Understanding Dark Web Links
- Additionally, popular culture and media frequently focus on the more illicit aspects of these areas, reinforcing misunderstandings and creating an aura of mystery around all three terms.
- All this activity, this vision of a bustling marketplace, might make you think that navigating the dark web is easy.
- Tor (“The Onion Router”) is free, open-source software initially developed by the U.S. military and designed for anonymous communication.
- Norton 360 Deluxe provides a comprehensive suite of protection that can help block malware and dangerous links in real time, and even detect scams using cutting-edge AI detection.
- And before you dive in, we’ll explain how to use Tor to access the dark web.
The dark web is a hidden part of the internet that requires specific tools and knowledge to access. It is often associated with anonymous activities and is known for hosting a wide variety of content that is not available through standard search engines. Understanding how to navigate and recognize dark web links is essential for anyone interested in exploring this elusive area of the internet. These links often take the form of complex and encrypted URLs, making it challenging to identify safe and legitimate destinations. For example, exploring dark web links can provide insight into the variety of content available, from informational resources to more sensitive material. Knowing how these links are structured and used can help users better understand the nature of the dark web. It is important to exercise caution and ensure the security of your devices when venturing into this part of the internet to avoid malicious sites or illegal content.
Definition and Significance of Dark Web URLs
The dark web is a hidden part of the internet that requires special tools and permissions to access. Central to navigating this shadowy realm are dark web links, which serve as gateways to various sites that are not accessible through conventional search engines. These links are often characterized by unique, complex URLs that differ significantly from regular web addresses, making them easily distinguishable. Understanding the nature of these dark web URLs is essential for anyone interested in exploring or studying this clandestine part of the internet.
Dark web links typically use a specific format, often ending with “.onion,” which signifies their connection to the Tor network or similar anonymity-preserving systems. These URLs are not indexed by standard search engines, which enhances their privacy and security but also makes access more challenging. The significance of these dark web links lies in their ability to connect users to anonymous marketplaces, forums, and information sources that operate outside the reach of conventional authorities. Recognizing and understanding these URLs helps in identifying both legitimate and malicious sites within the dark web environment.
- Unique Structure: Dark web URLs often feature randomized characters, making them difficult to memorize or predict, which adds a layer of security and privacy.
- Identifying the Purpose: While some dark web links lead to illegal activities, others serve legitimate purposes for privacy-conscious individuals, journalists, and activists.
- Security Measures: Accessing dark web links requires specific software and precautions, as these URLs can sometimes lead to dangerous or malicious content.
Given the complexity and the hidden nature of dark web links, it is crucial to approach them with caution and awareness of the risks involved. Proper understanding of these URLs facilitates safer navigation and enhances the ability to distinguish between harmful and valid resource links within this concealed segment of the internet.
Characteristics of Dark Web Links
The dark web is a hidden part of the internet that requires specialized software to access, often associated with anonymous activities and clandestine marketplaces. One of the key features of the dark web is its unique linking structure, which differs significantly from the surface web. Understanding dark web links is essential for navigating this concealed online space securely and effectively.
Dark web links typically have specific characteristics that set them apart from standard websites. These links usually follow a distinctive format, often ending with extensions like .onion. Unlike regular URLs, dark web links are designed to ensure user anonymity and secure communication. They are generated through cryptographic processes, resulting in complex, seemingly random alphanumeric strings that serve as addresses for accessing content within the dark web network.
Another characteristic of dark web links is their non-obvious and non-hierarchical structure. Unlike traditional websites that follow organized link hierarchies, dark web links are often isolated or scattered, making navigation more challenging without proper knowledge or a direct link. This layout enhances privacy and anonymity but also requires users to be cautious and informed when exploring these links.
Furthermore, dark web links are less prone to accidental discovery because they are not indexed by standard search engines. Instead, access relies heavily on direct sharing of links or specialized directories, which can encapsulate the mysterious and clandestine nature of the dark web. Recognizing these characteristics can help users identify authentic dark web links and understand their inherent privacy-centric design.
Differences Between Surface Web and Dark Web URLs
The dark web is a hidden part of the internet that is not indexed by traditional search engines and requires special software to access. Understanding dark web links is essential for navigating this secret realm safely and securely. These links, often ending with the “.onion” domain, are designed to provide anonymity for users and hosting sites alike. Unlike regular web links, dark web URLs are typically complex and not human-readable, making them difficult to remember or share easily.
In contrast, the surface web refers to the part of the internet that is accessible through standard search engines and web browsers. These URLs are straightforward, typically containing recognizable domain extensions such as .com, .org, or .net. Surface web links are easily accessible, and their information is intended for general public use. The key difference between surface web and dark web URLs lies in accessibility, purpose, and the level of anonymity they provide.
While surface web links are designed for open access and transparency, dark web links prioritize privacy and confidentiality. The dark web’s unique URLs are often generated generically or through specific services meant to keep users anonymous. Navigating between these two types of web addresses requires understanding their structure and purpose, especially for those interested in exploring the dark web safely. It is crucial to exercise caution when dealing with dark web links, as they can lead to content that is illegal or unsafe. Always ensure proper security measures and awareness when accessing or sharing dark web links to protect your identity and data.
Identifying Dark Web Links
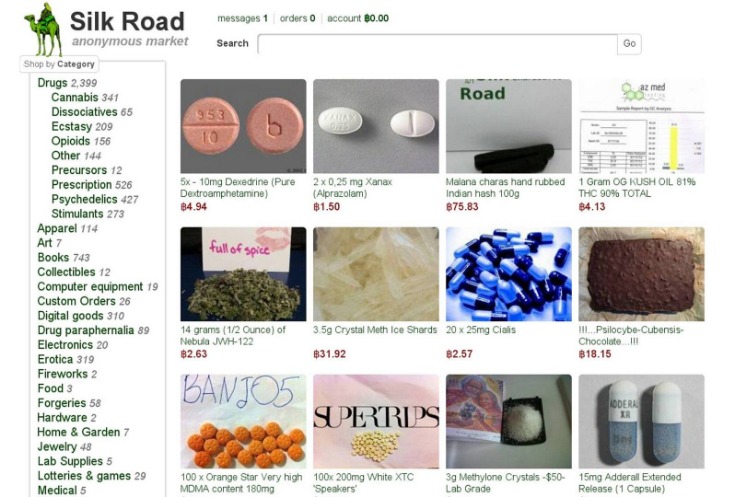
Identifying dark web links is a crucial step for individuals and organizations aiming to navigate the hidden corners of the internet safely and effectively. The dark web is composed of encrypted websites that are not accessible through standard search engines and often require specialized tools to access. Recognizing these links involves understanding their unique .onion domain suffix and the specific methods used to access them. For example, one such dark web link can be found at Nexusafe. Proper identification of these links helps ensure secure browsing, protects user privacy, and avoids malicious sites that could compromise security. As the dark web continues to expand, staying informed about how to spot authentic dark web links remains essential for anyone exploring this concealed part of the internet.
Common Domain Extensions: .onion
Identifying dark web links is crucial for navigating and understanding the hidden layers of the internet. One of the most distinctive features of these links is their domain extension, which often signals a connection to the dark web environment. The most common domain extension associated with dark web links is .onion. These specialized addresses are not accessible through standard web browsers and require the use of dedicated software like the Tor Browser to access content hosted on the dark web. Recognizing a dark web link typically involves noting its unique structure; .onion domains are usually comprised of a string of random characters followed by the extension, making them easily distinguishable from conventional website addresses. While these links serve legitimate purposes such as privacy protection and anonymous communication, they are also frequently used for illicit activities. Therefore, understanding the common domain extensions, especially .onion, is fundamental for cybersecurity professionals, researchers, and users aiming to safely explore or monitor dark web content.
Examples of Popular Dark Web URLs
The dark web is a hidden part of the internet that requires specific tools and knowledge to access. It is often associated with illegal activities, but it also hosts legitimate content and private communications. Identifying dark web links involves understanding their unique characteristics, such as their use of the “.onion” domain extension and the way they are structured. These links are not accessible through standard web browsers without the use of specialized software like Tor. Recognizing legitimate dark web URLs is essential for users who are exploring this part of the internet, whether for research, security, or privacy reasons. Common examples of dark web links include various “.onion” addresses, which serve as access points to hidden websites. Being aware of popular dark web URLs can help users navigate safely and avoid malicious sites. However, it is important to exercise caution and verify the authenticity of any links before clicking, as the dark web also contains numerous deceptive or harmful pages. Always prioritize security and legal considerations when exploring this aspect of the internet.
How Dark Web Links Are Structured
The dark web is a hidden part of the internet that is not indexed by traditional search engines and requires specialized software to access. One of the key characteristics of the dark web is its unique URL structure, which helps distinguish it from the surface web. Dark web links typically use the “.onion” extension, indicating they are accessible only through networks like Tor that prioritize user anonymity and privacy.
Dark web links often appear as complex, lengthy strings of alphanumeric characters, making them difficult to remember or share easily. These URLs are generated automatically, usually based on cryptographic keys, which enhances security and decentralization. For example, a dark web link might resemble http://exampleonionaddress.onion, although most are more random and unpredictable in their composition.
Understanding how dark web links are structured can help users recognize them and exercise caution when navigating unknown sites. The structure’s randomness and unique format are intentional, serving to obscure the location and identity of hosting servers. This distinctive formatting also signifies a link’s presence on the dark web, setting it apart from standard web addresses. Knowledge of these link structures is essential for safety and effective navigation within this clandestine part of the internet.
Accessing Dark Web Links Safely
Accessing dark web links safely requires careful preparation and awareness of potential risks. The dark web provides a platform for anonymous browsing, but it also hosts illicit activities and malicious content. Understanding how to navigate this hidden part of the internet securely is essential for anyone considering exploring dark web links. To start, users should utilize trusted tools like specialized browsers and VPNs to protect their identity and keep their data secure. For example, accessing a dark web link such as this dark web link can open a gateway to various resources. Ensuring your device is protected with up-to-date security software, avoiding revealing personal information, and exercising caution when clicking on links are all vital steps to maintaining safety on the dark web.
Using Tor and Dark Web Browsers
Accessing dark web links safely requires careful preparation and awareness of potential risks. The dark web hosts a variety of content that is not accessible through traditional search engines and often involves sensitive or illegal activities. To explore this part of the internet responsibly, it is essential to use specific tools like the Tor browser, which allows users to browse anonymously and securely. It is important to remain cautious and avoid sharing personal information or engaging in unlawful activities while navigating dark web links.
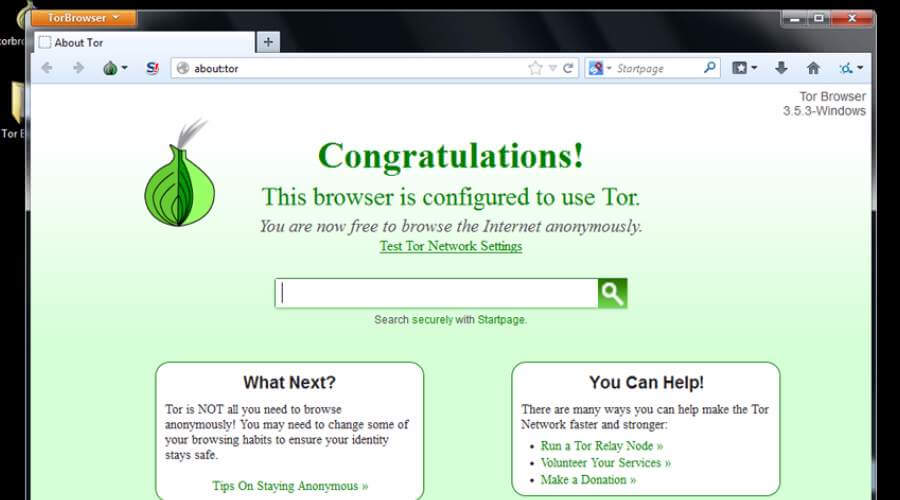
One of the most common methods for accessing dark web links is through the use of the Tor browser. Tor, which stands for The Onion Router, encrypts your internet traffic and routes it through multiple servers, making it difficult to trace your identity or location. This browser is designed specifically for accessing .onion sites and provides a layer of anonymity that helps protect users from potential threats. When using Tor, always verify the authenticity of dark web links before clicking on them to avoid malicious sites designed to compromise your security.
In addition to Tor, specialized dark web browsers can also be employed to enhance privacy and security. These browsers often come with built-in security features such as VPN compatibility, script blocking, and malware protection. It is crucial to keep your dark web browsers updated and to use reputable security tools to safeguard your devices from viruses, malware, or phishing attempts often encountered on dubious dark web links. Remember, the key to safe dark web browsing is vigilance, ensuring your system is protected and that you are complying with all relevant laws and regulations.
When exploring dark web links, always prioritize your security by using trustworthy tools, avoiding risky sites, and maintaining a low profile online. By doing so, you can access dark web content responsibly and reduce the likelihood of encountering malicious threats or legal issues. Protecting your personal information and practicing caution are vital steps to ensure a safe browsing experience on the dark web.
Dark Web Search Engines and Directories
Accessing dark web links requires careful consideration and awareness of safety practices to protect your privacy and security. The dark web is a part of the internet that isn’t indexed by standard search engines and often involves hidden networks accessible through specialized tools and browsers. To navigate this environment securely, it is essential to use trusted browsers such as Tor, which provides anonymity by routing your traffic through multiple relays. When exploring dark web links, always verify the legitimacy of the sources and avoid clicking on suspicious or unverified links that could compromise your device or personal data. Staying informed about common threats and avoiding downloading unknown files or providing unnecessary personal information can help minimize risks.
Dark web search engines and directories are valuable tools for locating specific sites within the hidden web. These search engines function similarly to traditional search engines but are optimized for accessing .onion sites. Popular options include search platforms that index a wide array of dark web content, allowing users to find links to marketplaces, forums, or information hubs. When using a search engine to locate dark web links, ensure you do so with security in mind and consider employing additional privacy measures like VPNs or secure operating environments. Remember that some links on the dark web may lead to illegal or harmful content, so exercising caution is paramount.
For safer browsing, always keep your software updated, utilize security tools such as antivirus programs, and understand the risks involved with entering various dark web sites. While dark web links can lead to legitimate and valuable resources, they also pose significant dangers if accessed irresponsibly. Educate yourself about common scams, and when in doubt, seek guidance or consult trusted sources specializing in dark web security to enhance your safety while navigating this complex part of the internet.
Best Practices for Safe Navigation
Accessing dark web links requires careful preparation and awareness of the potential risks involved. The dark web is a part of the internet that is not indexed by traditional search engines and often hosts both legal and illegal activities. To navigate it safely, it is essential to prioritize security measures and follow best practices to protect your privacy and devices.
First and foremost, use a reputable and secure browser such as Tor, which is designed specifically for anonymous browsing on the dark web. The Tor browser helps mask your IP address and encrypts your traffic, providing a layer of protection against surveillance. When visiting dark web links, ensure that you are accessing trusted sources and avoid suspicious or unverified sites that could contain malware or scams. Remember that malicious websites may appear legitimate but are designed to steal personal information or compromise your device.
Always keep your software and security tools up to date to defend against vulnerabilities. Enabling security features such as VPNs in conjunction with Tor can add an extra layer of anonymity, although it is crucial to choose a trustworthy provider. Be cautious about sharing any personal information and ignore prompts that ask for sensitive data or downloads. Navigating dark web links with caution and adherence to safety protocols significantly reduces the risks associated with exposure to harmful content or digital threats.
In summary, when accessing dark web links, prioritize using secure browsers like Tor, verify the authenticity of sites, keep your security measures current, and avoid revealing personal details. Following these best practices can help ensure a safer and more secure experience in the complex environment of the dark web.
Legal and Ethical Considerations of Dark Web Links
Exploring the dark web involves navigating a complex landscape filled with both potential opportunities and significant risks. When engaging with dark web links, it is crucial to consider the legal and ethical implications to avoid inadvertent violations of laws or involvement in harmful activities. Accessing certain content or services through dark web links may be illegal in some jurisdictions, and users must stay informed about local regulations. Ethical considerations also come into play, particularly regarding privacy, consent, and the legitimacy of the information accessed. For those interested in understanding more about dark web links, visiting trusted resources and guides can provide valuable insights into responsible usage and legal boundaries.
Legitimate Uses of Dark Web URLs
The dark web is a part of the internet that is not indexed by traditional search engines and requires specialized software to access. While it is often associated with illicit activity, there are legitimate and ethical uses of dark web links that can support privacy, security, and free expression. Understanding the legal and ethical considerations surrounding dark web URLs is essential for users and organizations alike.
Legal considerations related to dark web links primarily involve adherence to laws and regulations governing online activity. Accessing or sharing dark web URLs associated with illegal activities such as drug trafficking, illicit trade, or hacking can lead to severe legal repercussions. Even visiting certain sites without knowledge of their content can sometimes result in unintended legal issues. Therefore, it is crucial to use dark web links responsibly and within the bounds of applicable laws.
Ethically, users should consider the potential impact of engaging with dark web content. While some dark web URLs host confidential information or provide platforms for whistleblowers and journalists, others may facilitate harmful activities. Respecting privacy and ensuring that one’s actions do not contribute to criminal enterprises are vital ethical responsibilities for anyone exploring dark web links.
There are legitimate uses of dark web URLs that promote privacy and security. For example, journalists and human rights organizations often utilize dark web links to communicate securely in regions with oppressive regimes. Researchers and cybersecurity professionals also access the dark web to monitor threats and gather intelligence in a controlled and ethical manner. It is important to remember that accessing these URLs with good intent can be ethical when done lawfully and responsibly.
In summary, navigating dark web links requires careful consideration of both legal boundaries and ethical principles. Only engaging with content that aligns with lawful activities and respecting privacy and security concerns can help ensure that the use of dark web URLs remains responsible and legitimate.
Illegal Activities Associated With Dark Web Links
The dark web is a segment of the internet that exists on encrypted networks, accessible only through specialized software such as Tor. While it offers privacy and anonymity for users, it also raises significant legal and ethical concerns, especially related to the links found within this hidden part of the internet. Engaging with dark web links can pose serious risks, not only to individual users but also to society as a whole.
One of the primary legal considerations surrounding dark web links is the potential for involvement in illegal activities. Many dark web sites host illicit content, including the sale of illegal drugs, weapons, stolen personal data, counterfeit currencies, and other prohibited goods or services. Accessing or facilitating these links may inadvertently lead individuals to participate in criminal acts, which can result in severe legal consequences such as fines or imprisonment.
From an ethical standpoint, browsing or sharing dark web links raises questions about morality and responsibility. While privacy and anonymity are crucial rights, they should not be exploited to conceal unlawful activities or to harm others. Ethical use of internet resources involves respecting laws and considering the broader impact of actions taken online.
It is essential to recognize that not all dark web links are inherently illegal. However, the potential for exposure to harmful and unlawful content underscores the importance of exercising caution. Engaging with dark web links should be approached with a clear understanding of the legal boundaries and ethical implications involved. Navigating this space responsibly protects individuals and helps prevent the proliferation of illegal activities associated with certain dark web sites.
Understanding Risks and Legal Boundaries
Exploring the dark web involves accessing a concealed part of the internet that hosts a variety of content, some of which may be legal and some that is illegal. When dealing with dark web links, it is essential to understand the legal and ethical considerations associated with their use. Engaging with these links can pose significant risks, including exposure to illicit activities, scams, and malware, which can have legal repercussions. Recognizing the boundaries of lawful behavior helps protect individuals from unintended involvement in criminal enterprises or violations of privacy laws.
Legal boundaries concerning dark web links vary by jurisdiction, but generally, accessing or distributing illegal content, such as stolen data, illegal drugs, or counterfeit products, can lead to criminal charges. Even visiting certain sites may be flagged, especially if involved in activities like purchasing illicit goods or sharing copyrighted material. Ethical considerations also come into play, as users should be aware of the impact their actions have on others and avoid participating in harmful or exploitative practices.
Due diligence and strict adherence to laws are vital when exploring the dark web. It is recommended to avoid clicking on unknown dark web links that could lead to illegal content or malicious sites. For legal research or privacy-preserving activities, it is crucial to operate within the boundaries of the law and utilize secure methods. Staying informed about the legal implications and maintaining ethical standards ensure responsible navigation of this murky internet space, safeguarding oneself and respecting the rights of others.
Security Tips for Dark Web Links
Exploring the dark web can offer valuable insights and access to hidden information, but it also presents significant security risks. Protecting your identity and data is essential when navigating these unindexed networks. Implementing robust security tips for handling dark web links can help minimize potential threats and safeguard your online presence. Whether visiting sites like dark web links or exploring other hidden services, awareness and caution are paramount to maintaining security.
Protecting Your Identity and Data
Accessing and navigating the dark web requires careful attention to security to safeguard your identity and personal data. The dark web is often associated with illegal activities and malicious actors, making it essential to follow best practices to minimize risks. Protecting your digital footprint involves a combination of technical measures and cautious behavior, especially when dealing with dark web links. Ensuring your connection is secure and your identity remains anonymous helps prevent potential threats that may arise from visiting sensitive or malicious sites on the dark web.
One of the most important security tips for dark web links is to use a reputable and secure privacy-focused browser such as Tor. This browser anonymizes your internet activity and helps you access dark web content safely. Always confirm the legitimacy of the dark web links you visit, as many are designed to deceive or distribute malware. Avoid clicking on suspicious or unverified links, and never share personal information on dark web sites. When browsing, utilize strong, unique passwords and enable two-factor authentication where possible to add an extra layer of security.
Additionally, consider using a dedicated device or virtual machine for accessing the dark web to prevent any potential malware infection from spreading to your primary system. Keep your operating system and security software up-to-date to patch vulnerabilities. Be cautious about downloading files or opening unexpected attachments from dark web sources, as these can compromise your security. Remember that protecting your identity also involves anonymizing your online activity, avoiding sharing identifiable details, and never revealing real-world information that could lead to identification through a dark web link. Following these security tips can help you browse the dark web more safely while minimizing the risk of data theft or privacy breaches.
Using VPNs and Security Software
Exploring the dark web can expose users to a variety of risks, making security measures essential to protect your personal information and devices. When accessing dark web links, it is crucial to remain anonymous and secure by using the right tools and practices. Employing a dependable VPN ensures that your real IP address remains hidden, preventing malicious actors from tracing your activity back to you. A VPN encrypts your internet traffic, adding an extra layer of security when navigating dark web links. Furthermore, installing comprehensive security software helps detect and block potential threats such as malware, ransomware, or phishing attempts that are common in this part of the internet. Always verify the legitimacy of dark web links before clicking, as malicious links can lead to compromised systems or illegal content. Regularly updating your security software and avoiding sharing personal or sensitive data while exploring dark web links can significantly reduce vulnerability. Remember, maintaining a cautious approach by using a trusted VPN and security tools is vital for a safer dark web experience.
Recognizing and Avoiding Malicious Links
Exploring the dark web can be intriguing, but it also comes with significant security risks, particularly when encountering unfamiliar or suspicious links. Dark web links often lead to hidden sites that may host malicious content or scams, making it essential to exercise caution. Recognizing and avoiding malicious links is crucial for maintaining privacy and avoiding potential threats that could compromise personal information or system security.

One of the primary security tips is to verify the legitimacy of any link before clicking. Malicious links often use obfuscation techniques such as misspelled domain names or unusual URL structures to deceive users. Always hover over links to preview their destination and look for signs of suspicious activity. Using a reputable security tool or browser extension can also help identify potentially dangerous links before interacting with them.
Additionally, avoid clicking on links from untrusted sources or those received through unsolicited messages. The dark web can be a hub for scams, malware, and phishing attempts, so staying vigilant is critical. It is also recommended to use strong, unique security measures such as updated antivirus software, VPNs, and secure browsers when exploring or handling dark web links.
If you come across a dark web link that seems questionable, it’s best to refrain from opening it. Recognizing the signs of malicious links, such as strange URL formats or unexpected pop-ups, can prevent many security issues. Always prioritize safety by double-checking links, using security tools, and maintaining good online hygiene to stay protected from threats lurking on the dark web.
Monitoring and Responding to Dark Web Links
Monitoring and responding to dark web links is a critical component of cybersecurity and threat management. The dark web hosts a variety of illicit activities, including the sharing of stolen data, illegal marketplaces, and malicious communication channels. Staying vigilant involves continuously tracking suspicious links, such as http://xv3dbyu75coadsrwlbofnsg3dj5axfzcxh5v4nrvtcn3ey7uv6vrf5yd.onion, and analyzing their activity to prevent potential security breaches. Proactive engagement with dark web links enables organizations to identify emerging threats early and implement timely responses, safeguarding sensitive information and maintaining digital integrity.
Detecting Your Data on the Dark Web
Monitoring and responding to dark web links is a crucial aspect of maintaining cybersecurity and protecting sensitive information. As malicious actors often use the dark web to sell stolen data or conduct illicit activities, organizations must stay vigilant in tracking these activities. Regularly scanning areas of the dark web where sensitive data might appear helps identify potential threats before they escalate. This proactive approach enables quick response and mitigation, reducing the risk of data breaches or identity theft.
Detecting your data on the dark web involves implementing specialized tools and strategies that monitor for mentions of your organization’s information. These solutions can include dark web scanners that crawl and analyze underground forums, marketplaces, and encrypted networks to find breaches or leaks related to your business. When a link to your compromised data appears, it’s essential to respond swiftly by isolating affected systems, informing stakeholders, and enhancing security measures to prevent further exposure.
Staying ahead of dark web activity also requires continuous updates to monitoring protocols and awareness of emerging threats. Recognizing patterns or suspicious links within the dark web can help prevent significant damage. Always ensure that your cybersecurity teams are equipped with the latest intelligence and tools to detect and respond to dark web links such as dark web links. Regularly reviewing these measures will strengthen your defenses and help safeguard your organization’s reputation and assets.
Steps to Take if Your Information Is Compromised
The dark web can be a concerning avenue where sensitive information might be exposed or compromised. Monitoring for dark web links that mention your organization or personal details is essential to identify potential threats early. Regularly checking these sources helps detect breaches and malicious activities before they escalate. It is important to implement tools and services that track mentions of your credentials, sensitive data, or brand names on the dark web. When a dark web link indicating a breach is discovered, swift action is critical to minimize damage.
If you find that your information has been compromised via a dark web link, the first step is to confirm the breach. Conduct a thorough investigation to understand what data was accessed or leaked. Notify relevant stakeholders, including customers or employees if their data is affected, and follow legal and regulatory requirements for breach notification. Reset passwords, revoke compromised access credentials, and monitor accounts for suspicious activity. Strengthening security measures, such as multi-factor authentication and encryption, adds layers of protection against further threats.
It is also advisable to collaborate with cybersecurity professionals who can assist in analyzing the breach, identifying how it occurred, and implementing measures to prevent future incidents. Continuously update security protocols and educate your team about safe practices. Regularly scanning for dark web links can be an ongoing part of your cybersecurity strategy, helping you stay vigilant and respond promptly to any signs of compromise. Staying proactive is key to safeguarding your digital assets in an increasingly interconnected world.
Reporting Illegal Content and Threats
The dark web presents significant challenges for organizations aiming to maintain security and protect sensitive information. Monitoring and responding to dark web links is essential for safeguarding assets and identifying potential threats early. These links often host illicit content, data breaches, or stolen credentials, making it crucial for businesses to establish robust detection systems. Regularly scanning the dark web can help organizations discover compromised data or malicious actors attempting to leverage hidden networks.
When a dark web link is identified that references your organization’s confidential information or depicts potential threats, a prompt response is critical. This may involve investigating the source, assessing the credibility of the threat, and coordinating with cybersecurity teams or law enforcement agencies. Effective response strategies include removing exposed data, strengthening security measures, and informing affected stakeholders to mitigate harm.
Reporting illegal content and threats found through dark web monitoring is a vital part of a comprehensive security approach. Reporting should be done to appropriate authorities or agencies specialized in handling cybercrime. Maintaining detailed records of the discovered links, their context, and actions taken ensures proper follow-up and legal compliance. Additionally, staying updated on emerging dark web trends and continuously refining monitoring techniques are key to staying ahead of malicious activities associated with dark web links.