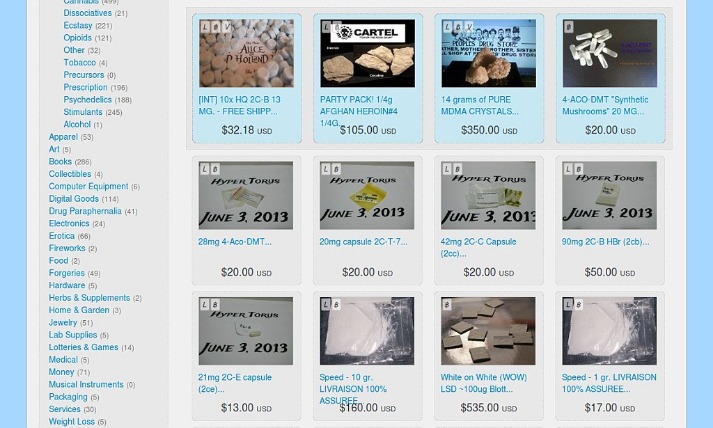
Overview of Dark Market Links
The dark market is a segment of the internet that operates beyond the reach of traditional search engines and law enforcement. It is characterized by anonymous transactions, encrypted communications, and a wide range of illicit activities. Understanding the nature of dark market links is crucial for recognizing how illegal goods and services are accessed and traded online. These links serve as gateways for users seeking such marketplaces, often requiring special software or configurations to access. Visiting dark market links involves significant risks, including legal consequences and cybersecurity threats.
Definition of Dark Web Market Links
The dark market links refer to the web addresses that lead to underground marketplaces operating on the dark web. These links provide access to platforms where illicit goods and services are exchanged, often beyond the reach of conventional law enforcement and regulatory authorities. Such markets are typically accessed through specialized software that anonymizes user activity, ensuring privacy and security for both buyers and sellers.
Dark web market links serve as gateways to concealed online environments where various illegal activities take place. They are often categorized based on the types of products or services offered, including drugs, stolen data, counterfeit documents, and hacking tools. Accessing these links requires users to navigate through anonymization networks, making tracking and regulation challenging. The dark market links are crucial for understanding how illegal transactions are organized and conducted in these hidden digital spaces.
Importance of Monitoring Dark Market Links
The dark market links refer to the encrypted and hidden web addresses used within the dark web environment. These links serve as gateways to underground marketplaces where a variety of illicit goods and services are exchanged. Due to their covert nature, dark market links are often associated with activities such as illegal trading of drugs, counterfeit products, stolen data, and other prohibited items. Monitoring these links is crucial for maintaining cybersecurity and protecting organizational assets from potential threats that originate from or are facilitated through the dark web.
Understanding the importance of monitoring dark market links can significantly enhance a company’s security posture. These links can be used by cybercriminals to plan and execute attacks, acquire stolen information, or distribute malicious software. By keeping an eye on these links, organizations can identify emerging threats early, prevent data breaches, and disrupt illegal activities before they impact broader networks. Additionally, monitoring dark market links helps law enforcement agencies gather intelligence and take action against illicit operations.
- Early Threat Identification: Detecting suspicious activities associated with dark market links allows for prompt response to potential cybersecurity threats.
- Enhanced Security Measures: Recognizing the types of illicit transactions and information exchanged through dark market links aids in developing targeted defense strategies.
- Legal and Compliance Oversight: Monitoring helps ensure compliance with legal standards and reduces the risk of inadvertently engaging with or supporting illegal activities.
- Disruption of Criminal Activities: Proactively tracking dark market links can disrupt ongoing illegal operations and diminish their impact.
- Protection of Reputation and Assets: By preventing cyber threats that stem from dark web activities, organizations safeguard their reputation and valuable assets.
Types of Dark Market Links
Understanding the various types of dark market links is essential for anyone exploring the hidden corners of online trade. Dark market links serve as gateways to clandestine marketplaces where a wide range of goods and services are exchanged outside the reach of conventional regulations. These links often vary depending on the purpose and security measures implemented by the marketplace.
One common type of dark market link is the direct URL to specific marketplaces, which are typically accessed through specialized browsers like Tor. These links can lead to marketplaces offering everything from digital products to illegal substances. Another important category includes hidden service links that obscure the identity and location of the marketplace, providing increased security. For example, some platforms utilize encrypted URLs or onion addresses to maintain anonymity and protect both buyers and sellers. Interestingly, there are marketplaces like dark market link that provide seamless access to various illicit goods, emphasizing the importance of understanding the different link types present in the dark web ecosystem.
By familiarizing oneself with these link types, individuals can better navigate the complexities of dark market environments and recognize the security measures in place. Such knowledge is vital for awareness and caution in these risky online spaces. Exploring the dark market link can provide insights into the mechanics and caution required when engaging with dark web marketplaces.
Internal Links Between Dark Web Marketplaces
Dark market links play a crucial role in the architecture of underground online marketplaces, facilitating access to various illicit goods and services. These links can be categorized into different types based on their purpose and the level of access they provide. Understanding these types is essential for navigating the dark web ecosystem, whether for research or security purposes. One common category is internal links, which connect different sections within the same dark market platform, making navigation seamless for users. These internal links help users find product categories, vendor profiles, and support pages efficiently.
Another significant type is dark market links that interconnect various dark web marketplaces. These links act as bridges, enabling users to move between similar platforms without leaving the underground network. The interconnection of dark web marketplaces through such links can lead to the formation of larger networks or communities, which may share resources, vendors, or products. These internal links between dark web marketplaces are often hidden or obfuscated to avoid detection by authorities and to protect user anonymity. Dark market links of this nature facilitate the expansion and sustainability of illegal marketplaces, making it challenging for law enforcement to dismantle entire networks quickly.
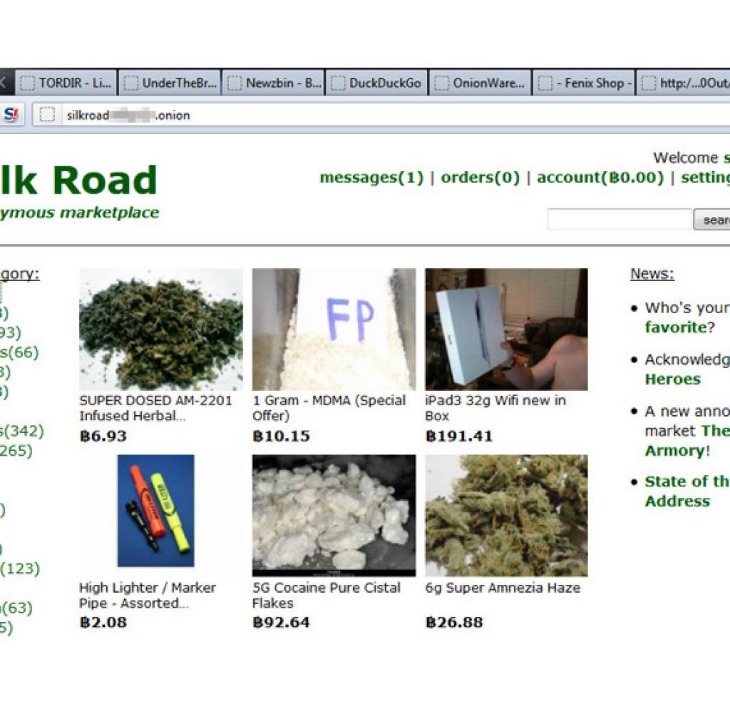
External Links to Illicit Marketplaces
Dark market links refer to URLs that provide access to illicit online marketplaces operating in the shadowy corners of the internet. These links are often used to facilitate illegal trades, including the sale of drugs, stolen data, counterfeit goods, and other prohibited items. Understanding the various types of dark market links is crucial for recognizing their presence and potential risks online.
One common type of dark market link is the direct marketplace link, which takes users to the homepage of a clandestine marketplace. These sites frequently change their addresses to evade law enforcement and detection, but they typically maintain a similar structure known within the community. Accessing these links usually requires specialized software or configurations to anonymize user identity and location.
Another category involves specific product links that lead directly to particular listings, such as a certain amount of stolen credit card information or illegal substances. These links are often shared within forums or encrypted messaging platforms to facilitate discreet transactions. The dark market link associated with these product pages is designed to obscure the nature of the content and protect the seller’s anonymity.
- Users who purchase products can provide feedback ratings on quality, delivery, and service on a scale from 1-5 to further establish vendor credibility.
- In 2021, Hydra accounted for an estimated 80% of all darknet market-related cryptocurrency transactions, and since 2015, the marketplace has received approximately $5.2 billion in cryptocurrency.
- And it also operates without ads, which can be particularly helpful when navigating the dark web.
- The rules section of the site details that the names of Administration accounts are highlighted in red.
- Cazes and his wife amassed numerous high value assets, including luxury vehicles, residences and a hotel in Thailand.
- Some, such as Julia Finess, have become popular and also made a name for themselves on TikTok.
External links to illicit marketplaces can also be embedded within other online content, including hidden sections of forums or encrypted chat groups. These external links serve as gateways for users to access illegal goods and services while maintaining the safety and anonymity of the marketplace operators. Recognizing these links and understanding their structure is essential in mitigating exposure to illicit online activities.
Overall, dark market links come in various forms, each tailored to facilitate anonymous and illegal exchanges. By identifying these link types and understanding how they function, authorities and users alike can better navigate the challenges posed by illicit online marketplaces.
Methods of Accessing Dark Market Links
Accessing dark market links involves various methods, each with its own level of complexity and risk. These methods typically require users to navigate through specialized networks and tools designed to maintain anonymity and security. Understanding these techniques is essential for those exploring the dark web for legitimate research or security purposes. One common approach is using the Tor browser, which enables access to hidden services and dark markets. For example, some users find it helpful to familiarize themselves with various dark market links, such as dark market links, to navigate effectively. Such links are usually hidden behind .onion addresses, necessitating specific tools and knowledge to reach them safely and securely.
Use of Tor and Other Anonymity Networks
Accessing dark market links requires a careful understanding of anonymity networks and privacy tools that facilitate secure and concealed browsing. The most widely used method involves utilizing the Tor network, which anonymizes internet traffic by routing it through multiple servers worldwide, making it difficult to trace user activity back to its origin. By configuring a web browser to connect via Tor, users can visit dark markets while maintaining a higher level of privacy and security.
Aside from Tor, there are other anonymity networks such as I2P and Freenet that cater to specific privacy needs. I2P, for instance, is designed for anonymous communication within a decentralized network, while Freenet emphasizes censorship-resistant free expression. These platforms offer different levels of access and security features, allowing users to choose based on their requirements for accessing dark market links safely.
When attempting to reach dark market links, it’s essential to employ additional security measures such as using a VPN, disabling scripts, and ensuring that operating systems are up-to-date to minimize vulnerabilities. Navigating these hidden marketplaces involves understanding the importance of anonymity and using the right tools to protect one’s privacy during online activities. Proper use of Tor and other anonymity networks plays a critical role in ensuring safer access to dark market links while minimizing exposure to potential threats.
Encrypted Communication Channels
Accessing dark market links and encrypted communication channels involves specialized methods designed to maintain anonymity and security for users. Dark markets operate on the darker regions of the internet, often utilizing anonymizing tools to hide both user identities and the locations of these websites. One common approach is using the Tor network, which allows users to browse anonymously by routing their traffic through a series of volunteer-operated servers. This process effectively conceals a user’s IP address, making it difficult for outsiders to trace activity back to them.
Encrypted communication channels are essential for securely exchanging information within dark markets and related activities. Tools like encrypted messaging apps and PGP (Pretty Good Privacy) provide a layer of security that ensures conversations and data remain confidential. When accessing dark market links, users often combine the use of the Tor browser with encrypted communication platforms to enhance privacy. This approach helps prevent eavesdropping, interception, or surveillance by third parties or authorities.
Overall, utilizing encrypted networks and secure communication methods is vital for those seeking access to dark market links and maintaining their anonymity. By employing tools such as the Tor browser and encryption protocols, individuals can navigate these hidden online spaces with a higher degree of safety. Remember, these methods are designed to protect privacy but also require careful handling to avoid exposure or legal risks.
Common Characteristics of Dark Market Links
Dark market links are often characterized by their clandestine nature and the way they operate outside traditional internet boundaries. These links typically facilitate illegal transactions, including the exchange of illicit goods and services. Recognizing common features of dark market links is essential for understanding their structure and the risks involved. Typically, these links are hidden behind encrypted domains or specialized access points, such as onion addresses that provide anonymity and security. For example, some dark market links are hosted on hidden services that require specific software to access, ensuring user privacy and operation secrecy. As part of their design, these links often aim to evade law enforcement detection and employ various techniques to maintain their anonymity, including sophisticated encryption and decentralized hosting. For illustration, a notable dark market link might be hosted on a specialized darknet platform, accessible only through secure private networks. Understanding the characteristics of these links, such as their use of encrypted domains and anonymous hosting, helps in identifying potential threats and maintaining cybersecurity awareness. You can explore more about dark market links through various resources or trusted underground channels.
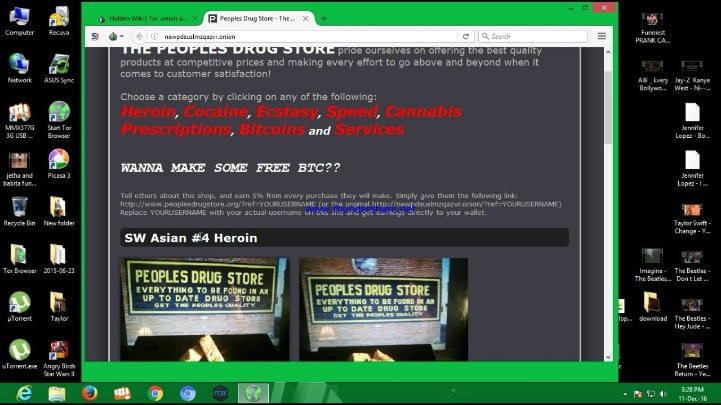
Encrypted URLs and Obfuscated Domains

Dark market links are commonly associated with illicit online marketplaces that facilitate the trade of illegal goods and services. These links often exhibit common characteristics that help distinguish them from legitimate website URLs. One notable feature is the use of encrypted URLs, which employ complex encoding methods to conceal the true destination, making it difficult for browsers and security tools to decipher their intent. Additionally, obfuscated domains are frequently encountered in dark market links, where domain names are intentionally scrambled or disguised using various techniques to evade detection and blacklisting.
Encrypted URLs in dark markets leverage advanced encryption algorithms or encoding schemes, such as Base64 or URL encoding, to obscure the underlying address. This complicates efforts by law enforcement or cybersecurity professionals to track or analyze these links. Obfuscated domains often use random string combinations or mimic legitimate domain patterns, further masking their malicious nature. These domains may also incorporate misspellings or subtle variations in well-known brand names to deceive users and evade filters.
Dark market links tend to be characterized by their short lifespan and frequent changes, as vendors and administrators frequently rotate URLs to avoid detection. They may also utilize domain hopping or rapid DNS updates to maintain covert operations. This dynamic and deceptive use of encrypted URLs and obfuscated domains makes the dark market ecosystem highly resilient and challenging for cybersecurity efforts to monitor effectively.
Recognizing these common traits can assist users and security professionals in identifying potentially malicious links, especially when navigating online marketplaces suspected of illicit activities. Vigilance and understanding of these characteristics are crucial in maintaining safe browsing practices and preventing exposure to harmful content.
Frequent Domain Changes and Mirrored Sites
Dark market links are often characterized by their covert and elusive nature, making them difficult to track and analyze. These links are typically associated with illegal or gray-area activities, and their structures often differ significantly from legitimate websites. One common characteristic is their tendency to frequently change domain names, which helps vendors and users evade detection by law enforcement or security systems. This constant shifting complicates efforts to monitor or block access to these sites, as traditional security measures rely heavily on domain stability.
Another notable feature of dark market links is the presence of mirrored sites. Mirrored sites are duplicates of the original marketplace, created to ensure continued accessibility even if one site is taken down or becomes inaccessible. These mirrored sites often share the same content and layout, but the URLs and server hosting may differ. This redundancy tactic enables vendors to maintain their operations and avoid disruption, contributing to the volatile nature of dark market links.
Additionally, dark market links often exhibit irregular and suspicious URL patterns, which may include unusual strings of characters or subdomains designed to obscure their true purpose. They may also employ techniques such as rapidly rotating domains, use of proxies, or encryption to prevent detection. The combination of frequent domain changes and mirrored sites underscores the adaptive strategies used by operators of these markets to sustain their illegal activities and evade identification.
Tracking Dark Market Links
Tracking dark market links has become an essential aspect of cybersecurity and digital forensics, helping authorities and researchers monitor illicit activities and identify emerging threats. Understanding how these links operate and how they can be traced provides valuable insight into the functioning of clandestine marketplaces. One such example is a dark market link that often appears in investigations, serving as a gateway to illegal transactions and information exchange. For those involved in monitoring dark web activities, tools and techniques that track these links are crucial for maintaining security and preventing criminal enterprises from flourishing. Exploring resources like the dark market link can offer practical insights into the structure and navigation of these hidden networks.
Automated Monitoring Tools for Dark Links
Tracking dark market links is a crucial aspect of cybersecurity and cyber intelligence, as it helps organizations identify and monitor illicit online activities. Dark market links often lead to websites involved in illegal transactions, including the sale of stolen data, counterfeit products, or unauthorized services. Implementing automated monitoring tools enables experts to detect and analyze these links efficiently, reducing the risk of cyber threats and unauthorized access. These tools leverage advanced algorithms and machine learning techniques to continuously scan the dark web for new or emerging links associated with dark markets. By maintaining a vigilant watch over dark market links, security teams can gather actionable intelligence, respond quickly to threats, and enhance their overall security posture. Recognizing the significance of tracking such links is vital in preventing cybercriminal operations and safeguarding sensitive information from falling into malicious hands. This proactive approach to monitoring dark market links fosters a safer online environment and supports the ongoing fight against cybercrime.**
Challenges in Validating Dark Market Links
Tracking dark market links presents significant challenges for researchers and security professionals aiming to understand the scope and operations of illicit online marketplaces. These markets often operate in hidden layers of the internet, using specialized technology to obscure their locations and transactions. The constantly changing URLs, cloaking techniques, and use of anonymizing tools like Tor hinder efforts to monitor and validate these links effectively. This dynamic environment makes it difficult to establish reliable data on the number of active dark market links, their activity levels, or the nature of the content being exchanged.
One primary challenge in validating dark market links is the ephemeral nature of these sites. They frequently shut down or relocate in response to law enforcement actions or internal issues, which leads to a high turnover rate. Researchers must continually update their databases and tracking methods to keep pace with these changes. Additionally, dark market operators often employ techniques such as link obfuscation, encryption, and decoy pages to mislead investigators and prevent accurate analysis of their activities. This deliberate obfuscation complicates efforts to verify the legitimacy and activity status of a given dark market link.
Furthermore, the decentralized and anonymous structure of dark markets hinders standard validation techniques. Many of these sites do not employ traditional security measures, making automated detection difficult, while manual inspection requires significant effort and expertise. The use of multiple layers of access controls and false leads further complicate validation. These challenges underscore the importance of adaptive and innovative methods in tracking dark market links, ensuring that efforts to understand and disrupt these networks are both accurate and effective.
Security Risks Associated with Dark Market Links
Engaging with dark market links poses significant security risks that users often overlook. These underground platforms, such as dark market links, are frequently associated with illegal activities and can expose individuals to various cyber threats. Clicking on or interacting with these links may lead to malware infections, identity theft, or financial loss. One of the primary dangers is the lack of regulation and security standards, which makes it easy for malicious actors to exploit unsuspecting users. For more information on the dark web, visit this comprehensive dark market link to understand the scope of these hidden networks. Protect yourself by remaining cautious and avoiding unnecessary interactions with dark market links, which are often gateways to serious security vulnerabilities.
Exposure to Malware and Phishing
Accessing dark market links can expose users to significant security risks, including exposure to malware and phishing schemes. These illicit platforms often operate outside the boundaries of legal and regulatory frameworks, making them attractive targets for cybercriminals seeking to distribute malicious software or steal sensitive information. Visiting a dark market link may inadvertently lead users to download harmful files or engage with fraudulent pages designed to capture personal data, financial information, or login credentials.
One of the primary dangers associated with dark market links is the high likelihood of encountering malware. Cybercriminals frequently embed malicious code within illegal marketplaces to infect the devices of unwary users. Once infected, devices become vulnerable to further attacks, data theft, or even turning into part of a botnet used for wider cyberattacks. Additionally, phishing attacks are rampant on these platforms, where fake login pages and deceptive communication serve to lure users into revealing their confidential information.
To mitigate these risks, it is crucial to be aware of the dangers associated with accessing dark market links. Users should avoid clicking on suspicious URLs and refrain from sharing personal information on unverified sites. Employing robust security measures, such as updated antivirus software and firewall protections, can help identify and block malicious content. Ultimately, staying vigilant and cautious when navigating online spaces significantly reduces the threat of malware infections and phishing attempts linked to dark market links.
Risks of Illicit Transactions
Dark market links pose significant security risks that can jeopardize users’ digital safety and personal information. These clandestine marketplaces are often associated with illegal activities, including the sale of stolen data, drugs, weapons, and counterfeit goods. Engaging with dark market links can expose individuals to malicious actors, as many sites lack proper security measures and operate outside legal boundaries. Cybercriminals frequently leverage these platforms to distribute malware, which can infect devices and steal sensitive information such as login credentials and financial data.
One of the primary risks of illicit transactions on dark market links is financial loss. Buyers and sellers often operate in an anonymous environment, making it difficult to verify identities or guarantee secure payments. This environment fosters scams, fraud, and non-delivery of goods or services. Additionally, law enforcement agencies actively monitor these markets, increasing the likelihood of legal repercussions for those involved in illegal transactions. Accessing or participating in such activities can lead to severe penalties, including criminal charges and imprisonment.
Furthermore, accessing dark market links increases exposure to scams and malicious software. Many sites may trick users into divulging personal or financial information or trick them into downloading harmful files that compromise their systems. Given the unregulated and deceptive nature of these platforms, users have little recourse if their transactions go awry or if they fall victim to fraud. The risks associated with illicit transactions highlight the importance of steering clear of dark market links to maintain online safety and legal compliance.
Best Practices for Handling Dark Market Links
Engaging with dark market links presents unique challenges and risks that require careful handling and strategic practices. These links often host illicit or sensitive content, necessitating a cautious approach to ensure safety, privacy, and compliance with legal standards. Implementing best practices helps in managing exposure, protecting personal information, and maintaining operational security when navigating these secret marketplaces. Understanding how to handle dark market links effectively can mitigate potential threats and promote responsible engagement in underground ecosystems.
Network Security and Access Control
Handling dark market links requires a strategic approach to ensure network security and access control. These links, often associated with illegal activities, pose significant risks to organizations, including data breaches, malware infections, and reputational damage. Proper management and understanding of these risks are essential for maintaining a secure digital environment.
One of the key best practices is to implement comprehensive network security measures that can detect and block access to known dark market links. This involves deploying advanced threat detection systems, firewalls, and intrusion prevention systems capable of identifying suspicious URLs. Regularly updating security tools ensures they can recognize new and evolving dark market links.
Access control policies are critical in preventing unauthorized access to dangerous links. Establishing strict user authentication protocols and monitoring user activities help restrict access only to authorized personnel. Training employees to recognize the signs of malicious links and educating them about the dangers of dark market links can further reduce risks.
Additionally, organizations should maintain a detailed inventory of known malicious links, including dark market links, and utilize blacklist databases to prevent users from visiting these sites. Monitoring traffic patterns can also help identify unusual activity related to dark market links, enabling quick mitigation measures.
For more targeted control, organizations can utilize web filtering solutions that restrict access based on URL categories. This can include filtering out dark market links and related sites, effectively reducing the attack surface. Regular security audits and vulnerability assessments can help identify potential entry points used by malicious actors exploiting dark market links.
Summary of Best Practices
- Implement advanced threat detection and regularly update security tools.
- Enforce strict access control policies and monitor user activity.
- Maintain and update blacklists of known malicious links, including dark market links.
- Utilize web filtering solutions to restrict access to dangerous sites.
- Conduct regular security audits and user training to recognize and respond to threats.
Handling dark market links effectively is vital for safeguarding digital infrastructure. By combining technical controls with user awareness, organizations can minimize exposure to these dangerous links and uphold a strong security posture.
Regular Updates and Threat Intelligence Integration
Handling dark market links requires a strategic and cautious approach to ensure safety and security. These links often lead to illicit marketplaces that can pose significant risks, including malware, scams, and legal issues. Incorporating best practices for managing such links is essential for maintaining a secure online environment and protecting sensitive information.
One of the key practices is conducting regular updates of security protocols and tools used to monitor and analyze dark market links. This helps identify new threats promptly and adapt defenses accordingly. Staying informed about emerging trends and tactics used by malicious entities in dark markets enables better anticipation and mitigation of potential risks.
Integrating threat intelligence is vital for effective management of dark market links. By leveraging threat feeds, cybersecurity databases, and incident reports, organizations can gain valuable insights into common vulnerabilities and attack vectors. This intelligence supports proactive measures, such as blocking malicious links and alerting users about potential dangers, including dark market links.
Furthermore, maintaining a comprehensive record of interactions with such links, including dates, actions taken, and observed patterns, enhances overall security posture. Collaboration with law enforcement and cybersecurity communities can also aid in tracking and dismantling dark market operations, reducing the threat landscape. Proper handling, regular updates, and threat intelligence integration form a holistic approach to minimizing the risks associated with dark market links.
Legal and Ethical Considerations
Engaging with dark markets raises significant legal and ethical considerations that must not be overlooked. These clandestine marketplaces often operate outside the boundaries of law, posing risks to users and contributors alike. Understanding the legal landscape helps individuals recognize the potential consequences of participation, including criminal charges and civil liabilities. Additionally, ethical issues related to privacy, security, and the morality of engaging in activities that may support illegal operations are critical to consider. It is essential to stay informed about the potential dangers and the importance of adhering to legal standards, especially when exploring or researching dark market links such as dark market link for educational purposes or security assessments. Exploring reputable resources and understanding legal boundaries can help mitigate risks associated with dark market activities and ensure responsible engagement in online security practices. For those interested in safe research, there are resources like this secure link that provide guidance on navigating these complex issues securely and ethically.
Legality of Accessing Dark Market Links
Accessing links related to dark markets involves significant legal and ethical considerations that must be carefully evaluated. Engaging with dark market links can expose individuals to activities that are often illegal, such as the trade of illicit goods or services, which can lead to severe legal consequences. Law enforcement agencies worldwide actively monitor and prosecute individuals participating in these markets, and simply accessing such links may be deemed unlawful depending on the jurisdiction.
From an ethical perspective, exploring dark market links raises questions about complicity in illegal enterprises and the potential for contributing to criminal activities. Viewing or engaging with content on dark market sites can be seen as endorsing or facilitating illicit operations, which conflicts with societal standards and laws designed to prevent harm and maintain order. It is crucial for individuals to understand the risks involved and to avoid engaging with dark market links that may be associated with illegal transactions.
Furthermore, the security risks associated with accessing dark market links, such as exposure to malware or scams, add another layer of concern. These sites often operate outside the bounds of legal oversight, making it difficult to ensure trustworthy transactions or safe browsing experiences. Considering these factors, it is advisable to steer clear of any links associated with dark markets to remain within the bounds of legality and ethical responsibility.
Ethical Responsibilities in Monitoring and Response
Engaging with dark market links raises significant legal and ethical considerations that organizations and individuals must carefully evaluate. Accessing or interacting with dark market links can expose users to illegal activities, including trafficking, unauthorized data exchanges, and the sale of illicit goods and services. Such activities may lead to serious legal repercussions, including criminal charges, fines, and damage to reputation. It is essential to understand that navigating these hidden parts of the internet often involves violating laws and regulations in various jurisdictions.
From an ethical standpoint, operating or even monitoring dark market links requires a balanced approach that prioritizes safety, legality, and moral responsibility. Organizations involved in cybersecurity or law enforcement may seek to monitor dark market links to identify and prevent illegal activities, but this must be done within the boundaries of legal frameworks and with respect for privacy rights. Ethical responsibilities include ensuring that data collection and analysis do not infringe on individuals’ rights or contribute to unlawful activities. Actions taken must align with legal mandates and adhere to principles of responsible reporting, transparency, and due diligence.
Monitoring and response efforts surrounding dark market links should be guided by ethical standards that emphasize integrity and safety. When dealing with dark market links, it is crucial to collaborate with legal authorities and follow established protocols to avoid unintended harm or complicity in criminal operations. Professional awareness and adherence to ethics help ensure that efforts to combat illicit activities are conducted responsibly and effectively, ultimately contributing to the safety and well-being of online communities.