Overview of Darknet Websites
The darknet consists of a hidden network of websites that are not accessible through standard search engines and require specific software or configurations to access. These sites often provide anonymity for both users and operators, making them a unique part of the broader internet ecosystem. Darknet websites are used for various purposes, ranging from privacy protection and secure communications to illicit activities. Due to their secretive nature, understanding how these sites function and the risks involved is crucial for anyone interested in digital security and privacy. For more insights into the structure and usage of darknet sites, visit reputable sources dedicated to internet security.
Definition and Structure
The darknet consists of a hidden part of the internet that is not accessible through standard search engines or browsers. It is often associated with anonymous activity and serves as a platform for various types of communication and transactions that require privacy and confidentiality. Darknet websites are specialized online locations that operate within this concealed network, providing a range of services and information outside the reach of traditional internet infrastructure. These sites are primarily accessed via specific software that ensures anonymity, such as the Tor network or I2P, which obscure user identities and protect their privacy.
The structure of darknet websites differs significantly from regular websites. They are typically designed to be highly decentralized and resilient against detection or shutdowns. These sites often utilize encryption and routing techniques to maintain confidentiality and security. Their architecture may include multiple layers of servers and hidden services that connect through complex onion routing or similar protocols. This structure helps create a secure environment for hosting content, interacting with users, and conducting transactions with a degree of anonymity. Understanding the architecture of darknet websites is essential for grasping how they maintain operational secrecy and serve their specific communities.
Common Domains and Access Methods
The darknet is a part of the internet that is not indexed by traditional search engines and requires specific tools or configurations to access. It is often associated with anonymous browsing and hidden websites that operate outside the regular internet infrastructure. These websites are typically used for various purposes, ranging from private communications to illicit activities. Accessing darknet websites usually involves specialized software and understanding of unique domain structures.
Common domains used for darknet websites often involve the “.onion” extension, which is exclusive to the Tor network, a popular tool for anonymous browsing. These domains are generated through cryptographic processes and do not follow the standard domain registration system, making them difficult to predict or trace. Besides “.onion” sites, some darknet websites may also utilize other obscure domain extensions or IP-based addresses to maintain their anonymity and security.
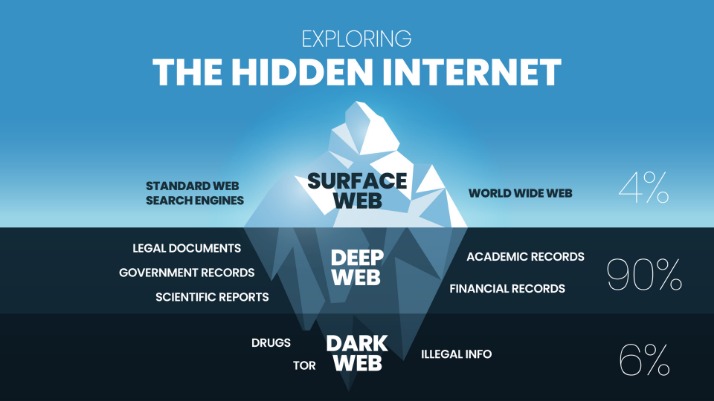
Access methods for darknet websites generally require the use of privacy-focused tools like the Tor Browser or I2P. These tools route internet traffic through encrypted networks, masking users’ identities and locations. Once connected, users can navigate the darknet much like the surface web but must know the specific addresses or directories to find the websites they seek. Due to the nature of the darknet, caution is advised, and proper security measures should be followed to protect identity and data integrity while browsing.
Types of Darknet Websites
Darknet websites are a subset of online platforms that operate on hidden networks, often utilizing anonymity tools like Tor or I2P. These sites are characterized by their encrypted connections and lack of conventional search engine indexing, making them accessible only through specific configurations. Different types of darknet websites serve various purposes, ranging from illicit markets and forums to privacy-focused communication channels. Among these, marketplace platforms and social forums are particularly prominent, catering to diverse user needs. For more insights into darknet activities, visit this darknet directory. Understanding the various types of darknet websites is crucial for grasping the complexities of this hidden part of the internet. These websites often differ significantly in their functions, user base, and security measures, reflecting the multifaceted nature of the darknet itself.
Illicit Marketplaces
The darknet is a part of the internet that is not indexed by traditional search engines and requires special software to access. It is often associated with privacy and anonymity, but it also hosts a variety of websites that serve different purposes, both legitimate and illicit. Understanding the types of darknet websites is essential for comprehending the complex landscape of this hidden network.
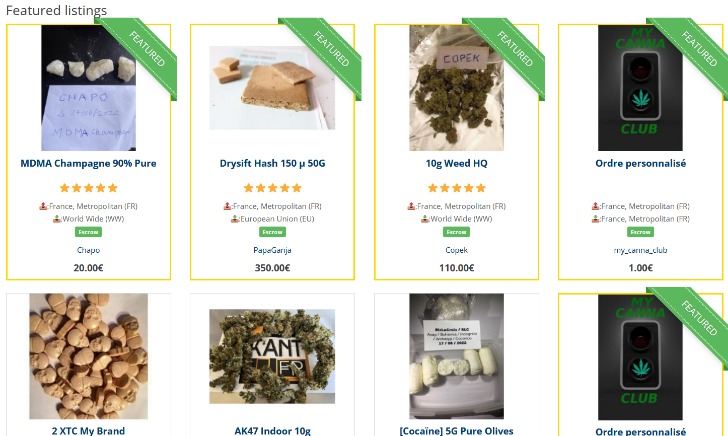
One prominent category of darknet websites involves illicit marketplaces. These marketplaces facilitate the trade of illegal goods such as drugs, firearms, counterfeit currency, stolen data, and hacking tools. Such sites operate with anonymity and security measures to evade law enforcement and maintain user privacy. The presence of these marketplaces contributes to the darknet’s notoriety and highlights the ongoing challenge of combating illegal online activities.
Aside from illicit marketplaces, the darknet also hosts various other types of websites that range from anonymous communication platforms to black markets. Some websites serve as forums where individuals can discuss sensitive topics without fear of censorship or surveillance. Others offer services like untraceable hosting, encrypted messaging, or hacking resources. These sites often prioritize anonymity to protect users involved in activism, journalism, or other activities requiring confidential communication.
Overall, while the darknet contains a mix of legitimate and illegal content, understanding its various website types, especially illicit marketplaces, is vital for awareness and responsible navigation of this concealed segment of the internet. Efforts to monitor and regulate these sites continue as authorities and organizations aim to reduce illegal activities while respecting privacy rights.
Hacking Forums and Cybercrime Sites
The darknet is a hidden part of the internet that requires specific tools and configurations to access. It hosts a variety of websites, some legitimate and others engaged in illegal activities. Understanding the different types of darknet websites is crucial for recognizing potential cyber threats and the scope of cybercrime activity online. Among the most notable are hacking forums and cybercrime sites, which often serve as hubs for malicious activities and illegal trade.
Hacking forums are online communities where threat actors share techniques, tools, and information related to hacking and cybersecurity exploits. These forums often operate pseudonymously and provide a space for hackers to collaborate, exchange malware, and plan cyberattacks. Such platforms can be used for recruiting individuals, buying and selling stolen data, or discussing new vulnerabilities.
Cybercrime sites are more broadly focused on illegal activities and can include marketplaces for buying and selling illicit goods and services. These sites may accommodate activities like drug trafficking, weapons sales, counterfeit currency, or hacking-related services such as phishing kits and malware. Many of these websites are part of the darknet, hidden behind layers of encryption and anonymity tools, making them difficult to track and shut down.
- Darknet marketplaces: These are virtual storefronts where illegal goods and services are bought and sold, often using cryptocurrencies for transactions.
- Hacking forums: Platforms for exchanging hacking techniques, tools, and compromised data, often with a focus on cyber exploits and digital security breaches.
- Cybercrime infrastructure sites: Sites that offer malware, ransomware, or phishing kits, enabling cybercriminals to launch attacks with minimal technical knowledge.
Understanding the environment of darknet websites, including hacking forums and cybercrime sites, is essential for cybersecurity professionals, law enforcement, and organizations working to protect data and infrastructure from malicious actors involved in cybercrime activities.
Encrypted Communication Platforms
The darknet is a hidden part of the internet that requires specialized tools and configurations to access. It hosts various websites that are not indexed by traditional search engines and often operate anonymously to protect the privacy of users and providers. These sites can serve a wide range of purposes, from legitimate activism and privacy protection to illegal activities. Among the most common types of darknet websites are marketplaces, forums, and information portals that prioritize anonymity and security.
Many darknet websites utilize encrypted communication platforms to facilitate anonymous interactions and transactions. These platforms often employ end-to-end encryption, ensuring that messages and data remain private and inaccessible to unauthorized parties. Encrypted communication tools like secure messaging apps and email services are vital components of the darknet ecosystem, allowing users to coordinate and share information securely without fear of surveillance or interception.
Overall, understanding the different types of darknet websites and the encrypted platforms they use is essential for appreciating the complex and secretive nature of this part of the internet. Whether for protecting privacy, exchanging sensitive information, or engaging in illicit activities, these tools and sites play a crucial role in maintaining anonymity in digital communications.
Media and Information Sites
Darknet websites encompass a range of online platforms that operate on encrypted networks, making them difficult to access and trace. These sites are often associated with various activities, some legal and others illegal, and are distinguished by their ability to maintain user anonymity and privacy. Understanding the different types of darknet websites is essential for recognizing their roles within this hidden part of the internet.
One common category within darknet websites is media and information sites. These platforms serve as repositories for news, forums, and discussion groups that focus on topics ranging from activism and privacy to more controversial subjects. Many users gravitate toward these sites to exchange information securely and anonymously, especially when censorship or surveillance is prevalent in their regions. Media and information sites in the darknet often operate under pseudonyms and use encryption technologies to safeguard the identities of their contributors.
Darknet media platforms also include marketplaces, which can range from legal to illicit. These marketplaces facilitate the trade of various goods, including digital products, pharmaceuticals, and other contraband. While some focus on legal transactions, others are associated with illegal activities, such as drug sales or stolen data. The structure and security measures of these sites aim to protect both buyers and sellers while evading law enforcement detection.
Besides marketplace and news sites, darknet websites may host forums and social networks that provide a space for discussion among users who seek to avoid censorship or government oversight. These sites often utilize anonymous login systems and encrypted communications to maintain privacy. They play a vital role for activists, journalists, and individuals in oppressive regimes, offering safe channels for information sharing.
Overall, darknet websites dedicated to media and information play a crucial role in maintaining free expression and access to information in restrictive environments. Their inherent focus on privacy and security makes them an important, though complex, part of the broader cybersphere associated with the darknet.
Legitimate Uses and Ethical Activities
Darknet websites are a subset of websites that operate on overlay networks, providing anonymity and privacy for their users. These sites are often accessed through specialized software such as Tor or I2P, which conceal users’ identities and locations. While some associate darknet websites with illegal activities, many serve legitimate and ethical purposes, contributing positively to various communities and fields.
There are different types of darknet websites, including marketplaces, forums, and information-sharing platforms. Marketplaces on the darknet often facilitate the exchange of goods and services, some of which are legally questionable. However, there are also platforms dedicated to promoting privacy tools, digital rights activism, and secure communications. Forums on these networks might host discussions about technology, privacy rights, and even mental health support, providing valuable resources for users seeking confidentiality.
Legitimate uses of darknet websites include protecting free speech in oppressive regimes, enabling confidential journalism, and facilitating communication for whistleblowers. Attorneys and human rights organizations utilize these platforms to gather and disseminate information securely. Furthermore, researchers and cybersecurity experts monitor darknet activities to uncover malicious behavior and enhance cybersecurity measures. Such activities highlight the importance of the darknet as a tool for good, rather than solely as a venue for illicit conduct.
In addition, ethical activities on the darknet include advocating for privacy rights, offering secure channels for vulnerable populations, and supporting transparency initiatives. Many users value the anonymity these websites provide to share sensitive information without fear of retaliation. As the digital landscape evolves, understanding the varied roles of darknet websites helps promote a balanced view—recognizing their potential for both misuse and meaningful, beneficial applications.
Accessing Darknet Websites
Accessing darknet websites involves navigating a hidden part of the internet that is not accessible through standard search engines or browsers. These sites often operate on the Tor network, providing users with increased anonymity and privacy. Understanding how to access these platforms safely is essential for researchers, journalists, and others seeking to explore this clandestine digital realm. Darknet websites serve a variety of purposes, from secure communication to accessing information that may be censored elsewhere. To explore some of these sites securely, users can utilize specialized tools and protocols designed to maintain anonymity and protect privacy.
Prerequisites: Tor and I2P Browsers
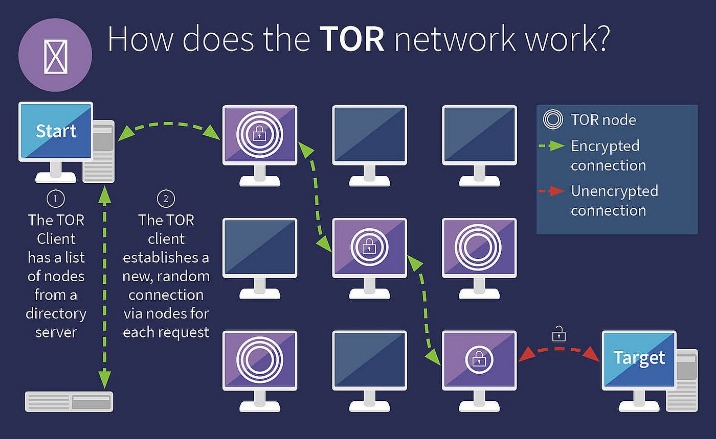
Accessing darknet websites requires careful preparation and the use of specialized browsers designed to ensure user privacy and anonymity. Darknet websites operate on overlay networks that are not accessible through standard web browsers, making it essential to utilize tools like Tor and I2P to navigate these sites securely. These browsers are built to anonymize your internet traffic, preventing third parties from tracking your online activities and safeguarding your identity while exploring the darknet.
Before attempting to access darknet websites, it is crucial to have the necessary tools in place. The Tor browser is a popular choice for accessing the dark web, as it routes your internet connection through a network of volunteer-operated servers, anonymizing your IP address. I2P, or the Invisible Internet Project, provides a similar level of privacy but operates on a different system optimized for hidden services within its own network. Both browsers require proper installation, and users should ensure they download them from official sources to avoid security risks.
Once the appropriate browser is installed, it is advisable to configure security settings and update the software regularly to incorporate the latest security patches. When browsing darknet websites, users should avoid using personal information, be cautious of suspicious links, and understand that the content found within these sites may vary greatly in legitimacy and safety. Using these browsers allows users to access darknet websites while maintaining a high degree of anonymity, which is essential for privacy-conscious individuals or those working within restrictive environments.
In summary, accessing darknet websites safely demands a solid understanding of the prerequisites, including the proper setup of Tor and I2P browsers. These tools are designed to provide anonymous browsing experiences, enabling users to explore the dark web without compromising their identity or security. Proper precautions and updated software are key to enjoying the benefits of darknet websites while minimizing potential risks.
Finding Darknet URLs and Directories
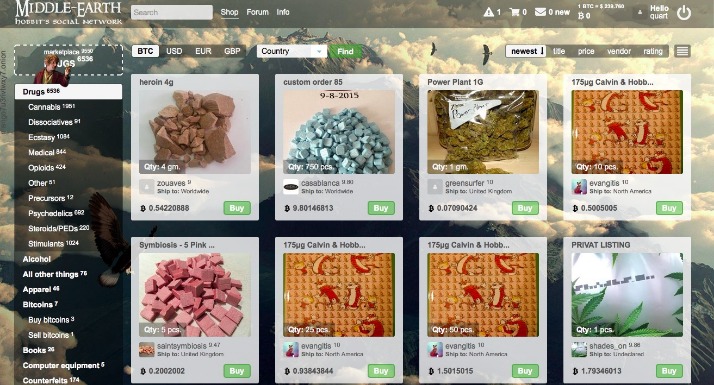
Accessing darknet websites involves navigating a hidden part of the internet that is not indexed by standard search engines and requires specific tools and techniques. These websites often operate on encrypted networks, providing anonymity and secure communication for users. To access these sites, users typically utilize specialized software such as the Tor browser, which allows connection to the dark web through a network of volunteer-operated servers. This setup masks user identities and locations, helping to maintain privacy and security.
Finding darknet URLs and directories can be challenging since they are not publicly listed or indexed. Many darknet sites are shared through private forums, encrypted communications, or word of mouth within specific communities. Users often discover new sites by browsing through onion directories, forums, or specialized platforms that collect and catalog accessible links. It is important to exercise caution and verify the legitimacy of found URLs, as the dark web can also host malicious content or scams.
When exploring darknet websites, it is essential to employ security measures like using reputable VPN services, keeping software updated, and avoiding suspicious links or downloads. Understanding the structure of darknet URLs, which are typically based on the ‘.onion’ domain, can assist in navigation. Nonetheless, always be mindful of the legal and ethical considerations involved, as accessing certain content or services on the dark web may be illegal or pose security risks. Proper knowledge and precautions are key to safely exploring darknet websites and their directories.
Privacy and Security Measures
Darknet websites are part of the hidden areas of the internet that require specialized tools and protocols to access. These sites are often associated with anonymous browsing and are used for various purposes, both legitimate and illegal. Accessing darknet websites involves navigating through a network designed to prioritize user privacy and security, making it essential for users to understand the necessary precautions. Due to the nature of these sites, users must be vigilant about privacy and security measures to protect their identity and sensitive information.
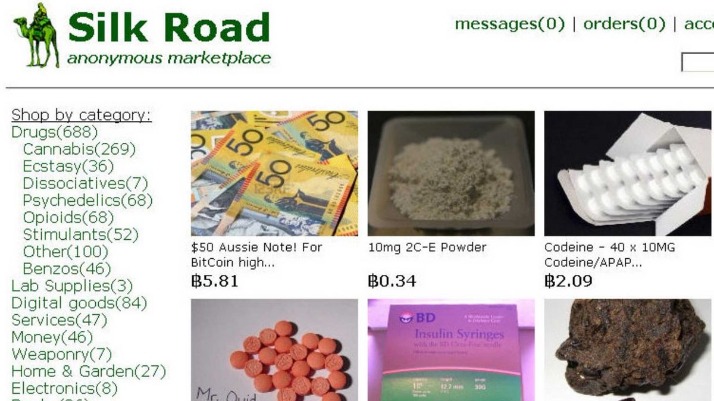
To access darknet websites safely, individuals typically use anonymity networks such as Tor or I2P, which route traffic through multiple layers of encryption, obscuring the user’s IP address and activity. Utilizing these networks helps maintain anonymity and reduces the risk of surveillance or data interception. However, simply connecting to a darknet site does not guarantee safety; users should also employ additional security tools like virtual private networks, secure browsers, and updated antivirus software to mitigate potential threats.
Privacy and security are paramount when exploring darknet websites. It is crucial to avoid sharing personal information or engaging in illegal activities, as these can lead to serious legal and security issues. Users should also ensure they understand the risks of malware, phishing, and scams prevalent in these areas of the internet. Employing strong, unique passwords, keeping all software up-to-date, and exercising caution when clicking links or downloading files can significantly reduce vulnerabilities.
Overall, while darknet websites offer a degree of anonymity, they require responsible and informed use. Implementing robust privacy tools, understanding the risks involved, and adhering to legal boundaries are essential for anyone venturing into these hidden parts of the internet. Prioritizing security and respecting legal guidelines can help users navigate the darknet more safely and effectively.
Risks and Safety Precautions
Exploring the darknet can be both intriguing and perilous, as it involves navigating a hidden part of the internet that is often associated with illegal activities and malicious threats. Understanding the risks and taking appropriate safety precautions are essential to protect oneself from potential dangers. Engaging with darknet websites requires awareness of security measures to avoid personal data theft, malware infections, and other cyber threats. By following proper safety protocols, users can minimize risks while exploring this complex digital environment, ensuring a safer browsing experience on sites such as darknet marketplaces or forums. For those interested in further security tips, visiting specialized resources can provide valuable guidance on safeguarding your identity and devices while browsing sensitive content on the darknet.
Potential Dangers of Dark Web Navigation
Accessing darknet websites can pose significant risks and safety challenges for users. The dark web, frequently associated with anonymity and illegal activities, presents potential dangers that can impact personal security and privacy. Navigating these sites without proper precautions can result in exposure to malicious software, scams, and legal issues.
One of the primary risks involves encountering malware or viruses that can compromise devices and steal sensitive information. Darknet websites often lack the security measures found on standard web platforms, making them attractive targets for cybercriminals. Users may also inadvertently download harmful files or be subjected to hacking attempts during their browsing sessions.
Another significant concern is the potential for scam schemes and fraudulent transactions, especially on darknet marketplaces or forums. These sites may host illegal goods or services, and transactions conducted without safeguards can lead to financial loss or legal repercussions. Law enforcement agencies actively monitor darknet activities, increasing the risk of detection and prosecution for those involved in illicit dealings.
Safety precautions are crucial when exploring darknet websites. Using a secure, updated device with robust antivirus software can help mitigate the threat of malware. Employing a trusted VPN service can also enhance anonymity and prevent tracking. Furthermore, users should avoid sharing personal information and abstain from engaging in illegal activities to reduce legal risks. Awareness of the potential dangers associated with darknet websites is essential to navigate this hidden corner of the internet with caution and responsibility.
Protection Strategies for Users
Exploring darknet websites can expose users to a range of risks that pose significant safety concerns. Due to the anonymous nature of these sites, malicious actors often operate with minimal oversight, increasing the likelihood of encountering illegal activities, scams, or malicious content. Therefore, understanding the associated dangers and implementing effective safety precautions is essential for anyone venturing into these parts of the internet.
To protect yourself when navigating darknet websites, it is crucial to follow several safety strategies:
- Use anonymizing tools: Employ privacy-centric tools such as the Tor Browser to mask your IP address and maintain anonymity while browsing.
- Maintain strong security measures: Keep your device’s operating system and security software up to date to defend against malware and other cyber threats.
- Avoid sharing personal information: Never disclose sensitive details such as your real name, address, or financial information on darknet sites.
- Be cautious of links and downloads: Refrain from clicking unknown links or downloading files, as they may contain malware or phishing schemes.
- Stick to reputable sources: Limit your activities to well-known and trusted sites to minimize exposure to scams or illegal content.
- Use a dedicated device: Consider using a separate device solely for accessing these websites to reduce the risk to your primary system.
- Disable scripts and plugins: Turn off unnecessary scripts, plugins, or JavaScript to prevent exploitation through browser vulnerabilities.
- Monitor your digital footprint: Regularly check for signs of compromise or unauthorized activity on your devices and accounts.
By following these protection strategies, users can significantly reduce their exposure to risks associated with darknet websites. Awareness and cautious behavior are key factors in maintaining safety while exploring these hidden parts of the internet.
Monitoring Personal Data on the Dark Web
Darknet websites are a part of the broader hidden internet, often associated with illegal activities and anonymous exchanges. While exploring or monitoring these sites can provide insights into potential threats, it also involves significant risks. Users should prioritize safety and take appropriate precautions to protect their personal data and avoid legal pitfalls. The anonymous nature of darknet websites makes it easy for malicious actors to exploit unsuspecting visitors or gather sensitive information.
One of the main risks associated with accessing darknet websites is exposure to cyber threats such as malware, phishing scams, or scams designed to steal personal information. Cybercriminals often use these platforms to facilitate illegal transactions, including buying or selling stolen data, drugs, or weapons. Without adequate security measures, personal data like passwords, financial information, or identity details can be compromised, leading to financial loss or identity theft.
- Like the Surface Web, the Dark Web isn’t all about shopping, it also supports informational websites and communities.
- Typically, you can find dark web URLs through forums, databases, or by talking to others who frequent those sites.
- This part of the internet also hosts vast amounts of child pornography, with some websites reaching tens or hundreds of thousands of users.
- Tor is a specially configured browser enabling users to access services on the web in ways that are difficult or impossible to trace.
- Unlike the surface web, you won’t be able to find dark web sites through a search engine.
To ensure safety while navigating or monitoring darknet websites, users should always employ robust security precautions. This includes using a reliable virtual private network (VPN) to anonymize internet traffic, keeping security software up to date, and avoiding the download of suspicious files. It’s also important to use strong, unique passwords and enable two-factor authentication whenever possible. Additionally, using privacy-focused browsers and tools designed for secure browsing can help reduce the risk of exposure.
Monitoring personal data on the dark web can help detect unauthorized use or sale of information. Frequent checks on known data breach sites and monitoring tools can alert individuals if their credentials or personal data appear in illegal marketplaces. However, it is essential to conduct such surveillance carefully and ethically, respecting privacy laws and regulations. Given the risks involved, seeking professional assistance or consulting cybersecurity experts is advisable if there is suspicion of personal data being compromised.
In summary, while darknet websites serve as access points to both legitimate and illegitimate activities, engaging with them requires heightened caution. Protecting personal data and maintaining cybersecurity hygiene are essential steps to mitigate risks. Being aware of the potential threats and following recommended safety precautions can help individuals stay safe in the complex and often hazardous environment of the dark web.
Legal and Ethical Considerations
Legal and ethical considerations are paramount when exploring the realm of darknet websites. These hidden parts of the internet operate outside the boundaries of traditional regulation, raising complex issues related to privacy, security, and morality. Engaging with darknet sites requires an awareness of the legal implications in various jurisdictions, as well as a commitment to ethical conduct to avoid contributing to illegal activities. Understanding these considerations helps ensure responsible navigation through this clandestine online space, especially when encountering sites like darknet websites hubs which often host sensitive or controversial content.
Legal Risks Associated with Darknet Use
Engaging with darknet websites involves navigating complex legal and ethical landscapes. While the darknet offers privacy and anonymity for users, it also presents significant legal risks that individuals must carefully consider. The use of darknet platforms can lead to inadvertent involvement in activities that are against the law, making it essential for users to understand the boundaries of lawful conduct and the potential repercussions of misuse.
Legal risks associated with darknet use are diverse and can have serious consequences. Authorities around the world actively monitor illegal activities on the darknet, such as drug trafficking, illegal arms sales, and the exchange of illicit content. Engaging in or facilitating these activities can result in criminal charges, hefty fines, and imprisonment. Even accessing certain illegal content or services is considered a criminal offense in many jurisdictions, regardless of intent.
It is important for users to recognize that the anonymity provided by darknet websites does not exempt them from legal responsibilities. Law enforcement agencies employ sophisticated techniques to trace illegal activities back to individuals, especially when involving financial transactions or identifiable communication patterns. Conducting illegal activities online can leave digital trails that compromise anonymity and lead to legal action.
Similarly, there are ethical considerations when exploring darknet websites. The platform can be exploited to facilitate harmful activities or exploit vulnerable populations, raising serious moral questions about participation or support. Ethical use of online platforms entails avoiding involvement in activities that could harm others or violate societal norms.
- Understanding and complying with local and international laws related to internet use and online activities.
- Avoiding participation in illegal transactions or content exchanges, especially on darknet websites.
- Being aware that digital footprints can be traced, and authorities can investigate illegal activities despite the use of anonymity tools.
- Considering the moral implications of accessing and sharing sensitive or potentially harmful information on darknet platforms.
- Consulting legal professionals if uncertain about the legality of specific online behaviors to prevent inadvertent violations.
Legitimate Purposes and Cautions
Engaging with darknet websites involves significant legal and ethical considerations that users must thoroughly understand. These platforms often operate beyond the boundaries of conventional regulations, raising concerns about legality, safety, and morality. It is crucial to recognize that while some activities on darknet sites may be legitimate, such as protecting privacy for journalists or activists, many others involve illegal content or transactions. Therefore, users should be cautious and well-informed before exploring these hidden parts of the internet.
Legitimate purposes for accessing darknet websites include safeguarding personal privacy, circumventing censorship, and conducting confidential research. However, it’s important to differentiate between lawful uses and activities that violate laws or ethical standards. Unauthorized transactions, distribution of illicit materials, or engagement in criminal enterprises not only pose legal risks but also damage personal integrity and societal trust. When considering access to darknet sites, users must ensure their intentions align with ethical guidelines and legal frameworks in their jurisdiction.
Practicing caution is essential when exploring darknet websites. Risks such as exposure to malicious content, scams, and malware are prevalent. Moreover, law enforcement agencies monitor illegal activities on these platforms, increasing the risk of legal consequences. It is advisable to avoid engaging in or supporting illicit transactions and to prioritize security measures, such as using reputable tools for anonymity and safeguarding sensitive information. Understanding the boundaries of legal and ethical conduct on the darknet helps in making informed decisions, minimizing dangers, and respecting the rule of law.
Tracking and Monitoring Dark Web Leaks
Tracking and monitoring leaks from the dark web is a critical component in safeguarding sensitive information and maintaining cybersecurity. The dark web hosts numerous clandestine websites and forums where illicit activities, including data breaches and leaks, frequently occur. By employing specialized tools and strategies, organizations can identify potential threats early and respond effectively. Regularly monitoring dark web activity helps in detecting unauthorized disclosures of confidential data, which could otherwise lead to severe consequences. For those interested in exploring darknet websites, resources such as this darknet site offer insights into ongoing activities and potential risks. Ultimately, proactive tracking of dark web leaks is vital for strengthening defenses against cyber threats and protecting digital assets.
Tools and Services for Dark Web Monitoring
Monitoring and tracking leaks on the dark web have become essential components of cybersecurity strategies for organizations and individuals alike. The dark web, with its hidden networks and anonymous marketplace platforms, often hosts stolen data, credentials, and sensitive information, which can lead to significant security breaches if left unchecked. Effective dark web monitoring involves the use of specialized tools and services designed to detect unauthorized disclosures early, enabling proactive responses to potential threats.
Darknet websites, frequently accessed via Tor or other anonymous networks, serve as hubs for illicit activities, including the distribution of leaked data. To combat these threats, numerous tools and services have been developed to scan, analyze, and alert stakeholders about dark web leaks. These solutions continuously search for compromised information, monitor marketplaces, forums, and chat services, and provide comprehensive reports to help organizations understand the scope and nature of their exposures.
Some of the key tools and services used for dark web monitoring include:
- Automated scanning platforms that crawl dark web marketplaces and forums for mentions of specific credentials, data breaches, or sensitive information.
- Real-time alert systems that notify security teams immediately when relevant leaks are detected, minimizing response time.
- Threat intelligence platforms that compile data from various sources on darknet websites to provide contextual analysis and risk assessments.
- Dark web monitoring services that offer continuous surveillance of underground marketplaces, helping track the sale of stolen data related to an organization’s assets or individuals.
- Credential monitoring tools that track compromised login information or personal details appearing in publicly accessible dark web forums.
Implementing these tools helps organizations proactively identify data leaks on darknet websites before they can be exploited. Regular monitoring, combined with prompt incident response, enhances overall security posture and minimizes the potential damage caused by dark web activity. Staying vigilant with advanced tracking and monitoring practices is crucial in the ongoing effort to secure sensitive information against the ever-present threats found within the dark web environment.
Understanding Data Leaks and Personal Identifiers
Darknet websites, often associated with illegal activities, pose significant risks to individuals and organizations through the occurrence of data breaches and leaks. Monitoring these websites is crucial for identifying unauthorized disclosures of sensitive information, which can help in mitigating potential damages. Tracking dark web activity involves using specialized tools and techniques to scan and analyze the content posted on these hidden networks, enabling security teams to detect leaks early and respond effectively.
Understanding data leaks and personal identifiers is essential in the context of darknet websites. Data leaks typically involve the exposure of confidential information such as login credentials, personal identification numbers, financial data, or proprietary business data. When such information is leaked, it can be exploited for identity theft, financial fraud, or cyberattacks. Recognizing the types of personal identifiers often targeted in these leaks—such as names, addresses, email addresses, or social security numbers—helps organizations better prepare and implement countermeasures to protect their data.
Effective strategies for monitoring include utilizing dark web monitoring services that scan various marketplaces, forums, and marketplaces within the darknet. These services can flag compromised data related to an organization or individual, allowing timely intervention. It is also vital to employ continuous monitoring rather than one-time checks, as dark web activity is dynamic and ever-changing. Organizations should establish protocols for responding to discovered leaks, including notifying affected parties, enhancing security measures, and working with law enforcement when necessary.
In conclusion, comprehensively tracking and monitoring dark web leaks is an essential component of a robust cybersecurity strategy. By understanding the nature of data leaks and personal identifiers, organizations can better defend against the threats posed by darknet activities and protect their sensitive information from malicious actors.
Future Trends in Darknet Websites
As technology continues to evolve, so do the methods and platforms used by various online communities, including those operating within the dark web. Future trends in darknet websites suggest a shift toward greater anonymity, sophisticated encryption, and enhanced security measures. These developments aim to improve user privacy while addressing the growing need for secure communication channels for both legitimate and illicit purposes. As darknet websites become more advanced, understanding these emerging trends is crucial for both cybersecurity professionals and users who seek to navigate this complex digital landscape safely and responsibly. Exploring darknet websites such as a prominent darknet site can provide insight into the future of these hidden online networks.
Emerging Technologies and Platforms
The landscape of darknet websites is continually evolving, driven by emerging technologies and shifting platforms that reshape how users access and utilize these hidden networks. As digital privacy and anonymity become increasingly prioritized, innovations in encryption, decentralized architectures, and blockchain integrations are influencing the development of these sites. These advancements facilitate more secure communication channels and enable the creation of resilient, tamper-proof platforms that can operate beyond traditional censorship. In particular, novel tools such as peer-to-peer networks and anonymous hosting services are empowering users to establish and sustain darknet websites with heightened anonymity and reduced risk of shutdowns.
One notable trend is the adoption of blockchain technology to enhance transparency and security within darknet environments. By leveraging decentralized ledgers, new platforms can offer immutable data storage and more robust privacy protections, making it harder for authorities or malicious actors to interfere with operations. Additionally, the integration of artificial intelligence and machine learning is beginning to play a role in moderating content, detecting suspicious activities, and automating security measures, which could significantly influence how darknet websites operate in the future.
Moreover, the expansion of emerging platforms that prioritize user privacy and provide seamless access to darknet services is fueling a dynamic ecosystem. Innovations in encryption protocols, such as end-to-end encryption, are further safeguarding user interactions and transactions. As a result, darknet websites are becoming more sophisticated, offering a broader range of services while maintaining strict anonymity. These technological strides not only alter the landscape for illicit activities but also pose challenges for cybersecurity efforts and regulatory bodies trying to monitor and manage illegal content and transactions.
Overall, future trends suggest that darknet websites will continue to adapt rapidly, embracing cutting-edge technologies to enhance anonymity, security, and resilience. This ongoing evolution underscores the importance of understanding emerging digital tools and their implications for online privacy and security in the dynamic realm of the dark web.
Law Enforcement and Regulation Efforts
Darknet websites continue to evolve rapidly, reflecting both technological advancements and the increasing sophistication of users seeking encrypted and anonymous communication platforms. As the digital landscape shifts, future trends suggest a rise in the use of decentralized hosting solutions and enhanced anonymity tools that make tracking and regulation more challenging. These developments could potentially lead to a broader range of activities on crowded darknet websites, spanning from legitimate privacy-focused services to illicit operations.
Law enforcement agencies are adapting their strategies in response to these changes, leveraging cutting-edge technologies such as artificial intelligence, blockchain analysis, and advanced cyber forensics. These efforts aim to improve the detection and disruption of illegal activities while respecting privacy and civil liberties. Coordination among international agencies is also intensifying, facilitating information sharing and joint operations to combat criminal enterprises that operate on darknet platforms.
Meanwhile, regulatory efforts are incrementally increasing, focusing on creating legal frameworks that deter illegal use of darknet websites without impeding legitimate privacy-enhancing services. This includes developing policies that promote responsible use, establishing clearer guidelines for reporting malicious activities, and fostering collaboration between governments, private sector entities, and cybersecurity experts. As these measures grow more sophisticated, the landscape of darknet websites will likely see a balancing act between technology-driven anonymity and effective regulation.


