Overview of Dark Markets
Dark markets are clandestine online platforms that operate outside the regular internet infrastructure, facilitating the exchange of goods and services often involving illegal activities. These hidden marketplaces are characterized by their anonymous nature, utilizing encryption and decentralized systems to evade detection by authorities. Participants in dark markets rely on specialized tools and cryptocurrencies to conduct transactions securely and privately. Understanding the structure and operation of these markets is essential for grasping the challenges faced in combating cybercrime and illegal trade on the internet.
Dark markets have evolved rapidly over recent years, expanding their scope and the variety of products available. They serve as hubs for illicit items such as drugs, counterfeit documents, stolen data, and hacking tools. Despite efforts by law enforcement agencies worldwide, these platforms persist due to the advanced methods of anonymity and decentralization used by operators and users. For those interested in exploring further, there are resources available that provide insights into the workings of these markets, although caution and awareness are advised when navigating such environments. Learn more about dark markets and their underlying technologies to understand their impact on digital security and legal frameworks.
Definition and Functionality of Dark Markets
Dark markets are clandestine online platforms that facilitate the exchange of goods and services often outside the bounds of traditional regulation and oversight. These markets operate within the dark web, a part of the internet not indexed by standard search engines and accessible only through specialized software. They are primarily known for hosting transactions involving illegal items, such as drugs, stolen data, counterfeit currencies, and other illicit products.
The primary function of dark markets is to provide a secure and anonymous environment for buyers and sellers to conduct transactions. This anonymity is achieved through the use of encryption technologies and the routing of traffic via the Tor network or similar systems. These mechanisms help both parties conceal their identities and locations, reducing the risk of detection by law enforcement agencies.
Dark markets employ various features to facilitate smooth operations, including:
- Escrow services that hold payments until the buyer confirms receipt of the goods, increasing trust among anonymous users.
- Reputation systems allowing users to rate each other based on transaction experiences, which helps establish credibility within the community.
- Cryptocurrency payments, primarily using Bitcoin or other digital currencies, to ensure financial anonymity.
Overall, dark markets serve as a complex ecosystem that enables illicit trade to thrive in the shadows of the internet, leveraging technology to maintain secrecy and reduce the risks associated with illegal exchanges.
Access Requirements and Technologies Used
Dark markets, also known as darknet or black markets, are clandestine online platforms where individuals can buy and sell goods and services that are often illegal or regulated. These markets operate within the dark web, a part of the internet that is not indexed by conventional search engines and requires specific tools to access. The primary purpose of dark markets is to facilitate anonymous transactions, often involving illicit products such as drugs, stolen data, counterfeit currencies, and weapons.
Access to dark markets typically requires the use of specialized technologies designed to maintain user privacy and security. Most commonly, users utilize anonymous networks like The Onion Router (TOR) to reach these hidden platforms. TOR provides a multilayered encryption system that anonymizes user identities and prevents tracing back to the accessing device. Additionally, many dark markets prefer to use encryption protocols, such as SSL/TLS, to secure communications and ensure the confidentiality of transaction data.
The technologies used in dark markets extend beyond basic anonymization tools. They often employ cryptocurrencies like Bitcoin, Monero, or other privacy-focused digital currencies to facilitate anonymous financial transactions. These digital currencies are preferred because they offer a certain degree of pseudonymity and are designed to be difficult to trace, further enhancing the privacy of participants.
Overall, the combination of anonymity networks, encrypted communication channels, and cryptocurrency transactions creates a resilient environment for dark markets. However, law enforcement agencies continuously work to identify and dismantle these platforms, emphasizing the importance of understanding the technologies and access requirements that underpin their operation. Awareness of these aspects is crucial for comprehending the complex landscape of online illicit trading environments.
Types of Illegal Goods and Services Sold
Dark markets are clandestine online platforms that facilitate the buying and selling of illegal goods and services. Operating within hidden parts of the internet, often accessed through special browsers, these markets are characterized by their anonymity and lack of regulation. Users rely on encryption and cryptocurrencies like Bitcoin to maintain privacy and security, making these platforms difficult for authorities to monitor and shut down.
Within dark markets, various types of illegal goods and services are traded. These include illicit drugs, ranging from controlled substances to synthetic substances, often sold in small quantities for personal use or distribution. Weapons and firearms are also frequently available, providing access to items prohibited by law. Additionally, counterfeit currencies, forged documents, stolen data, and hacking services are common offerings, catering to cybercriminal needs.
These markets also serve as hubs for the sale of illegal services, such as hacking, malware distribution, and illicit hacking expertise. Selling stolen financial information, like credit card details and login credentials for various accounts, is another prevalent activity. The anonymity and security features of dark markets make them attractive to individuals involved in illegal activities who seek to avoid detection and prosecution.
Despite efforts to combat illegal trading on these platforms, their existence poses significant challenges to law enforcement agencies worldwide. The diverse range of illegal goods and services available on dark markets underscores the importance of vigilance and ongoing cybersecurity measures to prevent their proliferation and protect users from engaging in unlawful transactions.
Cryptocurrency as a Preferred Payment Method
Dark markets are clandestine online platforms where goods and services are bought and sold outside the reach of traditional regulation and oversight. These marketplaces typically operate on the dark web, utilizing anonymizing technologies such as Tor to conceal the identities of users and vendors. The anonymity and confidentiality offered by dark markets attract a wide array of illicit activities, including the sale of drugs, weapons, stolen data, and counterfeit documents. Due to their secretive nature, these platforms present significant challenges for law enforcement agencies attempting to combat illegal trade and cybercrime.
In recent years, cryptocurrency has emerged as the preferred payment method within dark markets. Its decentralized and pseudonymous features make it difficult to trace transactions back to individuals, providing a layer of privacy that traditional financial systems cannot easily offer. Cryptocurrencies like Bitcoin and Monero are commonly used, with Monero being particularly favored for its enhanced privacy capabilities. This reliance on digital currencies has helped facilitate smooth and secure transactions on dark markets, further enabling illegal activities to thrive on these platforms.
Despite the efforts to regulate and shut down dark markets, their resilience underscores the persistent demand for anonymity and privacy in illegal commerce. Understanding the dynamics of these markets and the role cryptocurrencies play within them is essential for developing effective strategies to combat illicit online activities and enhance cyber security efforts.
Popular Dark Web Marketplaces
Dark web marketplaces have become a notable part of the underground digital economy, serving as hubs where users can buy and sell a variety of goods and services outside conventional legal channels. These platforms operate in the shadows of the internet, often using encrypted networks to maintain anonymity and security for their users. Many of these dark markets facilitate transactions ranging from simple commodities to more controversial items, attracting a diverse range of participants. Understanding the landscape of these marketplaces is essential for grasping the broader scope of the dark web’s activities and challenges.
Popular dark markets are characterized by their specialized offerings and secretive operations, often functioning on the basis of reputation systems and cryptocurrencies to enable transactions without revealing identities. These platforms are typically accessed via Tor or other anonymizing tools, making them difficult for authorities to monitor. Despite their clandestine nature, some markets have achieved considerable prominence and influence within the dark web ecosystem. For instance, some sites have garnered attention for their extensive product listings and user-friendly interfaces.
- It has gained a reputation for being a reliable source of high-quality data for cybercriminals.
- The volumes shown are monthly and contain all available products on the dark markets.
- This further complicates monitoring efforts because now you need to search for the related Telegram channels and track activity there and on the marketplace itself.
- Dark pools are private exchanges for trading securities that are not accessible to the investing public.
For individuals interested in exploring or understanding these marketplaces further, resources such as dark markets offer insights into their structure and functions. Recognizing the risks associated with engaging in such environments is crucial, as they often host illegal activities and pose significant cybersecurity threats.
Abacus Market: Features and Offerings
Dark markets, also known as dark web marketplaces, are hidden platforms where users can buy and sell a wide range of goods and services outside the reach of traditional regulation. These marketplaces operate on encrypted networks, making transactions private and anonymous. Among the various platforms available, Abacus Market has gained attention for its unique features and offerings, attracting a diverse user base seeking secure and discreet trade options.
Abacus Market is renowned for its user-friendly interface, which simplifies navigation and access for both buyers and sellers. It provides a broad spectrum of product categories, including digital goods, collectibles, and other commodities that are often not readily available through conventional channels. The marketplace emphasizes security by implementing robust encryption protocols and escrow services, ensuring that transactions are completed safely and efficiently.
One of the key features of Abacus Market is its emphasis on privacy. Users can create accounts with minimal information, reducing the risk of identification. The platform also employs advanced authentication methods to protect user identities and transaction integrity. Additionally, Abacus Market offers a variety of payment options tailored to user preferences, including cryptocurrencies designed for anonymous transactions, further enhancing confidentiality.
Offering a reliable shopping experience, Abacus Market maintains strict moderation policies to prevent fraud and counterfeit products. It fosters a community governed by trust, where users can review vendors and share feedback. This community-driven approach helps maintain quality standards and promotes transparency within the marketplace.
As part of the dark markets landscape, Abacus Market continues to evolve, integrating new features aimed at increasing security, usability, and anonymity. It remains one of the notable platforms for individuals seeking discreet online trade, reflecting the ongoing demand for privacy-focused marketplaces in the digital age.
STYX Market: Focus on Financial Cybercrime
The dark web hosts a variety of clandestine marketplaces that facilitate illegal activities, with many specializing in financial cybercrime. These dark markets often serve as hubs for the trading of stolen financial data, hacking tools, and illicit services aimed at compromising bank accounts, credit card information, and other financial assets. One such notable platform is STYX Market, which has gained notoriety for its focus on cybercriminal activities related to financial crimes.
STYX Market provides a marketplace environment where cybercriminals can buy and sell stolen financial information, including payment credentials, credit card dumps, and hacking services designed to target financial institutions. Its reputation stems from its specialized offerings, streamlined user experience, and the active participation of cybercriminals seeking to monetize their illicit activities. The platform’s emphasis on financial cybercrime exemplifies how dark markets have evolved from general illicit marketplaces to highly specialized environments catering to specific fraudulent schemes.
Law enforcement agencies continuously monitor these dark markets to track the flow of stolen financial data and dismantle cybercriminal networks. The prevalence of these marketplaces underscores the importance of robust cybersecurity measures and vigilant financial institutions to prevent the theft and misuse of sensitive financial information. Awareness and proactive security practices are essential in combating the threats posed by dark markets dedicated to financial cybercrime.
Mega Market: Range of Illicit Products
The dark web has become a clandestine marketplace where various illicit activities and products are traded outside the reach of conventional law enforcement. Among these underground platforms, dark markets such as Mega Market are known for offering a wide range of illegal items, attracting a diverse group of buyers and sellers. These marketplaces operate in hidden networks, often accessed through specialized browsers, making them difficult to regulate and shut down.
In dark markets like Mega Market, the variety of illicit products is extensive, covering multiple categories that cater to different illegal interests. Buyers can find everything from drugs, stolen data, and counterfeit documents to weapons and hacking services. The anonymity provided by these platforms facilitates transactions that would be illegal or heavily restricted in the mainstream economy. This environment fosters a thriving black market that challenges traditional law enforcement efforts.
Some of the most common types of products and services available on dark markets include:
- Illegal drugs, including narcotics and psychedelics
- Stolen financial information and personal data
- Counterfeit currency, documents, and identification cards
- Weapons and ammunition
- Hacking tools and services
- Malware and ransomware software
- Black market electronics and gadgets
The existence of dark markets like Mega Market underscores the ongoing challenges faced by authorities worldwide in combating cybercrime and illegal trade. While these platforms provide a space for illicit activities, efforts continue to monitor and dismantle such networks to promote safer and lawful online environments. Awareness and understanding of the scope of these dark web marketplaces are essential for both cybersecurity professionals and the general public in the ongoing fight against cybercrime and organized illegal activities.
Bohemia: Modern Interface and Quality Control
Dark web marketplaces have become a prominent component of the hidden internet, serving as platforms for a variety of goods and services outside the reach of conventional online regulations. These markets often operate on encrypted networks, providing users with anonymity and privacy. Among the numerous dark markets, Bohemia stands out due to its modern interface and a strong emphasis on quality control. Such features enhance user experience and foster trust within the community.
Bohemia’s sleek and user-friendly design makes navigation seamless for both seasoned users and newcomers. This modern interface is a significant departure from traditional dark web markets, which often suffer from cluttered layouts and confusing menus. By prioritizing usability, Bohemia attracts a wider user base while maintaining the necessary security protocols to safeguard transactions and user data.
Another key aspect of Bohemia is its strict quality control measures. In an environment where reliability can vary greatly, ensuring the integrity of products and services is crucial. Bohemia employs rigorous vetting procedures for vendors and actively monitors listings to prevent scams and counterfeit goods. This approach has helped establish a reputation for trustworthiness, setting it apart from less reliable marketplaces that often suffer from high fraud rates.
Overall, the landscape of dark markets continues to evolve, with platforms like Bohemia leading the way through innovation and a focus on quality. These advancements reflect a shift towards more professional and secure environments, catering to users seeking safer and more reliable interactions in the clandestine digital economy.
Cypher Market: Cybercrime Tools and Exploits
The dark web is a hidden part of the internet where illicit activities often take place, facilitated by specialized marketplaces that operate outside the reach of conventional law enforcement. These dark marketplaces serve as hubs for the exchange of illegal goods, services, and cybercrime tools, attracting a wide range of individuals involved in illegal activities. One prominent aspect of this ecosystem is the availability of cybercrime tools and exploits that enable malicious actors to compromise systems, steal data, or conduct cyberattacks.
Among various dark markets, some stand out due to their scale, variety of offerings, and reputation within the cybercriminal community. These marketplaces often feature listings for hacking tools, malware, stolen data, and exploits that can be used to gain unauthorized access to networks or devices. The environment fosters an underground economy, where cybercriminals trade in products and services that can cause significant damage to individuals and organizations.
Cypher Market is one of the notable cybercriminal platforms known for its distinctive focus on cybercrime tools and exploits. It serves as a marketplace for hackers and cybercriminals to buy and sell malicious software, zero-day vulnerabilities, and other hacking resources. This platform provides an environment where malicious actors can find advanced cybercrime tools with relative ease, often fostering collaboration and the sharing of techniques among cybercriminal communities.
- Cybercrime Tools: Cypher Market offers a range of hacking tools, including malware, remote access Trojans (RATs), and phishing kits, which can be used to infiltrate systems and steal sensitive information.
- Exploits and Vulnerabilities: The platform also features zero-day exploits and security vulnerabilities that are highly sought after for their effectiveness in bypassing traditional security measures.
- Stolen Data: In addition to tools, the marketplace sometimes lists databases containing stolen credentials, financial information, and personal data.
These dark markets and platforms like Cypher Market play a significant role in the broader cybercrime ecosystem, enabling malicious actors to operate with relative anonymity. Understanding their operations and the types of services they offer is crucial for organizations and cybersecurity professionals aiming to defend against emerging threats and bolster their security measures.
Russian Market: Stolen Data and Credential Logging
The dark web has become a notorious hub for illegal activities, with various marketplaces operating secretly to facilitate the exchange of illicit goods and services. Among these, certain marketplaces have gained notoriety for their focus on stolen data and credential logging, posing significant threats to cybersecurity and personal privacy. These dark markets often enable cybercriminals to buy and sell stolen personal information, financial data, and login credentials, fueling identity theft, financial fraud, and other malicious activities.
The Russian market, in particular, has established itself as a prominent node for trading stolen data. Cybercriminals within this marketplace specialize in harvesting and distributing sensitive information from various sources, including compromised accounts, data breaches, and malware schemes. This data is then used for a range of nefarious purposes, from blackmail and scams to advanced persistent threats against businesses and individuals alike.
Credential logging remains a core operation within these dark markets. Cybercriminals deploy sophisticated malware and phishing techniques to collect login details, which are then aggregated and sold to other malicious actors. This ecosystem facilitates widespread cybercrime operations, enabling rapid access to valuable accounts and personal information. The proliferation of such activities highlights the need for robust cybersecurity measures and awareness to prevent fall into these traps.
Overall, these dark markets, especially those centered around stolen data and credential logging, pose a significant challenge to online security. Protecting personal information and maintaining vigilant security practices are essential to defend against the threats emerging from these clandestine online spaces.
FreshTools: Credential Leaks and Hacking Resources
The dark web is often associated with clandestine marketplaces that facilitate the trading of illicit goods and stolen information. Among the most discussed platforms are dark markets, which enable vendors and buyers to interact anonymously. These marketplaces often serve as hubs for a variety of illegal transactions, including the sale of narcotics, weapons, counterfeit documents, and compromised credentials.
One notable resource within this illicit ecosystem is FreshTools, a platform that has gained notoriety for providing credential leaks and hacking resources. FreshTools offers hackers and cybercriminals access to a vast array of compromised data, including usernames, passwords, and other sensitive information. These credential leaks are often sold or shared among malicious actors to facilitate identity theft, account compromise, and further cyberattacks.
Dark markets and hacking resource platforms like FreshTools play a significant role in the cybercriminal underground. They not only enable the sale of illicit items but also serve as a hub for exchanging hacking tools, exploits, and other resources that can be used to breach security systems. The proliferation of such platforms highlights the ongoing challenges faced by cybersecurity professionals in combating cyber threats originating from the dark web.
Staying vigilant and employing comprehensive security measures are essential in defending against the risks posed by these dark markets and resources. Organizations and individuals should prioritize protecting sensitive data, using strong authentication methods, and remaining aware of emerging threats linked to illegal online activities on the dark web.
MGM Grand Market: Counterfeit Goods and Financial Data
The dark web hosts a variety of clandestine markets where illegal transactions frequently occur, making it a focal point for law enforcement and cybersecurity experts alike. Among these, some dark markets have gained notoriety for their involvement in the sale of counterfeit goods and compromised financial data, posing significant risks to consumers and businesses. One such marketplace, known as MGM Grand Market, has become infamous for facilitating the trade of counterfeit products, ranging from luxury items to electronics, undermining legitimate industries and consumers’ trust. Additionally, MGM Grand Market also serves as a hub for exchanging stolen financial data, including credit card details and banking information, which can be exploited for financial fraud and identity theft. The existence of these robust and often sophisticated dark markets underscores the importance of vigilant cybersecurity practices and the ongoing efforts of authorities to curb illicit online activities. As these dark markets continue to evolve, staying informed and alert to such criminal enterprises remains essential for safeguarding personal and financial information.

BidenCash: Credit Card and PII Theft
The dark web hosts a range of illicit marketplaces where illegal activities such as the sale of stolen personal information and credit card data are prevalent. These dark markets provide a clandestine platform for cybercriminals to buy and sell sensitive information with relative anonymity, making them a significant concern for cybersecurity and law enforcement agencies. One such notorious marketplace is BidenCash, which has gained notoriety for its involvement in credit card and personally identifiable information (PII) theft. These platforms often operate in the shadows, facilitating the quick exchange of stolen data that can be used for financial fraud, identity theft, and various other cybercrimes.
Dark markets serve as hubs for various illegal transactions, attracting cybercriminals motivated by profit and anonymity. BidenCash, in particular, has been linked to the theft and dissemination of stolen credit card details and PII, enabling fraudsters to exploit compromised accounts for financial gain. These marketplaces often feature user-friendly interfaces and escrow services to ensure secure transactions, making them attractive to a wide range of cybercriminals. Law enforcement agencies continuously monitor these platforms in an effort to dismantle them and curb the spread of stolen data, but the persistent demand for such information sustains their existence.
Understanding the operations and risks associated with dark markets is crucial for individuals and organizations to enhance cybersecurity measures. Awareness of how illegal marketplaces like BidenCash function highlights the importance of protecting personal information, utilizing strong authentication methods, and monitoring financial statements regularly. While these dark web markets are largely hidden from the public eye, their impact can be widespread, resulting in financial losses and severe privacy violations for victims. Continued efforts from authorities and improved cybersecurity practices are essential to combat these illicit activities and reduce their prevalence in the digital landscape.
2easy Market: Breached Data and Cybercrime Services
The dark web hosts a variety of marketplaces that facilitate the exchange of illicit goods and services, often operating beyond the reach of law enforcement. These hidden platforms are known for their anonymity features, which attract cybercriminals and buyers seeking unlawful transactions. Among these, some marketplaces have gained notoriety for dealing with breached data and cybercrime services, making them focal points in discussions about online security threats.
One notable example is 2easy Market, a dark web marketplace that has been associated with the distribution of breached data, including personal information, financial records, and login credentials. Cybercriminals frequently utilize such platforms to buy and sell stolen data, which can be used for identity theft, financial fraud, or further cyberattacks. In addition to data breaches, these marketplaces often offer cybercrime services such as hacking tools, malware, and exploit kits, making them central hubs for orchestrating malicious activities.
The existence of these marketplaces highlights the ongoing challenges faced by cybersecurity professionals and law enforcement agencies trying to combat cyber threats. The dark markets serve as a backbone for many illegal activities, enabling cybercriminals to operate with relative ease and anonymity. Protecting personal and organizational information requires vigilance and proactive security measures to mitigate the risks associated with the activities conducted on these clandestine platforms.
Emerging Trends in Dark Markets
Dark markets have long been a subject of intrigue and concern within the realm of digital commerce. As technology evolves, so do the methods used by illicit entities to operate outside traditional legal frameworks. Recent emerging trends indicate a shift towards more sophisticated, decentralized, and encrypted platforms that challenge law enforcement efforts and reshape the landscape of illegal online trading. These dark markets continue to adapt, leveraging new technologies and economic models to maintain their presence and accessibility in the shadows of the web. For those interested in exploring the latest developments, there are numerous resources and platforms dedicated to understanding and analyzing these hidden ecosystems.
New Market Launches and Growth Patterns
Dark markets, often shrouded in secrecy and accessed through specialized networks, continue to evolve as a significant component of the digital economy. These hidden marketplaces facilitate a wide array of transactions, frequently involving illicit goods and services, yet they also serve as platforms for alternative economic activities beyond traditional financial systems. The emergence of new markets and the shifting growth patterns within this realm reflect ongoing technological advancements and changing user behaviors.
Recent trends indicate the launch of innovative dark markets that leverage enhanced security measures, such as anonymous cryptocurrencies and encrypted communication channels, to attract users seeking privacy and anonymity. These new platforms often differentiate themselves through unique features like decentralized architectures or integrated payment solutions, aiming to minimize risks associated with law enforcement activities.
Growth patterns in dark markets reveal a dynamic landscape characterized by rapid expansion in certain sectors, including digital commodities, hacking services, and counterfeit products. As law enforcement agencies increase crackdowns on recognized platforms, vendors and consumers are quick to migrate to alternative markets, exploiting these disruptions to establish fresh ecosystems. This cyclical shift underscores the resilience and adaptability of dark market participants.
The overall trajectory suggests that *dark markets* will continue to innovate and expand, driven by ongoing demand for privacy and unregulated commerce. Monitoring these trends is crucial for understanding broader cybersecurity threats, economic implications, and the challenges faced by regulatory authorities attempting to stem illicit activities in the digital domain.
Specialization of Markets by Crime Type
Dark markets have become a complex landscape where illegal transactions flourish beyond the reach of traditional law enforcement. One of the notable emerging trends is the increasing specialization of these markets by crime type, allowing vendors and buyers to focus on specific illicit activities. This segmentation enhances operational efficiency and reduces risks for participants, creating distinct niches within the broader dark market ecosystem.
Specialization has led to the development of dedicated platforms for various types of illegal goods and services, such as drug trafficking, counterfeit documents, hacking tools, and stolen data. By concentrating on a particular crime category, these markets can streamline logistics, improve reputation systems, and attract targeted customer bases. This trend makes law enforcement efforts more challenging, as monitoring and dismantling specialized markets requires understanding unique transaction patterns and product flows.
Furthermore, the segmentation by crime type has facilitated innovation within dark markets, including the adoption of crypto payments, escrow services, and reputation management systems tailored to each niche. As a result, these markets continue to evolve, becoming more sophisticated and resistant to disruption. The rise of specialized dark markets underscores the importance of targeted investigative strategies and cybersecurity measures to combat illicit activities effectively.
- Development of dedicated platforms for specific illicit activities such as narcotics, cybercrime tools, and fake identification.
- Enhanced operational security and trust mechanisms within niche markets, making criminal transactions more reliable and harder to intercept.
- Increased complexity in law enforcement efforts, requiring specialized knowledge and tools to monitor and intervene effectively.
- Growth in the use of cryptocurrencies and anonymization techniques to facilitate transactions within these specialized markets.
- Overall trend toward market segmentation fueling innovation and resilience in dark market operations.
Integration of Enhanced Security Measures
Dark markets continue to evolve rapidly, driven by technological advancements and shifting user demands. As these underground platforms expand, they increasingly adopt innovative features to stay ahead of law enforcement and maintain user engagement. One of the most significant emerging trends is the integration of enhanced security measures aimed at protecting users and safeguarding transactions. These security protocols include advanced encryption methods, multi-factor authentication, and sophisticated anonymization techniques that help conceal users’ identities and transaction details. Such enhancements not only increase trust among participants but also complicate efforts to monitor and shut down illegal activities.
Additionally, the incorporation of decentralized technologies, like blockchain, promises to further fortify the security landscape within dark markets. Blockchain’s inherent transparency and immutability provide a double-edged sword, offering both increased security for legitimate uses and new challenges for law enforcement agencies trying to trace illicit operations. Moreover, the use of cryptocurrency payment systems facilitates secure and anonymous transactions, making it harder for authorities to track activity across these platforms.
As dark markets become more sophisticated in their security approaches, there is also a growing emphasis on implementing resilient infrastructure to withstand cyberattacks and operational disruptions. This includes regular security audits, employing cutting-edge cybersecurity tools, and establishing responsive incident management protocols. While these measures aim to enhance safety for users, they also pose significant challenges for regulatory agencies seeking to combat illegal activities. Overall, the integration of advanced security measures signifies a pivotal trend in dark markets, shaping their evolution and presenting new complexities in the efforts to combat illicit online commerce.
Market Saturation and Competition Dynamics
Dark markets have long been a mysterious and rapidly evolving sector within the broader landscape of digital commerce. As technology advances and user behaviors shift, emerging trends in dark markets are reshaping how illicit transactions are conducted and managed. These markets operate largely outside mainstream internet infrastructure, often on encrypted and anonymized platforms, which complicates efforts to regulate and monitor them.
One notable trend is the increasing sophistication of security protocols used by dark market operators. Enhanced encryption, multi-layered authentication, and decentralized marketplaces help protect users’ identities and transactions, making law enforcement efforts more challenging. Additionally, the rise of decentralized exchanges and peer-to-peer networks contributes to the resilience and adaptability of these markets.
Market saturation within dark markets is also a significant factor influencing competition dynamics. As new platforms emerge, they contribute to a fragmented ecosystem with numerous niche markets catering to specific needs. This saturation fosters intense competition among vendors and marketplaces, often leading to price wars and the adoption of innovative marketing strategies to attract users. Meanwhile, the constant threat of scams, scams detection systems, and reputation management further complicates the landscape, encouraging vendors to establish trust through reviews and community engagement.
Furthermore, the competition dynamics are being shaped by technological innovations such as cryptocurrency integration, which provides a swift and anonymous means of payment, and the adoption of digital escrow services that ensure secure transactions. These developments bolster market confidence and facilitate growth, even amid increasing scrutiny from authorities. Overall, the evolving landscape of dark markets reflects a complex interplay of technological advancements, market saturation, and strategic competition, all of which contribute to their resilience and ongoing transformation.
Risks and Threats Associated with Dark Markets
Dark markets, often operating in the shadows of the internet, present a range of significant risks and threats for users and law enforcement alike. These anonymous marketplaces facilitate the trade of illicit goods and services, making them attractive to criminals but also exposing participants to numerous dangers. From financial losses due to scams and fraud to legal repercussions, engaging with dark markets can have severe consequences. Additionally, these platforms often attract cybercriminals who exploit vulnerabilities for their own gain. For those interested in understanding the complexities surrounding these covert exchanges, exploring the ecosystem of dark markets reveals just how pervasive and hazardous they can be.
Financial Fraud and Identity Theft
Dark markets present a significant challenge to the security and stability of the digital ecosystem, as they serve as hubs for illegal activities including financial fraud and identity theft. These clandestine marketplaces operate outside the reach of legal regulations, making them attractive environments for malicious actors seeking to exploit vulnerabilities for personal gain. The anonymity provided by these platforms complicates law enforcement efforts to identify and apprehend offenders, thereby intensifying ongoing threats to individuals and organizations alike.
One of the primary risks associated with dark markets is the proliferation of financial fraud. Criminals often use these platforms to distribute counterfeit currency, launder money obtained through illicit means, or execute scams that deceive unwary users into relinquishing their funds. The lack of transparency and oversight increases the likelihood of fraudulent transactions, which can result in substantial financial losses for victims. Moreover, these activities undermine trust in legitimate financial systems and pose a threat to economic stability.
Identity theft is another grave concern linked to dark markets. Cybercriminals often exchange stolen personal information, such as social security numbers, banking details, and login credentials, on these underground networks. This stolen data can then be used to commit various forms of identity theft, including opening unauthorized accounts, making fraudulent purchases, or engaging in other malicious activities under the victim’s name. The consequences for individuals can be devastating, leading to damaged credit scores and long-term financial hardship.
The risks posed by dark markets are further exacerbated by the complexity of cyber threats and the innovative methods employed by cybercriminals to evade detection. As technology advances, so do the tactics used to commit fraud and steal identities. It is essential for individuals, businesses, and governments to remain vigilant and to implement robust cybersecurity measures to mitigate these dangers. Combating these threats requires a concerted effort to enhance digital security, improve law enforcement capabilities, and promote awareness about the dangers lurking within dark markets.
Cyber Espionage and Data Breaches
Dark markets, often associated with illicit trade and hidden financial transactions, pose significant risks and threats to individuals, organizations, and national security. These clandestine platforms facilitate the exchange of illegal goods and services, making them a lucrative target for cybercriminals. The anonymity provided by dark markets enables malicious actors to operate with little fear of detection, increasing the likelihood of cyber espionage and data breaches.
One of the primary risks linked to dark markets is the potential for cyber espionage. State-sponsored and independent hackers may exploit these platforms to gather sensitive information, Intellectual Property, or confidential data from targeted organizations. Such activities can compromise national security and threaten the integrity of critical infrastructure. Because dark markets often operate beyond the reach of traditional law enforcement, tracing and preventing these attacks becomes particularly challenging.
Data breaches are another grave threat associated with dark markets. Cybercriminals involved in these illegal arenas frequently engage in hacking, phishing, and malware deployment to steal personal and corporate data. Once compromised, this data can be sold or used for financial fraud, identity theft, or further cyber attacks. The proliferation of stolen data on dark markets complicates efforts to secure sensitive information and increases the financial and reputational risks faced by individuals and businesses alike.
Overall, the existence and operation of dark markets significantly elevate the threat landscape in cyberspace. As technology advances, so do the tactics employed by cybercriminals, making it imperative for organizations and individuals to implement robust security measures. Vigilance, continuous monitoring, and proactive cybersecurity strategies are essential to mitigate the risks posed by these hidden marketplaces and safeguard digital assets from cyber espionage and data breaches.
Distribution of Malware and Exploit Kits
Dark markets represent a significant threat vector in the digital landscape, serving as centralized hubs for illegal transactions and the distribution of malicious software. These hidden marketplaces facilitate the exchange of illicit goods such as drugs, counterfeit documents, and malicious tools, making them a major concern for cybersecurity professionals and law enforcement. The anonymous nature of these platforms complicates efforts to track and dismantle cybercriminal operations, contributing to an ongoing cycle of threats across global networks.
One of the key risks associated with dark markets is the proliferation of malware and exploit kits. Cybercriminals leverage these platforms to sell or distribute malicious software tailored to exploit vulnerabilities in target systems. Exploit kits are automated tools that streamline malware deployment by scanning devices for security weaknesses, enabling even less technically skilled actors to compromise systems easily. This widespread availability accelerates the spread of ransomware, data theft malware, and other malicious payloads, resulting in significant financial and data losses for individuals, enterprises, and governments.
The distribution of malware through dark markets often occurs via disguised links, fake software downloads, or compromised legitimate websites. These channels allow criminals to reach a broad audience quickly and discreetly. Moreover, the use of cryptocurrencies on dark markets ensures secure, pseudonymous transactions, further complicating efforts to trace the origin of malicious software and funding sources. This integration of anonymity and automation raises the risk level for organizations and individuals alike, highlighting the need for robust cybersecurity measures.
Furthermore, the trade of exploit kits on dark markets enables attackers to rapidly deploy targeted attacks, often resulting in widespread network compromises. These kits are sold as ready-to-use solutions that can bypass conventional security defenses, making them highly attractive for cybercriminals looking to maximize their impact. The availability of such tools on dark markets significantly lowers the barrier to entry for cyberattacks, increasing their frequency and sophistication. As a result, organizations must prioritize threat intelligence and proactive defense strategies to address these evolving risks.
Counterfeit and Fake Identity Product Risks
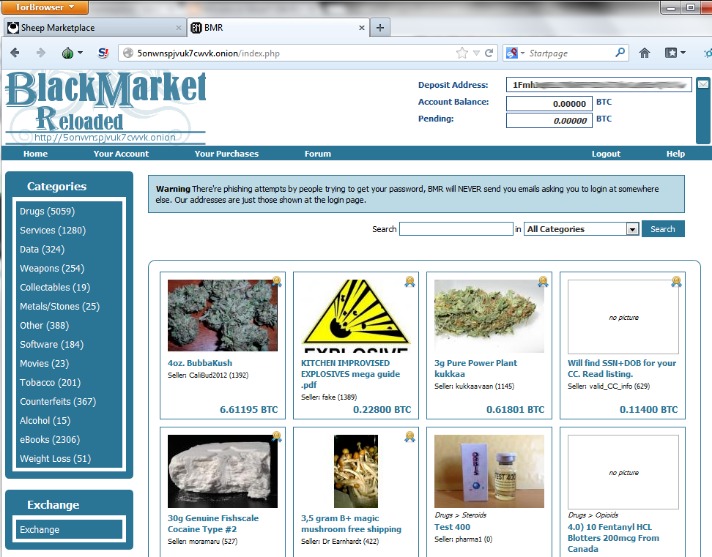
Dark markets pose significant risks and threats to individuals and organizations alike, primarily due to their unregulated and anonymous nature. These platforms often facilitate the trade of illegal goods and services, creating an environment where malicious actors can operate with limited oversight. One of the most pressing concerns associated with dark markets is the proliferation of counterfeit and fake identity products, which can have serious legal and security implications.
Counterfeit items sold on dark markets include a range of products such as luxury goods, pharmaceuticals, software, and electronic components. These counterfeit items often fail to meet safety standards, putting consumers at risk of injury or health complications. Moreover, the sale of fake identity products, such as forged documents, fake IDs, and stolen credentials, can enable criminal activities like fraud, identity theft, and unauthorized access to secure systems. Such counterfeit tools undermine trust and can cause substantial financial and reputational damage to individuals and businesses.
The risks associated with dark markets extend beyond counterfeit goods. Participants often face legal repercussions if caught engaging in illicit activities, and the anonymous nature of these platforms makes law enforcement efforts challenging. Victims of counterfeit products or fake identities may face financial losses, compromised personal information, or even criminal charges in cases of misuse. The threat landscape is continually evolving, with cybercriminals deploying sophisticated methods to conceal their identities and operations.
In conclusion, the presence of dark markets significantly heightens the risks related to counterfeit and fake identity product trades. Awareness and vigilance are crucial for individuals and organizations to avoid falling victim to these threats. Maintaining robust security measures, verifying the legitimacy of products, and staying informed about evolving criminal tactics can mitigate some of these dangers and help combat the illicit activities facilitated by dark markets.
Monitoring and Counteracting Dark Market Activities
Monitoring and counteracting dark market activities have become essential components of maintaining online security and combating illegal transactions. These hidden marketplaces facilitate the trading of illicit goods and services, posing significant challenges to law enforcement and cybersecurity professionals. Implementing effective strategies to identify emerging dark market trends and disrupt their operations is crucial in reducing their impact on society. Continuous surveillance, advanced technological tools, and international cooperation are vital in tracking and dismantling these clandestine networks. For additional insights into online underground economies, visiting specialized resources on dark markets can be beneficial. Ultimately, a proactive approach is necessary to stay ahead of malicious actors operating within these concealed digital spaces.
Automated Dark Web Monitoring Importance
Monitoring and counteracting activities within the dark market are essential components of modern cybersecurity and risk management strategies. As dark markets continue to evolve, they pose significant threats by facilitating illegal transactions, data breaches, and the proliferation of illicit goods and services. Effective surveillance helps organizations identify early signs of malicious activities, enabling timely intervention and mitigation of potential harm.
Automated dark web monitoring tools have become increasingly vital in this effort. These systems utilize advanced algorithms and artificial intelligence to scan, analyze, and alert security teams about suspicious activities across the dark web. By continuously monitoring dark markets, organizations can stay ahead of cybercriminal operations, detect compromised data, and prevent potential exploitation before it occurs.
Implementing comprehensive dark web monitoring not only enhances security posture but also provides valuable insights into emerging threats and hacker trends. This proactive approach helps organizations assess the likelihood of targeted attacks and develop strategic defenses. In an environment where dark markets serve as hubs for illicit activities, automation ensures rapid response times, reduces manual effort, and increases overall detection accuracy, making it a critical element in combating cybercrime.

Threat Intelligence and Early Detection
Monitoring and counteracting activities within dark markets is a critical component of cybersecurity and law enforcement efforts to combat illicit online trade. These hidden marketplaces often facilitate illegal transactions involving drugs, weapons, counterfeit goods, and stolen data, posing significant threats to individuals and organizations alike. To effectively address these challenges, it is essential to develop robust threat intelligence strategies that enable early detection of suspicious activities and emerging trends within these covert environments.
Implementing continuous surveillance and data analysis allows security teams to identify patterns and anomalies indicative of malicious activities. Threat intelligence platforms aggregate information from various sources, including dark market forums, transaction patterns, and user behaviors, providing valuable insights into the operational structures and key players. Early detection mechanisms, such as real-time monitoring and automated alert systems, help organizations respond swiftly to potential threats, minimizing damage and preventing escalation.

Collaborative efforts between private cybersecurity firms, law enforcement agencies, and international organizations are vital in disrupting the infrastructure of dark markets. Sharing intelligence and best practices enhances the collective ability to track illegal transactions and dismantle networks. Advanced analytical tools, including machine learning algorithms, aid in distinguishing legitimate activities from illicit ones, ensuring that intervention efforts are targeted and effective.
Ultimately, a proactive approach combining vigilant monitoring, intelligence gathering, and collaborative enforcement is essential in mitigating the influence of dark markets and safeguarding digital ecosystems. Continued innovation in detection technologies and international cooperation will play a vital role in staying ahead of evolving threats in these clandestine online spaces.
Best Practices for Organizations
Monitoring and counteracting activities within dark markets is essential for organizations aiming to protect their digital assets, reputation, and customer base. These clandestine marketplaces often serve as hubs for illicit trading of stolen data, counterfeit goods, and other illegal products, posing significant risks to both consumers and businesses. Implementing robust detection mechanisms and strategic countermeasures can help organizations mitigate these threats effectively.
Organizations should establish proactive monitoring systems that continuously scan the internet and dark market platforms for mentions of their brand, products, or counterfeit activities. Leveraging specialized tools and threat intelligence feeds enables timely identification of suspicious activities and potential breaches. Maintaining an up-to-date understanding of emerging trends in dark market activities allows organizations to adapt their security measures accordingly.
Engaging in collaboration with law enforcement agencies and industry partners can greatly enhance the ability to disrupt illegal operations. Sharing threat intelligence and best practices with relevant stakeholders fosters a coordinated approach to tackling dark market activities. Additionally, organizations should prioritize employee training to recognize phishing attempts, social engineering tactics, and other methods used by malicious actors operating within dark markets.
Implementing strong cybersecurity measures, such as advanced encryption, secure access protocols, and regular vulnerability assessments, reduces the risk of data breaches that can be exploited in dark markets. It is also crucial to develop comprehensive incident response plans to swiftly address any discovery of illicit activity involving an organization’s assets or intellectual property.
Active enforcement through legal channels, including takedown notices and intellectual property claims, can help remove counterfeit or illicit listings associated with the organization. Regularly auditing digital presence and engaging in brand protection activities also minimizes exposure to dark market activities. Ultimately, a layered approach combining technological, legal, and collaborative strategies forms the best defense against the persistent threats emerging from dark markets.
Legal and Ethical Considerations in Monitoring
Monitoring and counteracting activities on dark markets present complex challenges that require a careful balance between security, legality, and ethical considerations. These clandestine online spaces often facilitate illegal transactions involving illicit goods and services, making vigilance essential for law enforcement agencies, cybersecurity professionals, and ethical investigators. Effective monitoring involves utilizing advanced digital forensics, analyzing transactional patterns, and employing specialized tools to identify suspicious behavior without infringing on individual rights. It is crucial to adhere to legal frameworks to ensure that investigations respect privacy laws and due process, avoiding any breaches that could compromise the integrity of operations.
When tackling dark market activities, maintaining ethical standards is vital. This includes ensuring that intelligence gathering methods do not infringe upon privacy rights or lead to unwarranted violations. Transparency in investigative procedures and a commitment to lawful practices help foster trust and uphold the rule of law. Counteracting these illicit marketplaces often requires collaboration among international agencies, technological innovation, and continuous education on emerging tactics used by dark market participants. Ultimately, a well-rounded approach that combines legal compliance with ethical responsibility is essential for effectively addressing the threats posed by dark markets.