Overview of Dark Web Sites
The dark web is a complex and often misunderstood part of the internet that exists beyond the reach of standard search engines and browsers. It is characterized by a collection of websites and online services that require specialized software and configurations to access, providing a layer of anonymity for both users and site operators. While some dark web sites are associated with illegal activities, others serve legitimate purposes such as protecting privacy and facilitating secure communication in oppressive regimes. Exploring the dark web offers insight into a hidden digital universe where the rules and norms differ significantly from the surface web.
Definition and Characteristics of Dark Web Sites
The dark web comprises parts of the internet that are not indexed by traditional search engines and require specific software or configurations to access. These sites are intentionally hidden from regular browsing and are often accessed via anonymizing tools that preserve user privacy. Dark web sites are a subset of the deep web, which includes all online content not indexed by standard search engines, but they are distinguished by their emphasis on anonymity and encryption.
Typically, dark web sites are characterized by their use of encryption, hidden hosting, and unique domain extensions that are not reachable through conventional browsers. They often utilize networks like Tor or I2P, enabling users and site operators to maintain confidentiality and security. This level of privacy makes these sites suitable for various purposes, including sensitive communication for activists, journalists, and whistleblowers, as well as for illegal activities.
Unlike surface web sites, which are accessible through standard browsers and easily indexed, dark web sites often have randomized or non-descriptive domain names and are hosted on anonymized networks to prevent tracing. Their characteristics include high degrees of security, encryption, and often a focus on privacy preservation, which together foster an environment that can be both a haven for free expression and an arena for illicit dealings.
Common Technologies and Protocols Used
The dark web refers to a hidden part of the internet that is not indexed by traditional search engines and requires specific software or configurations to access. It hosts a variety of sites that operate outside the public internet, often used for private communications, whistleblowing, or illicit activities. Due to its anonymous nature, users rely on specialized technologies to access dark web sites securely and privately.
Common technologies and protocols used in the dark web include the Tor network, I2P, and Freenet. The Tor (The Onion Router) network is the most widely used, utilizing a system of layered encryption to anonymize user traffic and protect identities. Dark web sites often employ Tor for secure, anonymous hosting, with sites ending in “.onion” providing access points that are not available through standard browsers. I2P (Invisible Internet Project) offers an alternative to Tor by creating a peer-to-peer network suitable for anonymous hosting and communication. Freenet focuses on censorship-resistant data storage and sharing, allowing users to publish and access information without revealing their location or identity.
These technologies rely on complex protocols that facilitate anonymous routing and encrypted communication. Tor, for example, uses a series of relays and layered encryption to obscure user locations and browsing activities. The protocols ensure that no single relay can identify both the origin and destination of the data, enhancing privacy and security. Similarly, I2P uses garlic routing, a variant of onion routing, to route data through multiple nodes with layered encryption, making it difficult to trace.
Overall, the dark web’s sites leverage these advanced protocols and technologies to create a secure, private environment for users. While they serve legitimate purposes such as protecting privacy and free expression, they are also exploited for illegal activities. Understanding the common technologies and protocols used in the dark web is essential for grasping how anonymity and security are maintained in this hidden part of the internet.
Types and Examples of Dark Web Sites
The dark web comprises a hidden segment of the internet that requires special tools and knowledge to access. It hosts a wide variety of sites, each serving different purposes and audiences. These sites can be classified into various types based on their content and functions, ranging from marketplaces and forums to information hubs and anonymity services. Understanding the different types and examples of dark web sites is essential for recognizing both their benefits and potential risks.
Illegal Marketplaces and Black Markets
The dark web consists of a hidden part of the internet that is not accessible through standard search engines and requires specific software, configurations, or authorization to access. It hosts a variety of sites, some legitimate and others involved in illegal activities. Understanding the different types of dark web sites is crucial for recognizing both their purposes and potential risks.
One prominent category of dark web sites includes illegal marketplaces, often referred to as black markets. These platforms facilitate the trade of illicit goods and services such as drugs, firearms, stolen data, counterfeit currency, and hacking tools. These marketplaces operate anonymously, making law enforcement efforts challenging. Examples of these sites include large, well-known darknet marketplaces that have been involved in widespread illicit trading.
Another type of dark web site involves illegal service platforms offering hacking services, illegal financial transactions, or illegal VPN services. These sites often provide a range of unlawful services, including hacking for hire, money laundering, and untraceable payment options. Such platforms is designed to cater to individuals or groups seeking to commit cybercrimes with minimal risk of identification.
Black markets are also involved in the sale of stolen data, including personal information, login credentials, and financial details. Cybercriminals use these dark web sites to exchange or sell data obtained through breaches or hacking attacks. This data is often used for identity theft, fraud, or further malicious activities.
Beyond illicit markets, the dark web hosts a variety of sites dedicated to privacy advocacy, whistleblowing, and secure communication. However, the presence of illegal sites underscores the importance of remaining cautious and aware of the potential dangers associated with navigating the dark web. Recognizing the types and examples of sites found there helps users understand the scope of activities and the need for security measures when exploring this hidden part of the internet.
Legal and Reputable Dark Web Sites
The dark web comprises a hidden part of the internet that is not indexed by standard search engines and requires specialized software to access. It hosts a wide variety of sites, ranging from illicit marketplaces to privacy-focused platforms, making it a complex landscape to understand. Knowing the different types of dark web sites can help users identify both potential risks and legitimate uses.
One common type of dark web site is black marketplaces, where illegal goods and services such as drugs, weapons, and stolen data are often traded. These sites operate with a high degree of anonymity and are a well-known aspect of the darker side of the internet. Conversely, there are also forums and communities where individuals discuss sensitive topics, such as whistleblowing or political activism, often seeking privacy and security away from oppressive regimes.
Another category includes privacy-focused services, like anonymous email providers or secure communication platforms, designed to protect users’ identities. Additionally, the dark web hosts news outlets and human rights organizations that use it to share information safely in regions with censorship or surveillance. These entities demonstrate that while the dark web has a reputation for illegal activity, it also plays a vital role in supporting free expression and privacy rights.
Legal and reputable dark web sites are those that operate ethically and within the boundaries of the law. For example, certain news organizations maintain secure, onion-site versions of their platforms to enable whistleblowers and journalists to exchange information securely. Similarly, some non-profit organizations utilize the dark web to provide resources and support to vulnerable populations or to facilitate secure communications during sensitive situations.
Understanding the different types and purposes of dark web sites is essential for navigating this hidden part of the internet responsibly. Recognizing the distinction between illicit and legitimate sites helps users protect their privacy and avoid dangerous or illegal content. When approached with caution and awareness, the dark web can serve as a valuable tool for privacy, free expression, and secure communication in a digital landscape increasingly defined by concerns over surveillance and censorship.
Accessing Dark Web Sites
Accessing dark web sites requires specific tools and precautions to ensure safety and anonymity. The dark web is a hidden part of the internet that is not indexed by standard search engines and can only be accessed through specialized software such as Tor. Navigating this anonymous space involves understanding the necessary steps and security measures to protect your identity and data. With proper knowledge, users can explore dark web sites securely while being aware of the potential risks involved.
Darknet Protocols and Browsers (e.g., Tor)
The dark web consists of a hidden part of the internet that is not indexed by traditional search engines and requires specialized tools to access. It is often associated with anonymity and privacy, making it a space where confidential communication and certain activities take place. Accessing dark web sites involves understanding the key technologies and protocols that enable users to navigate this clandestine part of the internet securely and privately.
Darknet protocols such as Tor, I2P, and Freenet are essential for accessing the dark web. Among these, Tor (The Onion Router) is the most widely used browser that facilitates anonymous browsing by routing internet traffic through a series of volunteer-operated servers worldwide. This process encrypts data multiple times, making it difficult to trace users’ locations or identify their activities. Tor is designed to protect user privacy and enable access to dark web sites that are hosted as hidden services with specific addresses known as onion sites.
Using browsers like the Tor Browser allows users to access dark web sites securely, but it is important to exercise caution. The dark web hosts a wide range of content, some of which may be illegal or dangerous. Users should ensure they understand the risks involved and take measures such as using strong security practices, avoiding sharing personal information, and refraining from downloading files or clicking on unfamiliar links. While the dark web offers space for privacy-focused activities, it is essential to navigate it responsibly and ethically.
In summary, accessing dark web sites requires specialized tools like Tor, which utilize specific protocols to provide anonymity and privacy. Awareness of the underlying technology and cautious browsing habits are key to safely exploring this hidden portion of the internet.
Legality and Risks of Accessing
The dark web consists of a portion of the internet that is not indexed by standard search engines and requires specialized software to access. It is often associated with anonymous browsing and clandestine activities, making it a topic of both curiosity and concern. Accessing dark web sites can provide privacy and security for individuals needing to communicate confidentially, but it also carries significant risks and legal considerations.
Legally, accessing dark web sites is a complex issue. While browsing the dark web itself is not illegal in many jurisdictions, engaging in activities such as purchasing illicit goods, accessing illegal content, or participating in unlawful transactions is strictly prohibited and can lead to severe penalties. It is important for users to understand the law in their country and to avoid activities that violate legal standards when exploring the dark web.
There are substantial risks associated with accessing dark web sites. These include exposure to malicious software, scams, and harmful content. Cybercriminals often populate these sites to distribute malware or conduct fraudulent schemes. Additionally, because of the anonymous nature of the dark web, it can be a hub for illegal trade and activities, increasing the chances of encountering dangerous situations. Users should take precautions such as using strong security measures and understanding the legal boundaries to avoid unnecessary risks.
Understanding the nature of the dark web, its legal implications, and associated dangers is essential for anyone considering exploring it. Responsible and informed use is crucial to secure your privacy and stay within the bounds of the law.
Activities on Dark Web Sites
The dark web is a hidden part of the internet that requires specific software and configurations to access. It is known for hosting a wide variety of activities, ranging from private communications to illicit transactions. Many users visit dark web sites seeking anonymity and privacy, but they can also encounter dangerous or illegal content. Understanding the types of activities that occur on dark web sites is essential for staying informed and maintaining safety while exploring this mysterious online realm.
Illicit Transactions and Black Markets
The dark web consists of parts of the internet that are not indexed by standard search engines and require specific software, configurations, or authorization to access. It is often associated with a variety of activities, both legitimate and illicit. Among the most concerning aspects of dark web sites are the illicit transactions and black markets that operate within this hidden network. These sites facilitate the exchange of illegal goods and services, making them a hub for activity that bypasses traditional legal frameworks.
Illicit transactions on dark web sites cover a wide range of illegal items, including firearms, drugs, stolen data, and counterfeit documents. These transactions often involve cryptocurrencies to maintain the anonymity of both buyers and sellers. Black markets hosted on dark web sites enable vendors to reach a global customer base while evading law enforcement efforts, creating a complex challenge for authorities trying to combat illegal trade.
The anonymity provided by the dark web’s architecture allows these activities to flourish, attracting individuals involved in illegal enterprises. Law enforcement agencies worldwide continuously work to monitor and dismantle these black markets, but the decentralized and encrypted nature of dark web sites makes enforcement difficult. Awareness and understanding of these illicit activities are crucial for developing effective strategies to combat illegal trade and protect users from unknowingly engaging in such transactions.
Legitimate Uses and Privacy Purposes
The dark web is a part of the internet that requires special software and configurations to access, often associated with anonymity and privacy. While it is frequently depicted in a negative light, there are legitimate activities conducted on dark web sites that serve important purposes for privacy-conscious individuals and organizations.
One of the primary legitimate uses of dark web sites is for protecting privacy and ensuring secure communication. Journalists, activists, and whistleblowers may utilize these sites to share sensitive information without fear of exposure or retaliation. Additionally, human rights organizations sometimes leverage dark web platforms to connect with individuals in oppressive regimes or dangerous environments, facilitating anonymous reporting and support.
Engaging in activities on dark web sites for privacy purposes can include:
- Secure communication and correspondence that cannot be traced back to the user
- Accessing information securely in environments with heavy censorship
- Distributing information anonymously to protect sources and vulnerable populations
- Participating in forums and communities that prioritize confidentiality and privacy for sensitive topics
It is important to recognize that while the dark web has a reputation for illegal activities, numerous legitimate and necessary functions are carried out there. These activities emphasize the importance of privacy and security for users operating under oppressive conditions or seeking confidential communication channels.
- The dark web is not meant for the general public since it is harder to access and need technical knowledge.
- A subset of the Deep Web, the Dark Web is intentionally hidden from your standard search engines, and is much more difficult to access as all its data is encrypted.
- However, the dark web is also used by individuals seeking online privacy or to bypass censorship in their home countries.
- Google only indexes websites on the open web (freely accessible and public), while dark web sites use .onion domains that are not visible to traditional search engines.
Security and Threats Associated with Dark Web Sites
The dark web is a hidden segment of the internet that operates on encrypted networks, making it difficult to access without specialized tools. While it offers anonymity for users, it also hosts various illegal activities and malicious actors. Security threats associated with dark web sites are significant, ranging from data breaches and financial scams to illegal trades and cyberattacks. Users who venture into this shadowy part of the internet often face risks that can compromise their personal information and digital security. It is essential to be aware of these dangers and understand the potential consequences of engaging with dark web sites.
One notable concern is the prevalence of dark web sites that facilitate illegal transactions or distribute malicious software. These sites can be used by cybercriminals to exchange stolen data, counterfeit goods, or weapons, often evading law enforcement detection. For instance, browsing some dark web sites without proper safeguards can lead to exposure to scams and malware that can infect devices or steal sensitive data. Therefore, users should exercise caution and implement robust security measures if they choose to explore this hidden online realm. For those seeking a safer entry point, some platforms provide gateway sites that offer limited access or guidance to navigate the dark web securely.
To explore dark web sites securely, consider using anonymizing tools and specialized browsers designed to protect user identity. Remember that not all dark web sites are malicious, but the potential security threats make it risky for the uninformed. Always stay updated on best practices for online safety and avoid engaging in any illegal activities. Learn more about protecting yourself on dark web sites by visiting reputable resources dedicated to cybersecurity and safe browsing.
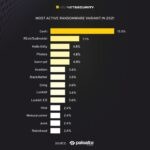
Cybercriminal Operations and Attack Coordination
The dark web consists of a hidden part of the internet that is not indexed by traditional search engines and requires specialized software to access. While it offers legitimate uses such as protecting privacy and enabling free expression in restrictive environments, it is also a hub for various malicious activities. Dark web sites often host illegal content, black markets, and forums where cybercriminals coordinate their operations. These sites provide a degree of anonymity that facilitates the planning and execution of cyber threats beyond the reach of law enforcement.
Cybercriminal operations on dark web sites are increasingly sophisticated, involving activities such as hacking services, recruitment of cybercriminals, and exchange of stolen data. These platforms serve as marketplaces for weapons, illicit drugs, and stolen financial information, fueling a range of cyber threats. Attack coordination often occurs on these sites, where hackers share tools, techniques, and targets to execute large-scale attacks such as ransomware campaigns, data breaches, and distributed denial-of-service (DDoS) attacks.
Security concerns related to dark web sites are significant because they enable the proliferation of cyber threats and criminal activities. Law enforcement agencies face challenges in tracking down and dismantling these operations due to the anonymity provided by anonymizing technologies. Organizations and individuals must remain vigilant, implementing strong cybersecurity measures and monitoring for potential threats originating from dark web sources. Recognizing the risks associated with dark web sites can help in developing more effective strategies to prevent cyber attacks and protect sensitive information.
Distribution of Malware and Exploits
The dark web sites are often associated with a variety of security challenges and threats that pose significant risks to individuals, organizations, and even national security. Due to their anonymous nature, these sites facilitate illicit activities, including the distribution of malicious software and exploits, making them a major concern for cybersecurity professionals.
One of the primary threats linked to dark web sites is the proliferation of malware, which is frequently exchanged or sold in these hidden online marketplaces. Cybercriminals leverage these platforms to distribute malicious tools such as ransomware, trojans, and viruses that can infect computers, servers, and entire networks. This illicit trade of malware enables attackers to bypass traditional security measures and reach targets with less scrutiny.
Exploits are another significant concern associated with dark web sites. These are code vulnerabilities that attackers can exploit to gain unauthorized access to systems or escalate their privileges. Dark web markets often serve as hubs for the sale of zero-day exploits and hacking tools, allowing cybercriminals to launch sophisticated attacks against both private and public sector targets.
The anonymous environment of dark web sites complicates efforts to trace and shut down malicious activities. Cybersecurity teams must remain vigilant, employing advanced detection techniques to identify and mitigate threats emerging from these hidden platforms. Protecting sensitive data and maintaining robust security protocols are essential in countering the dangers posed by the distribution of malware and exploits originating from dark web sites.

Monitoring and Protecting Against Dark Web Threats
Monitoring and protecting against dark web threats is essential for organizations aiming to safeguard sensitive information and maintain operational integrity. The dark web hosts a variety of sites that can be exploited for malicious activities, including data breaches, illegal transactions, and cybercriminal collaborations. Identifying and tracking these activities require a proactive approach to threat detection and risk management. By continuously monitoring dark web sites, businesses can detect early signs of data leaks and unauthorized access, enabling swift responses to mitigate potential damages. Staying vigilant against these hidden sites is a crucial component of a comprehensive cybersecurity strategy, helping organizations to stay a step ahead of cybercriminals operating within the dark web.
Dark Web Monitoring Tools and Strategies
Monitoring and protecting against threats originating from the dark web is an essential component of modern cybersecurity strategies. Dark web sites serve as hubs for illicit activities, including data breaches, illegal transactions, and the exchange of stolen information. Organizations need effective tools and strategies to identify and mitigate risks associated with these hidden marketplaces and forums, where stolen credentials, sensitive corporate data, or intellectual property may be traded or sold.
Implementing a comprehensive dark web monitoring approach involves several key strategies. First, organizations should utilize specialized monitoring tools capable of scanning dark web sites for leaks of company credentials, proprietary data, or other sensitive information. These tools often employ keyword searches, data hashing, and AI-driven analytics to detect relevant mentions or leaks. Additionally, establishing incident response protocols ensures that any findings are promptly investigated and contained, minimizing potential damage.
Furthermore, organizations can adopt proactive measures to protect against dark web threats. Employee training on security best practices reduces the risk of credential compromise, while enforcing strong, multi-factor authentication makes it harder for malicious actors to exploit stolen data. Regular security audits and vulnerability assessments also help identify weaknesses before they are exploited on dark web sites.
- Utilize specialized dark web monitoring tools to scan for stolen credentials, proprietary data, or sensitive information.
- Implement real-time alerts to notify security teams of potential threats detected on dark web sites.
- Maintain an incident response plan specifically addressing dark web-related breaches.
- Educate employees on cybersecurity best practices to prevent credential leaks.
- Enforce strong authentication and regular password updates to reduce the risk of account compromise.
- Conduct periodic vulnerability assessments to identify and address security weaknesses.
By combining advanced monitoring tools with strategic preventative measures, organizations can better defend against threats that originate from dark web sites. Staying proactive and vigilant is essential in minimizing cyber risks and protecting valuable assets from malicious activities lurking in these hidden corners of the internet.
Threat Intelligence and Early Warning Signs
Monitoring and protecting against dark web threats is a critical component of a comprehensive cybersecurity strategy. Organizations need to be proactive in identifying potential risks originating from dark web sites, where malicious actors often share stolen data, exploit vulnerabilities, and plan cyberattacks. Staying informed about these activities allows businesses to act swiftly and mitigate potential damages.
Threat intelligence plays a vital role in detecting and understanding dark web activities. By gathering and analyzing data from various sources, security teams can uncover emerging threats, compromised credentials, and targeted attack campaigns before they escalate. Implementing automated monitoring solutions that scan dark web sites for leaked information or references to an organization’s assets enhances the ability to respond promptly to potential threats.
Early warning signs on dark web sites often include the appearance of stolen login credentials, proprietary data, or discussions indicating planned attacks. Recognizing these indicators requires trained analysts who can interpret cryptic or coded communications typical of dark web environments. Regular threat intelligence reports and alerts enable organizations to adjust security measures and reinforce defenses where needed.
To effectively safeguard against dark web threats, organizations should adopt a layered security approach, combining technical safeguards with user education and continuous monitoring. By maintaining an active watch on dark web sites and staying alert to early warning signs, businesses can reduce the risk of data breaches and cyberattacks, ensuring a resilient security posture against evolving cybercriminal tactics.
Law Enforcement and Dark Web Takedowns
Law enforcement agencies around the world are increasingly focused on tackling illegal activities that take place on the dark web. This hidden part of the internet hosts a variety of clandestine operations, from drug trafficking to cybercrime, making it a challenging environment for authorities to monitor and regulate. Dark web takedowns are a critical component of efforts to disrupt criminal networks and ensure online safety. These operations often involve complex investigations and collaboration across borders to identify and shut down illicit dark web sites.
Operations Against Illegal Dark Web Sites
Law enforcement agencies around the world actively monitor and conduct operations against illegal activities on the dark web, targeting illicit sites involved in trade of drugs, weapons, stolen data, and other criminal enterprises. Given the anonymity provided by dark web platforms, these operations often require advanced techniques and international cooperation to identify and dismantle harmful sites. Successful takedowns rely on complex investigative methods, including digital forensics, undercover operations, and collaboration with cybersecurity experts.
Operations against illegal dark web sites aim to disrupt criminal networks and prevent the proliferation of illegal goods and services. This involves tracking digital footprints, compromising dark web marketplaces, and gathering intelligence to locate administrators and users involved in illegal activities. Law enforcement agencies also utilize
Challenges in Disrupting Dark Web Activities
Dark web sites have become a focal point for various illegal activities, posing significant challenges for law enforcement agencies worldwide. These sites operate within the hidden layers of the internet, often utilizing encrypted networks to maintain user anonymity and evade detection. The inherently covert nature of the dark web complicates efforts to identify and shut down illicit marketplaces, forums, and communication channels that facilitate activities such as drug trafficking, weapons sales, cybercrime, and human trafficking.
Law enforcement agencies face numerous hurdles when attempting to disrupt dark web sites. One major challenge is the use of anonymization tools, such as Tor, which obscure user identities and make tracing transactions and communications extremely difficult. Additionally, dark web sites frequently employ sophisticated technological measures to protect their operators’ identities, including encryption, false hosting servers, and decentralized architectures.
Moreover, these sites are often rapidly relocated or reconstructed after takedowns, which complicates ongoing efforts to permanently shut them down. Criminal actors also frequently use layered encryption and multiple proxy servers to mask their activities, further hindering investigations. The decentralized and resilient nature of some dark web sites can result in a persistent presence that resists conventional enforcement tactics.
Despite these challenges, law enforcement continues to develop innovative strategies to target dark web sites. These include digital forensics, undercover operations, and international collaborations, aimed at undermining the infrastructure that supports illicit activities. Efforts to disrupt dark web sites require a combination of technical expertise, legal frameworks, and coordinated efforts across jurisdictions to effectively combat the illegal operations hosted within these hidden corners of the internet.