifying the ecosystem.
Overall, the onion marketplace scene continues to evolve rapidly, shaped by technological innovations, user demands, and ongoing efforts to circumvent law enforcement restrictions. The ongoing development of darknet markets onion underscores the importance of staying informed about the latest trends and security practices in this clandestine digital environment.
Technological Advancements and Security Improvements
The darknet marketplace landscape continues to evolve rapidly, driven by emerging trends and technological advancements that enhance user experience and operational efficiency. Among these developments, the prominence of onion-based marketplaces has grown significantly, providing a layer of anonymity and security crucial for users engaging in sensitive transactions. These marketplaces leverage the Tor network to maintain anonymity, making it increasingly difficult for authorities to track activities and identify participants. As technology advances, many darknet markets are integrating sophisticated tools such as encryption protocols and decentralized architectures to improve privacy and resilience against shutdowns.
One of the notable trends is the adoption of blockchain technology and cryptocurrency payment options, which facilitate secure and anonymous transactions while reducing the risk of fund traceability. Innovations like multi-signature wallets and privacy-focused cryptocurrencies further augment transaction security, making it more challenging for third parties to intercept or analyze exchanges. Additionally, improvements in escrow services and reputation systems enhance trustworthiness within these marketplaces, fostering a safer environment for buyers and vendors alike.
Security measures in onion marketplaces are also seeing significant improvements. Developers are implementing advanced cybersecurity protocols, including regular software updates, intrusion detection systems, and multi-layer encryption, to defend against hacking attempts and malware. Furthermore, marketplaces are adopting robust verification processes for vendors and users, reducing fraudulent activities and ensuring compliance with operational standards. These security enhancements are vital in safeguarding sensitive information and maintaining the integrity of darknet markets, which are often targeted by law enforcement and cybercriminals alike.
Overall, the ongoing technological advancements and security improvements in darknet markets, particularly those accessible through onion sites, reflect a commitment to developing more resilient, private, and trustworthy digital spaces. As these markets continue to adapt to changing legal and technological environments, understanding these trends is essential for anyone interested in the evolving landscape of online clandestine commerce.
Shift in Types of Goods and Services Offered
The darknet markets onion ecosystem is continuously evolving, reflecting broader trends in digital commerce and user behavior. As technology advances and cybersecurity measures improve, marketplaces are adopting innovative strategies to enhance user experience and ensure anonymity. One significant trend is the diversification of goods and services offered on these platforms, moving beyond traditional digital goods to include a wider array of products, some of which are legally controversial. This shift is partly driven by user demand for more comprehensive and convenience-oriented shopping experiences, creating a dynamic landscape that adapts rapidly to societal and technological changes.
In recent developments, there has been a noticeable shift in the types of goods and services available on darknet markets onion. These platforms now feature a broader range of products, including pharmaceuticals, digital currencies, and sometimes even physical items such as electronics and luxury goods. The expansion is fueled by vendors seeking new markets and users looking for more diverse options. Additionally, these marketplaces are increasingly integrating innovative payment methods, enhancing privacy, and employing advanced encryption to protect both buyers and sellers from detection.
The growth of privacy-focused tools and the proliferation of secure communication channels have also contributed to the evolution of these marketplaces. As law enforcement agencies intensify efforts to combat illegal activities, marketplace operators are adopting sophisticated security protocols and decentralized models to maintain their operations. This ongoing shift in the darknet markets onion scene demonstrates a resilient digital economy that adapts to external pressures while expanding the scope of offerings. Ultimately, these developments highlight the ongoing transformation of online clandestine markets and their ability to innovate in response to changing technological and legal environments.
Impact of Law Enforcement Operations
Darknet markets operating on onion sites have experienced significant shifts due to emerging trends and recent developments within the industry. As these marketplaces continue to evolve, there is a noticeable increase in the adoption of advanced security measures and anonymity techniques to protect both users and vendors. Innovations such as improved encryption protocols and decentralized marketplaces are shaping the future landscape of these hidden networks, making them more resilient against external disruptions.
Law enforcement operations have played a pivotal role in influencing the dynamics of the onion marketplaces. Increased crackdowns and targeted investigations often result in temporary closures or the seizure of prominent sites. These actions prompt marketplace operators to innovate rapidly, utilizing techniques like site migrations, implementing escrow services, and enhancing operational security. While law enforcement efforts aim to curb illegal activities, they inadvertently accelerate the development of more sophisticated and covert marketplace platforms.
The impact of law enforcement operations extends beyond immediate disruptions, fostering a cycle of adaptation within the darknet ecosystem. Vendors and users tend to migrate to more clandestine platforms, often with improved privacy features, to evade detection. Such developments also lead to a more fragmented market structure, where illicit trade continues but becomes harder to track and regulate. This ongoing tug-of-war underscores the importance of understanding emerging trends and the resilience of onion marketplaces amidst regulatory pressures.
Risks and Threats Associated with Darknet Markets
The darknet markets onion networks pose significant risks and threats to users due to their unregulated and anonymous nature. Engaging with these platforms can expose individuals to legal issues, financial loss, and exposure to illicit activities. The anonymity provided by the darknet makes it difficult to track transactions and identify participants, increasing the likelihood of scams, fraud, and other malicious activities. Users must exercise caution and be aware of these dangers when exploring darknet markets onion regions. Despite the potential for accessing a wide range of goods and services, the risks associated with these activities often outweigh the benefits. Learning about the safety measures and understanding the inherent dangers is crucial for anyone considering engagement in these hidden online spaces.
Fraud and Scams
Darknet markets operating on the onion network present a significant array of risks and threats to users, largely due to their anonymous and unregulated nature. These platforms facilitate the exchange of illegal goods and services, making them attractive for illicit activities. However, engaging with these markets exposes individuals to various forms of financial fraud, scams, and security breaches that can result in substantial losses or legal consequences.
One of the primary threats associated with darknet markets onion is the prevalence of scams. Many vendors and buyers may operate dishonestly, promising products or services that are never delivered or providing counterfeit items. Without a central authority to verify credibility, victims often find it difficult to recover lost funds. Additionally, fraudulent schemes such as fake escrow services or phishing attempts are common, targeting unsuspecting users and leading to financial theft or identity theft.
Financial fraud is another significant concern. Cybercriminals may exploit vulnerabilities in the marketplace or use advanced techniques to steal cryptocurrency transactions, which are the predominant currencies used on these platforms. Once stolen, these digital assets are difficult to trace or recover, especially given the anonymity provided by the onion network. Such risks make engaging in transactions on darknet markets onion inherently dangerous without strict security measures.
Legal risks are also substantial. Authorities worldwide continue to monitor and shut down illegal operations on these illicit platforms. Engaging with darknet markets exposes users not only to monetary loss but also to criminal investigations, potential prosecution, and long-term legal consequences. Furthermore, the lack of regulatory oversight means that user protections are minimal, increasing vulnerability to exploitation and significant legal repercussions.
Security threats extend beyond financial fraud. Users operating on darknet markets face the risk of malware, spyware, and other malicious software designed to compromise their devices and steal sensitive information. Such cybersecurity threats can result in data breaches, unauthorized access to personal information, and increased exposure to further cyberattacks.
In summary, while darknet markets onion can facilitate anonymous transactions, they are fraught with considerable risks and threats. Fraudulent schemes, scams, financial theft, and legal dangers underscore the importance of exercising caution and understanding the inherent perils associated with these clandestine online platforms.
Data Breaches and Leaks
Darknet markets, especially those operating on the onion network, pose significant risks and threats to individuals and organizations alike. These clandestine platforms facilitate the exchange of illegal goods and services, making them a hub for criminal activities. Users often overlook the potential consequences, risking exposure to law enforcement actions and financial losses. The anonymity provided by onion sites can lead to unchecked illegal transactions that might later result in data breaches and leaks.
One of the primary risks associated with darknet markets onion is the possibility of data breaches. Because these platforms operate outside the scope of traditional regulations, they often lack robust security measures. Cybercriminals may exploit vulnerabilities to steal sensitive information, including personal identities, financial details, and transaction histories. Such breaches not only endanger users but can also be used for further criminal activities or blackmail.
Leaks of data originating from darknet markets onion can have far-reaching repercussions. Once information is leaked, it may be disseminated widely, exposing individuals to fraud, identity theft, or targeted attacks. Because these markets thrive on illicit transactions, the data they contain is highly valuable to cybercriminals, who may use it to conduct scams or expand their networks. This perpetuates a cycle of illegal activity, making it difficult for authorities to curb the operational threats posed by these markets.
Furthermore, involvement in darknet markets increases the risk of legal consequences. Authorities worldwide have intensified efforts to dismantle these operations, and many individuals involved have faced criminal charges. The danger is compounded by the potential for malware or phishing schemes used to target unsuspecting users, risking not only legal repercussions but also significant financial and personal harm.
In conclusion, darknet markets onion represent a complex challenge due to their inherent risks and threats. Data breaches and leaks are common issues that can escalate from illegal transactions and expose participants to substantial dangers. Awareness and caution are essential for anyone encountering these hidden corners of the internet, given the serious implications associated with their use and the security vulnerabilities they entail.
Law Enforcement Crackdowns
Darknet markets, particularly those accessible via the onion network, have gained notoriety due to their association with illegal activities and unregulated commerce. While these platforms provide anonymity and facilitate transactions beyond traditional financial systems, they also pose significant risks and threats to users and society alike. The complex structure of darknet markets onion sites makes them attractive for illicit dealings but equally susceptible to law enforcement interventions.
One of the primary risks associated with darknet markets onion is the potential for law enforcement crackdowns. Authorities worldwide have increasingly focused on infiltrating and dismantling these hidden marketplaces. Such operations often result in the seizure of sites, arrest of vendors and users, and significant disruption to illegal trade networks. When crackdown efforts succeed, users may lose access to their funds and data, and vendors face legal consequences.
Beyond law enforcement actions, there are other threats linked to darknet markets on the onion network. These include:
- Fraud and scams: Users often encounter fake vendors or phishing schemes designed to steal personal and financial information.
- Malware and hacking: Some marketplaces may distribute malicious software to compromise users’ devices or steal sensitive data.
- Exposure of personal information: Even with anonymity measures, traces of digital footprints can sometimes lead to identification and legal repercussions.
- Financial loss: Due to the unregulated nature of these markets, buyers and sellers risk losing money through scams or operational failures of marketplaces.
- Legal penalties: Engaging in illicit transactions on darknet markets can result in criminal charges, fines, and imprisonment.
In conclusion, while darknet markets onion facilitate clandestine activities with a degree of privacy, they are fraught with significant dangers. Law enforcement agencies continue to develop sophisticated methods to combat illegal operations on these platforms, increasing the risks for all participants. Awareness of these threats is crucial for anyone considering engagement with darknet markets in order to avoid severe legal and security consequences.
Financial and Personal Security Threats
Darknet markets on the onion network present a complex landscape filled with significant risks and threats, particularly concerning financial and personal security. These markets operate in the shadows of the internet, often facilitating illegal transactions that expose users to various vulnerabilities. Engaging with darknet markets onion sites entails potential dangers that can compromise both financial assets and personal information, making awareness and caution essential for anyone involved.
One of the primary risks associated with darknet markets is financial theft. Cryptocurrency transactions, which are a dominant method of payment on these platforms, are inherently anonymous but not entirely foolproof. Hackers and malicious actors often target users through phishing schemes, scams, or malware, aiming to hijack digital wallets or steal sensitive data. Due to the unregulated nature of these markets, there is little recourse or legal protection for victims, increasing the likelihood of loss.
Personal security threats are equally concerning. Users accessing darknet markets onion sites risk exposing their identities and IP addresses, potentially leading to surveillance, legal action, or blackmail. Law enforcement agencies continuously monitor these platforms, employing sophisticated techniques to identify and apprehend users involved in illegal activities. Mistaken or careless disclosures can have severe consequences, including criminal charges or personal reputation damage.
Furthermore, darknet markets are often rife with scams, counterfeit goods, and malicious software, all of which pose additional threats. Buyers and sellers can fall victim to fraudulent schemes, counterfeit products, or malicious links designed to infect devices or harvest personal data. The risky environment underscores the importance of understanding these dangers before engaging in any activities on the onion network.
Ultimately, operating within darknet markets onion sites carries substantial threats to both financial security and personal privacy. Vigilance, robust security measures, and a thorough understanding of the risks are crucial for anyone considering exploring or participating in these clandestine marketplaces. Staying informed about potential dangers can help mitigate the impact of these threats and promote safer internet practices.
Monitoring and Investigating Onion Marketplaces
Monitoring and investigating onion marketplaces is a critical component in understanding the complex landscape of darknet markets. These hidden online platforms often operate anonymously, making it challenging to track activities and ensure security. By carefully analyzing transaction patterns, withdrawal anomalies, and marketplace behavior, investigators can gain valuable insights into illicit trade and emerging trends. The darknet markets onion domain provides a gateway into these encrypted environments, where illicit goods and services are often exchanged. Enhancing surveillance techniques and deploying sophisticated investigative tools are essential to effectively monitor these marketplaces and address the associated risks.
Methods of Dark Web Monitoring
Monitoring and investigating onion marketplaces on the darknet is a crucial aspect of understanding the clandestine activities and ensuring security within digital ecosystems. These marketplaces operate on the Tor network, making them inherently difficult to track due to their anonymity features. Effective surveillance involves a combination of technical methods and strategic intelligence gathering to identify illicit transactions and gather valuable insights. By consistently monitoring such platforms, authorities and cybersecurity professionals can better comprehend the scope of illegal activities, including those related to black markets, drugs, weapons, and other prohibited items.
Methods of dark web monitoring encompass various techniques, including network traffic analysis, crawl-based approaches, and the use of specialized tools designed to access and scan onion sites. Automated crawlers are tailored to traverse the darknet, capturing data from publicly accessible listings and forums, thus enabling analysts to observe trends and item availability over time. Additionally, behavioral analysis involves examining patterns in vendor activity, transaction frequencies, and communication channels used within these marketplaces. Combining multiple sources of information enhances the accuracy and depth of investigations.
Advanced investigative methods also involve collaboration with law enforcement agencies and cybersecurity firms to develop intelligence on market operators and vendors. Undercover operations and digital forensics play vital roles in uncovering the identities behind these marketplaces and the infrastructure they rely on. Despite the challenges posed by the anonymity of onion sites, ongoing innovation in monitoring techniques continues to improve the ability to detect illegal activities on the dark web and mitigate potential threats related to the onion marketplaces.
Tools and Technologies for Tracking Markets
Monitoring and investigating darknet marketplaces, particularly on the onion network, presents unique challenges for law enforcement, cybersecurity professionals, and researchers. These encrypted markets operate with a focus on privacy and anonymity, making direct observation difficult yet essential for understanding market trends, identifying illegal activities, and combating cybercrime. Utilizing specialized tools and technologies is crucial for tracking transactions, identifying illicit network operators, and gathering intelligence without compromising operational security.
One of the primary methods for monitoring darknet marketplaces involves the use of crawling and scraping tools designed to stealthily collect publicly available data from onion sites. These tools can automate the process of capturing marketplace listings, vendor profiles, and product descriptions, which are then analyzed for patterns or suspicious activity. To maintain anonymity and avoid detection, investigators deploy networks of proxy servers and anonymization services, such as the Tor network, which is fundamental for accessing onion sites securely.
Advanced analytical technologies, including data mining and machine learning algorithms, are increasingly employed to interpret the massive quantities of data generated on these platforms. These technologies can identify trends, detect fraudulent listings, and link vendor accounts across multiple marketplaces. Additionally, digital forensics tools assist in examining seized digital assets and communications, providing deeper insights into the operational structures of darknet markets.
Network monitoring tools, combined with threat intelligence platforms, enable ongoing surveillance of onion marketplaces, alerting investigators to new marketplace launches or significant activity shifts. Furthermore, collaboration among international agencies and private cybersecurity firms enhances information sharing and collective efforts in tracking market dynamics and disrupting illegal operations.
Overall, the integration of advanced technological tools with strategic investigative techniques empowers stakeholders to effectively monitor, investigate, and understand the complex ecosystem of darknet marketplaces on onion networks, contributing significantly to efforts in combatting cybercrime and illegal trade activities online.
Challenges in Monitoring Onion Markets
Monitoring and investigating **darknet markets onion** pose significant challenges due to the inherently clandestine nature of these platforms. These markets operate through encrypted networks, making it difficult for law enforcement and researchers to track activities, transactions, and user behaviors effectively. The use of anonymizing tools like Tor further complicates efforts to gather actionable intelligence, as these technologies are designed to conceal identities and locations.
One primary challenge in monitoring onion marketplaces is the rapid and continuous evolution of market sites. Vendors frequently change addresses, create new platforms, or shift their operations to avoid detection. This constant reorganization hampers efforts to maintain comprehensive and persistent oversight. Additionally, clandestine marketplaces often employ sophisticated encryption and obfuscation techniques to evade automated detection systems and analytical tools.
Investigating activities within these markets demands sophisticated technical capabilities, including cyber forensics, network analysis, and intelligence gathering. However, resource limitations, legal restrictions, and jurisdictional barriers often impede extensive investigations. Moreover, users and vendors in **darknet markets onion** tend to exercise heightened caution, employing cryptocurrency transactions and encrypted communications to preserve anonymity, which further complicates tracing efforts.
Overall, the challenges in monitoring onion marketplaces underscore the need for coordinated efforts, advanced technological solutions, and ongoing adaptation to new tactics by market operators. Despite these obstacles, continuous research and targeted interventions remain essential to disrupt illicit activities and enhance online safety.
Best Practices for Threat Intelligence Gathering
Monitoring and investigating **darknet markets onion** platforms is a crucial aspect of maintaining cybersecurity and law enforcement efforts. These marketplaces often operate anonymously, making it challenging to track illicit activities and gather actionable intelligence. Effective threat intelligence gathering in this domain requires a combination of technical expertise, strategic planning, and adherence to legal frameworks.
Best practices begin with establishing dedicated teams focused on monitoring darknet activities through specialized tools and platforms. These teams utilize advanced scraping and crawling techniques to collect data from onion sites, looking for patterns, new vendors, and emerging trends. Automated systems can help identify suspicious transactions, product listings, or communication channels that may indicate illegal operations.
Additional steps involve cross-referencing collected data with known indicators of compromise and other intelligence sources. Analysts should maintain an updated database of onion marketplace behaviors, transaction methods, and common tools used by vendors. These insights support early detection of potential threats and facilitate proactive intervention.
It is also vital to incorporate human intelligence by engaging with community forums or informants where relevant. Ethical considerations and legal compliance should always guide investigative practices. Regularly updating operational security measures helps prevent exposure or infiltration by malicious actors who are active in **darknet marketplaces onion**.
Overall, a comprehensive approach combining technological solutions, human intelligence, and strict adherence to legal standards enhances the effectiveness of monitoring and investigating these clandestine platforms. This proactive stance is essential in disrupting illegal activities and safeguarding digital ecosystems.