Understanding the Dark Web and Darkmarket Links
The dark web is a hidden part of the internet that requires specialized software to access and is often associated with various illicit activities. Among the most talked about areas within this hidden network are darkmarkets, which are online platforms where illegal goods and services are bought and sold. Understanding how darkmarkets operate and recognizing their links can provide insight into this shadowy world. For instance, some darkmarket links are used to facilitate transactions that are difficult to trace, making them a focus of law enforcement efforts. Exploring these links, such as the darkmarket link in question, can help researchers and security professionals understand the scope and nature of online illicit trade. Additionally, platforms like this darkmarket link exemplify the types of marketplaces operating in the dark web environment. Gaining knowledge about darkmarket links is crucial for developing strategies to combat illegal activities on these platforms and enhance overall cybersecurity.
What Are Darkmarket Links?
The dark web is a part of the internet that is not indexed by traditional search engines and requires specific software or configurations to access. It is often associated with illicit activities, including the operation of darkmarkets. Darkmarket links are specialized URLs that direct users to these hidden marketplaces where illegal goods and services are bought and sold. These links are typically encrypted and rely on anonymity networks to conceal the location and identity of both buyers and sellers. Navigating darkmarket links requires caution, as they are frequently targeted by law enforcement, and engaging with these sites carries significant legal risks. Understanding what darkmarket links are and how they operate is essential for security professionals, researchers, and law enforcement agencies working to combat illegal online activities. Such links serve as access points to underground marketplaces, facilitating transactions that bypass traditional oversight and regulatory frameworks. Recognizing the structure and purpose of darkmarket links can aid in efforts to monitor, investigate, and disrupt illegal online networks and activities.
Types of Darkmarket Links
The dark web is a hidden part of the internet that operates outside the reach of standard search engines and is often associated with anonymous activities. Within this clandestine realm, darkmarkets serve as digital marketplaces where various illicit goods and services are bought and sold. Understanding darkmarket links is crucial for recognizing how these illegal transactions are facilitated and how they operate in the shadows of the internet.
Darkmarket links are specific URLs that direct users to these underground trading platforms. These links are often disguised or encrypted to evade detection by authorities and security systems. They typically include alpha-numeric characters and sometimes resemble legitimate website addresses, making them difficult for untrained users to identify. These links act as gateways for traders and buyers to access prohibited items, ranging from stolen data to illegal substances or counterfeit products.
There are various types of darkmarket links, each serving different purposes within the illicit online ecosystem. Some links lead directly to marketplace homepages, where users can browse listings or create accounts. Others are session-specific links used for private transactions or secure communication channels. Additionally, some darkmarket links are used for escrow services or to facilitate particular transactions securely, ensuring both parties fulfill their obligations without trusting each other entirely.
Recognizing these darkmarket links and understanding their structure is essential for cybersecurity professionals, law enforcement, or anyone interested in monitoring cyber threats. They highlight the importance of employing advanced detection techniques to track and disrupt illegal activities happening on the dark web. As these links continually evolve to evade detection, staying informed about their nature and types remains vital in combating cybercrime.
The Role of Darkmarket Links in Illicit Activities
The darkweb is a hidden segment of the internet that exists outside the realm of traditional search engines and accessible via specialized software. Within this concealed network, darkmarkets serve as clandestine marketplaces where a wide array of illicit activities take place. These platforms facilitate the sale and exchange of illegal goods such as drugs, weapons, stolen data, and counterfeit documents. A core component that enables these transactions is the use of darkmarket links, which act as gateways to access these secretive marketplaces securely and anonymously. These links are often shared among users through encrypted channels, ensuring anonymity and reducing the risk of detection.
Darkmarket links play a pivotal role in the facilitation of criminal activities by providing a simplified method for individuals to access these illicit marketplaces. Once connected through a darkmarket link, users can browse listings, communicate with vendors, and complete transactions, often using cryptocurrencies for added anonymity. The ease of sharing these links makes it easier for illicit networks to operate in secret while expanding their reach globally. Law enforcement agencies continually seek to monitor and dismantle these networks, but the dynamic nature of darkmarket links and the use of encryption technologies make it challenging to trace and curb illegal activity.
Understanding how darkmarket links function is essential in recognizing the scope of cybercrime and online black markets. These links serve as critical junctures for facilitating the exchange of prohibited goods and services, emphasizing the need for ongoing cybersecurity efforts and international cooperation to combat these illegal operations effectively.
Accessing Darkmarket Links Safely and Legally
Accessing darkmarket links safely and legally requires a thorough understanding of the potential risks involved and adherence to applicable laws. These platforms often operate in the shadows of the internet, making it essential to prioritize security measures and legal boundaries when exploring such sites. Ensuring your own safety while navigating these environments involves using proper tools and techniques, such as secure browsing methods and anonymity tools. For those interested in exploring darkmarkets responsibly, understanding the importance of legal compliance is crucial. Some researchers and security professionals may access certain darkmarket links, such as darkmarket links, under specific circumstances for investigative purposes and cybersecurity analysis. Being cautious and informed helps mitigate potential dangers and legal issues associated with darkmarket access.
Methods of Connecting to Darkmarket Links
Accessing darkmarket links safely and legally is a complex topic that requires considerable caution and awareness of legal boundaries. Darkmarkets are often associated with illegal activities, and connecting to them can expose users to significant risks. It is essential to understand the methods of connecting to darkmarket links carefully to avoid compromising security or violating laws. Proper knowledge can help ensure that any interaction with such sites remains within legal limits and minimizes potential harm.
When exploring darkmarket links, taking security precautions is crucial. Here are some methods to connect safely and legally:
- Use a Secure and Privacy-Focused Network: Always connect through a reliable Virtual Private Network (VPN) to mask your IP address and encrypt your internet traffic. This adds a layer of privacy and helps prevent tracking.
- Employ Tor Browser for Access: The Tor network is often used to access darkmarkets securely, providing anonymity by routing connections through multiple relays. Using the Tor browser ensures that your identity remains protected while browsing darkmarket links like Darkmarket link.
- Keep Software Up-to-Date: Regularly update your browser, operating system, and security tools to defend against vulnerabilities that could be exploited when accessing darkmarket sites.
- Use Strong, Unique Passwords and Enable Two-Factor Authentication: If login credentials are involved, safeguarding your accounts with strong passwords and additional verification can prevent unauthorized access.
- Be Aware of Legal Implications: Always ensure your activities adhere to local laws. Accessing or participating in illegal transactions can lead to serious legal consequences regardless of the safety precautions taken.
Connecting to darkmarket links requires a careful balance of maintaining anonymity and abiding by legal standards. Utilizing tools like the Tor browser and VPNs can help protect your identity, while vigilance against suspicious activity and adherence to applicable laws are vital. Remember that engaging with darkmarkets carries inherent risks, so proceed with caution and always prioritize your safety and legal compliance.
Legal Considerations When Visiting Darkmarket Links
Accessing dark market links involves navigating underground online marketplaces that often facilitate illegal activities. These platforms operate on encrypted networks, making it challenging for users to ensure their safety and legality. It is essential to understand the risks involved and to approach such sites with caution, recognizing that they are often associated with illegal transactions or content. Protecting your personal information and maintaining anonymity are critical steps if you choose to explore these markets, but it is equally important to be aware of the legal implications involved.
Legal considerations play a significant role when visiting darkmarket links. Engaging with sites linked to illicit goods or services can lead to serious legal consequences, including criminal charges. Authorities actively monitor these platforms to combat illegal activities, and legal jurisdictions across the world treat unauthorized access or participation in such markets as unlawful. Users should always be aware that accessing or attempting to purchase illegal items from a darkmarket link may be deemed a crime, regardless of intent or knowledge.
Furthermore, attempting to access darkmarket links without adequate safeguards can expose users to cybersecurity threats such as malware, scams, and data breaches. The use of VPNs, secure browsers, and other privacy tools can enhance safety, but do not eliminate all risks. It is crucial to prioritize legal and ethical considerations, avoiding any activity that violates laws or regulations. Ensuring compliance with local laws and understanding the serious ramifications of phishing, fraud, or other illegal acts is essential when dealing with darkmarket links.
In summary, while the allure of darkmarket links might seem tempting for some, their exploration carries significant legal and safety dilemmas. Being informed about the risks and adhering strictly to legal boundaries is vital to avoid severe consequences. Users should remember that engaging with such sites can have profound personal and legal implications, shaping the importance of responsible behavior online.
Risks and Precautions for Users
Accessing darkmarket links poses significant legal and security risks, and it is crucial for users to understand the potential consequences before attempting to visit such sites. Darkmarkets are part of the dark web, which operates on a separate network from the traditional internet, often used for illicit activities. While some individuals may seek these links for legitimate reasons, such as research or security analysis, the dangers involved are substantial. Visiting darkmarket links like darkmarket links without appropriate precautions can expose users to malware, scams, and legal actions.
Legal implications are among the foremost concerns when accessing darkmarket links. Many activities conducted on these sites are illegal in numerous jurisdictions, including the sale of illegal substances, stolen data, or counterfeit items. Engaging in or even merely browsing these sites can lead to serious legal repercussions, including criminal charges. Therefore, it is essential to be well-informed about local laws and regulations to avoid unintentionally committing a crime.
Security risks also abound when visiting darkmarket links. These sites are often targeted by cybercriminals who seek to exploit visitors through malware, phishing, or other malicious tactics. Using secure and anonymized methods, such as a reputable VPN and the Tor network, can add layers of protection. However, even with these measures, the risk remains high. Users should never provide personal or financial information when accessing darkmarket links, as this can lead to identity theft or financial loss.
Precautions for users include being cautious and aware of the potential dangers involved. Employing robust cybersecurity practices, including updating software, using strong and unique passwords, and avoiding downloads from untrusted sources, is essential. Additionally, understanding that access to darkmarket links is inherently risky and that legal issues can result from even casual browsing helps users make more informed decisions. Ultimately, avoiding darkmarket links altogether is the safest approach, but if access is necessary for professional or research purposes, it must be done with extreme caution and awareness of the risks involved.
Darkmarket Links and Cybersecurity Threats

Darkmarket links have become a focal point within the realm of cybersecurity threats, posing significant challenges to law enforcement and organizations alike. These clandestine online marketplaces facilitate the exchange of illicit goods and services, often hiding behind encrypted networks to evade detection. Understanding the nature of darkmarket links is essential in developing effective strategies to combat cybercrime and protect sensitive information. One such darkmarket link exemplifies the hidden infrastructure used by cybercriminals to operate in the shadowy corners of the internet.
Cybersecurity experts continuously monitor and analyze darkmarket links to uncover patterns and vulnerabilities, aiming to dismantle these illegal networks. The proliferation of darkmarket links underscores the importance of robust cybersecurity measures and awareness among users to prevent unauthorized access and data breaches. For instance, accessing resources on platforms like darkmarket links can expose users to a range of threats, including malware, phishing, and financial scams. Staying informed and cautious is crucial in navigating the complexities of the dark web and safeguarding digital assets.
Use of Darkmarket Links by Cybercriminals
Darkmarket links are digital pathways that connect users to illicit marketplaces operating on the dark web. These links serve as gateways for cybercriminals to exchange illegal goods and services, including stolen data, drugs, firearms, and hacking tools. The anonymity provided by dark markets and the use of encrypted connections make these links attractive for malicious actors aiming to conduct covert transactions without easy detection.
Cybercriminals frequently exploit darkmarket links to facilitate various cyber threats and illegal activities. These links enable unauthorized exchanges that bypass traditional law enforcement efforts and standard security measures. Once on a darkmarket platform, perpetrators can buy and sell malicious software, compromised credentials, or access to cyber networks, thus increasing the scope and sophistication of cyber threats.
Utilization of darkmarket links by cybercriminals contributes significantly to cybersecurity threats in several ways:
- Spreading malware and ransomware through illicit transactions facilitated by darkmarket links.
- Trading stolen personal, financial, or corporate data, which can lead to identity theft and financial fraud.
- Organizing coordinated cyberattacks, including phishing campaigns and Distributed Denial of Service (DDoS) assaults.
- Distributing hacking tools and exploits that enable breaches into vulnerable systems.
Understanding the role of darkmarket links in cybercrime is essential for developing effective cybersecurity strategies. Organizations must employ advanced monitoring, threat intelligence, and user education to detect and mitigate threats originating from these clandestine online pathways. Vigilance towards darkmarket activities can help prevent the proliferation of cybercriminal operations and protect sensitive information from falling into malicious hands.
Impact on Organizations and Data Security
Darkmarket links are notorious within the cybersecurity landscape as gateways to illicit online marketplaces where illegal activities such as drug trafficking, weapon sales, stolen data trading, and cybercriminal services are conducted. These links serve as access points for cybercriminals to exchange illegal goods and services, which significantly heighten the threat landscape for organizations and data security. The proliferation of darkmarket links makes it challenging for organizations to protect sensitive information and maintain secure operational environments.
Engagement with darkmarket links can pose severe cybersecurity threats, including data breaches, malware infections, and financial fraud. Cybercriminals utilize these platforms to acquire stolen credentials, sell malicious tools, or distribute ransomware. The presence of these links within an organization’s network or infrastructure can facilitate unauthorized access, leading to compromised systems and loss of critical data. Moreover, the anonymity afforded by darkmarket links complicates law enforcement efforts to track and dismantle illegal operations, which in turn sustains ongoing security risks for organizations.
The impact on organizations and data security can be profound:
- Improved risk of data breaches and theft of sensitive information.
- Increased exposure to malware and ransomware attacks through malicious downloads linked to darkmarket sources.
- Potential financial losses due to fraud, data recovery, and legal repercussions.
- Damage to reputation and customer trust resulting from data exposure or security incidents.
- Escalation of cyber espionage activities targeting corporate intellectual property and strategic data.
Understanding the role of darkmarket links is essential for strengthening cybersecurity defenses. Organizations should implement advanced threat detection systems, educate employees on phishing and illicit link recognition, and maintain robust security policies to mitigate the risks associated with these clandestine platforms. Being vigilant about the presence and exploitation of darkmarket links can significantly enhance organizational resilience and safeguard valuable data assets from cyber threats.
Monitoring and Disruption of Darkmarket Links
Darkmarket links are online gateway points used to access underground marketplaces that facilitate the trade of illicit goods and services. These links often serve as critical infrastructure for cybercriminal activities, enabling vendors and buyers to connect while maintaining a degree of anonymity. Due to the unlawful nature of the transactions, these links are highly targeted by cybersecurity agencies aiming to disrupt illegal markets and protect digital ecosystems.
Monitoring darkmarket links is a complex process that involves advanced cybersecurity techniques such as threat intelligence gathering, network traffic analysis, and the use of specialized crawling tools. Security teams track the disappearance or resurgence of these links to identify new marketplaces or to apprehend operators involved in illicit transactions. Disrupting these links is a vital part of reducing cyber threats, as it hampers the ability of cybercriminals to conduct operations securely.
Cybersecurity Threats Associated with Darkmarket Links
Darkmarket links pose various cybersecurity threats, including:
- Data Breaches: Access to illicit marketplaces can lead to leaks of sensitive information, impacting victims and exposing vulnerabilities in cybersecurity defenses.
- Malware Distribution: Links often serve as gateways for distributing malware, ransomware, and viruses that infect systems upon access.
- Financial Fraud: Engaging with darkmarket links can result in financial theft, scams, and identity theft, which are difficult to trace and prevent.
- Network Intrusions: Cybercriminals leverage darkmarket connections to probe networks for exploitable vulnerabilities.

Monitoring and Disruption Strategies
Effective monitoring involves leveraging automated tools to scan for emerging darkmarket links, analyzing patterns, and correlating data from various sources. Law enforcement agencies often collaborate with cybersecurity organizations to identify and shut down these links by seizing servers or infiltrating marketplaces. Disruption tactics include takedown operations, legal actions against vendors, and deploying honeypots to deceive and trap cybercriminals. These efforts are crucial in reducing the reach of darkmarkets and securing digital spaces against ongoing threats.
Understanding the nature of darkmarket links and implementing proactive cybersecurity measures are essential steps in combating cyber threats. Continuous monitoring and disruption efforts help protect individuals, organizations, and national security interests from the persistent dangers posed by underground online marketplaces.
Legitimate Uses of Darkmarket Links
Darkmarket links are often associated with illicit activities, but they can also serve legitimate purposes under certain circumstances. For example, secure communication channels for journalists, whistleblowers, or human rights organizations might utilize darkmarket links to protect their sources and maintain anonymity. These links can facilitate access to confidential information or specialized resources that require heightened privacy measures. Understanding the appropriate and lawful uses of darkmarket links, such as darkmarket links, is essential to ensure responsible and ethical engagement with this technology.
Whistleblowing and Anonymous Communication
Darkmarket links are often associated with illicit activities, but they can also serve legitimate purposes under certain circumstances. Understanding the nuanced use of these links is essential for distinguishing between harmful and lawful practices. In some cases, individuals or organizations utilize darkmarket platforms and their links for whistleblowing, anonymous communication, or secure information exchange, especially when facing repressive regimes or surveillance. These applications highlight the importance of privacy and security in sensitive contexts.
Legitimate uses of darkmarket links include:
- Whistleblowing: Securely sharing confidential information about corruption, abuse, or illegal activities within organizations or governments, without fear of retaliation.
- Anonymous communication: Protecting the identities of individuals involved in journalistic activities or activism, enabling them to reach out or disseminate information while maintaining anonymity.
- Research and investigation: Law enforcement and cybersecurity professionals may use darkmarket links to monitor illegal activities, gather intelligence, and develop strategies to combat malicious actors.
- Conflict zones or oppressive regimes: Facilitating secure communication for journalists, activists, or citizens operating under restrictive environments where surveillance is prevalent.
While accessing or sharing links associated with darkmarkets carries risks, understanding their legitimate applications underscores their role in promoting privacy, safety, and transparency in situations where conventional communication channels may be compromised. Responsible and ethical use of such links is crucial to ensure they serve their intended protective purposes.
Press and Non-Governmental Organization Activities
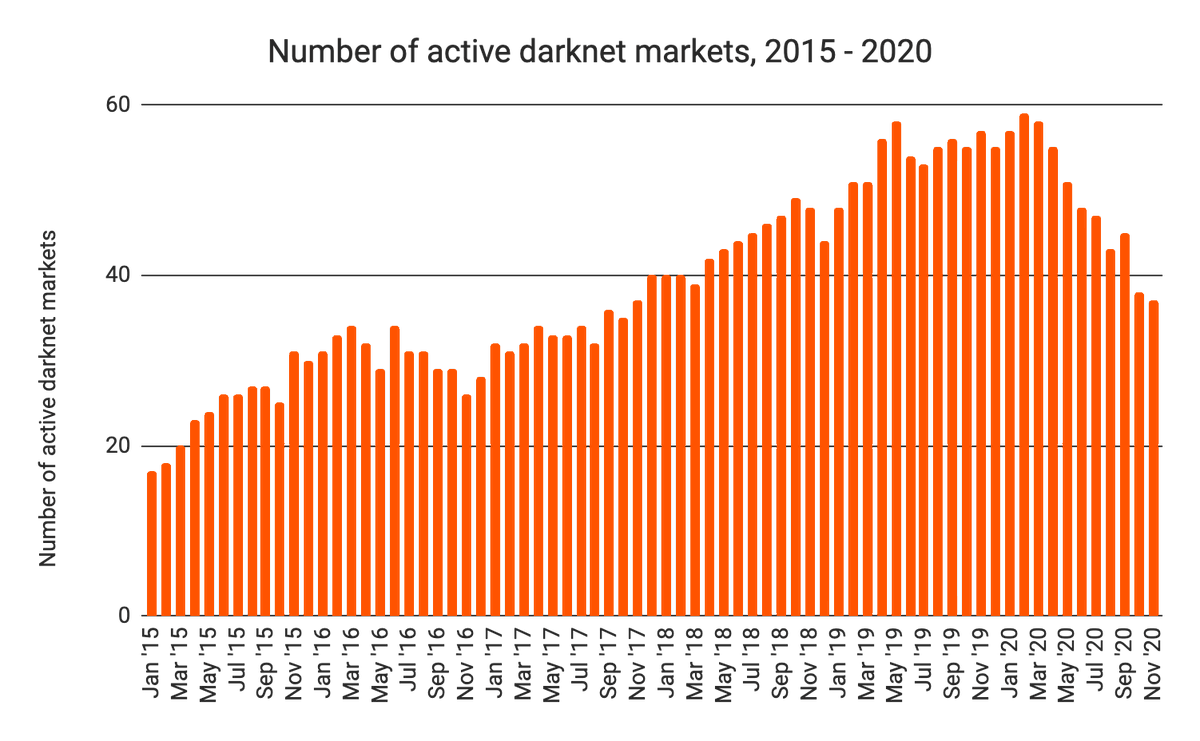
Darkmarket links often evoke a sense of curiosity and concern due to their association with illicit activities; however, there are legitimate contexts in which these links are utilized. Various organizations, including press agencies and non-governmental organizations (NGOs), sometimes access darkmarket platforms to monitor illegal markets, gather intelligence, and understand emerging threats. Such activities aim to combat crime, enhance cybersecurity, and promote public safety.
For press outlets, investigating darkmarket links enables detailed reporting on unlawful activities such as trafficking, counterfeit goods, or cybercrime schemes. By analyzing these markets responsibly, journalists can raise awareness and inform the public, ultimately supporting law enforcement efforts. NGOs may also engage with darkmarket links in controlled environments to conduct research or develop intervention strategies, assisting authorities in dismantling illegal networks.
It is important to note that the use of darkmarket links in these scenarios is conducted within legal and ethical boundaries, emphasizing transparency and the goal of reducing harm. Such legitimate activities contribute to a broader understanding of underground markets, help develop effective policy responses, and support ongoing efforts to ensure safety and security online.
Examples of Reputable Entities Using Darkmarket Links
Darkmarket links are often associated with illicit activities, but they can also serve legitimate purposes in specific contexts. Some cybersecurity professionals and researchers utilize these links to study cybercriminal behavior, track illegal marketplaces, and develop strategies to combat online threats. By analyzing darkmarket links, they can identify patterns, vulnerabilities, and operational methods used by malicious actors, contributing to enhanced cybersecurity measures.
Reputable organizations involved in law enforcement and digital forensics may access darkmarket links to gather intelligence on illegal operations. For instance, intelligence agencies might monitor these links to uncover criminal networks and disrupt illegal trading activities. Additionally, certain academic institutions may examine darkmarket links as part of research initiatives aimed at understanding online crime ecosystems and developing safer online environments.
While darkmarket links are inherently linked to illicit content, their study by credible institutions plays a crucial role in promoting digital safety and justice. Efforts to analyze these links should always adhere to legal standards, ensuring that investigations serve the public interest and do not inadvertently facilitate harmful activities. Recognizing the legitimate uses of darkmarket links is essential for a comprehensive approach to cybersecurity and criminal justice.
Identifying and Tracking Darkmarket Links
Identifying and tracking darkmarket links is a crucial aspect of cybersecurity and law enforcement efforts aimed at disrupting illegal online activities. Darkmarkets often utilize complex, anonymized websites to facilitate transactions involving illicit goods and services. Recognizing patterns and indicators associated with darkmarket links helps in monitoring these hidden networks effectively. For instance, some darkmarket links may be accessed through specialized networks or hidden services, making their detection more challenging. Maintaining awareness of such links, including resources like darkmarket links, is vital for cybersecurity professionals striving to combat illegal online activities and protect users from potential harm.
Techniques for Detecting Darkmarket Links
Identifying and tracking darkmarket links is a crucial aspect of cybersecurity and law enforcement efforts aimed at combatting illegal online activities. Darkmarkets often utilize encrypted and disguised links to facilitate illicit transactions, making detection a complex task that requires specialized techniques. One effective approach involves analyzing network traffic patterns to identify suspicious activity that may indicate the presence of darkmarket links. By monitoring for anomalies or unusual data flow associated with known darkmarket operations, investigators can pinpoint potential links that warrant further examination.
Another method for detecting darkmarket links involves examining the content and metadata of websites. Cybersecurity professionals often develop signatures or heuristics to recognize common traits of darkmarket sites, such as specific URL structures, hosting patterns, or obfuscated code. Regular updates to these detection techniques are essential, as darkmarkets frequently change their hosting strategies to evade detection. Additionally, social engineering and intelligence gathering play vital roles; by monitoring underground forums, chat channels, or other clandestine communication channels, analysts can uncover mentions or references to darkmarket links.
Advanced tracking may also employ automated tools and machine learning algorithms that analyze vast amounts of internet data to identify potential darkmarket links efficiently. These systems can learn to recognize emerging patterns and adapt to shifting tactics used by malicious actors. Combining technical analysis with human expertise often yields the best results, enabling authorities and cybersecurity teams to stay ahead of evolving darkmarket infrastructures while mitigating harm caused by illicit online activities.
Tools and Strategies for Monitoring Darkmarket Activity
Identifying and tracking dark market links is a critical component of cybersecurity and law enforcement efforts to combat illegal online activities. Darkmarkets often operate covertly, utilizing complex methods to hide their presence and evade detection. Effective monitoring requires a combination of technical tools, strategic approaches, and ongoing analysis to uncover and analyze these clandestine networks.
One of the primary strategies in tracking darkmarket links involves monitoring underground forums, marketplaces, and chat channels where illicit trade is discussed or promoted. Cybersecurity professionals often leverage specialized tools such as link scanners and darknet monitoring platforms to identify suspicious URLs associated with darkmarkets. These tools can analyze patterns, detect new entries, and flag links that may be linked to illegal activities.
Another effective method is the use of automation and data scraping techniques. Automated scripts can continuously scan forums, marketplaces, and social media platforms for references to darkmarket links. Once identified, these links can be cataloged and analyzed for patterns, such as common hosting providers or shared infrastructure, facilitating the attribution process.
Collaborating with internet service providers and cybersecurity firms can further enhance monitoring efforts. Sharing intelligence about darkmarket links helps create a broader understanding of their evolving tactics and infrastructure. Additionally, law enforcement agencies may use infiltration tactics and honeypots to lure and track darkmarket operators, gaining insights into their networks and operational methods.
For ongoing monitoring, using web crawling tools designed for deep web and dark web environments is essential. These tools can systematically explore hidden sites and identify new darkmarket links as they emerge. Ensuring diplomatic and legal compliance during these activities is paramount, especially when handling sensitive or potentially illegal content.
Ultimately, a multi-layered approach combining technical detection tools, strategic intelligence gathering, and inter-agency collaboration is vital for effectively identifying and tracking darkmarket links. This proactive stance not only disrupts illicit networks but also contributes to broader efforts to maintain cybersecurity and public safety. Vigilance and adaptability remain key in the constantly evolving landscape of darkmarket activity.
Law Enforcement Efforts to Disrupt Darkmarket Links
Identifying and tracking darkmarket links pose significant challenges for law enforcement agencies aiming to disrupt illicit online activities. These clandestine markets often utilize sophisticated obfuscation techniques to conceal their digital footprints, making detection difficult. Darkmarket links are typically shared through encrypted messaging platforms, forums, or hidden within malicious advertisements, requiring specialized investigative tools to pinpoint their locations. Effective strategies involve analyzing network traffic, monitoring dark web forums, and employing honeypots to lure and trace offenders. By understanding patterns in how these links are distributed and accessed, authorities can develop targeted approaches to disrupt the infrastructure of illicit marketplaces. Efforts to track darkmarket links are crucial in preventing the proliferation of illegal goods and services. Law enforcement agencies worldwide are continually refining methods to identify and monitor these links to dismantle the networks behind them.
- Using digital forensics to analyze leaked or captured data from suspected sources
- Monitoring encrypted communication channels for clues about link sharing
- Deploying sophisticated algorithms to recognize patterns associated with darkmarket activities
- Engaging in undercover operations to infiltrate and gather intelligence from these markets
- Collaborating internationally to share data and disrupt cross-border illicit transactions
Best Practices for Navigating Darkmarket Links
- Established in 2019, Russian Market is a well-known and highly regarded data store on the dark web, specializing in the sale of PII and various forms of stolen data.
- Since the organization behind it is independent, it’s fully user-supported and relies on donations to keep its site up and running.
- But you can face criminal charges if you use the dark web to engage in illegal activity, such as the sale or purchase of illegal firearms, drugs, pornography, stolen passwords, hacked credit card account numbers, or other illicit items.
- The Gray Web, Deep Web, and Dark Web are all valuable sources of threat intelligence, but many organizations limit their information-gathering efforts to the Surface Web.
- The concept known today as the Dark Web set its foundation in the early 2000s.
Navigating darkmarket links requires caution and awareness due to the inherent risks and potential legal implications involved. Understanding how to approach these links safely can help minimize exposure to malicious activities and protect your privacy. When encountering a darkmarket link, such as darkmarket link, it’s essential to use secure tools and best practices to ensure your safety online. Familiarity with hidden services and the proper precautions can make the process more secure and informed. For instance, exploring trusted sources or explicitly verified darkmarket links can provide a better experience and reduce vulnerability.
Security Measures for Users
Engaging with darkmarket links requires a high level of caution and awareness to protect your security and privacy. These illicit marketplaces often operate outside the boundaries of law and can expose users to significant risks including scams, malware, and legal consequences. To navigate these environments safely, it is essential to follow best practices that minimize potential harm. Always ensure your device has up-to-date security software and use strong, unique passwords for any accounts involved. Employing a secure and anonymous browsing method, such as virtual private networks (VPNs) and encrypted browsers, can help conceal your identity and location. Recognize suspicious links or offers that may be designed to deceive and avoid clicking on or sharing links like the darkmarket link, which can be a gateway to malicious content. Being cautious about the information you share and verifying the authenticity of any interactions are critical steps to safeguard your digital footprint. Adhering to these measures significantly reduces the likelihood of falling victim to scams or malicious activities often associated with darkmarket links. Ultimately, maintaining vigilance and employing robust security measures are essential components for anyone navigating these risky online spaces.
Cybersecurity Protocols for Organizations
Navigating darkmarket links requires a careful and informed approach due to the inherently risky and often illicit nature of these platforms. Organizations must prioritize cybersecurity protocols to protect sensitive data and mitigate potential threats associated with accessing or monitoring these links. Understanding the best practices for engaging with darkmarket links can help organizations maintain security while investigating suspicious activities or gathering intelligence.
For organizations involved in cybersecurity investigations, here are essential best practices when dealing with darkmarket links:
- Use Secure and Isolated Environments: Always access darkmarket links within a controlled, sandboxed environment such as a virtual machine. This isolates the activity from the main network, reducing the risk of malware spreading.
- Employ Robust Threat Detection Tools: Utilize advanced security tools and malware scanners to analyze any content or links related to the darkmarket, especially when testing or retrieving information from suspicious links.
- Enhance Network Monitoring: Continuously monitor network traffic for unusual activity when researching or engaging with darkmarket links like darkmarket link. This helps in early detection of potential breaches or malicious communications.
- Implement Strict Access Controls: Limit access to sensitive systems and data to authorized personnel only. Use multi-factor authentication to add an extra layer of security.
- Educate Staff on Risks and Protocols: Regular training is essential to keep staff aware of the dangers and proper procedures when dealing with darkmarket links, including recognizing phishing attempts or malicious payloads.
- Adopt Legal and Ethical Guidelines: Ensure all activities related to darkmarket links comply with legal standards and organizational policies, avoiding any illegal transactions or breaches of compliance.
Overall, a structured cybersecurity protocol combined with cautious navigation practices can significantly reduce risks associated with darkmarket links. Staying vigilant and following these best practices help organizations safeguard their assets and contribute to broader cybersecurity resilience.
Continuous Monitoring and Threat Intelligence Gathering
Navigating darkmarket links requires a strategic approach to ensure safety and security while accessing these hidden online spaces. Users must exercise extreme caution due to the illicit nature of many darkmarket platforms, which often host illegal transactions and activities. Employing best practices when interacting with darkmarket links can dramatically reduce exposure to threats such as scams, malware, and law enforcement surveillance.
Continuous monitoring is essential for maintaining safety in this environment. This involves regularly checking for updates related to darkmarket sites, such as changes in domain addresses or platform shutdowns. Staying informed about emerging risks and disruptions can help users adapt their strategies promptly and avoid becoming victims of malicious activities or infrastructure takedowns.
Gathering threat intelligence plays a critical role in understanding the evolving landscape of darkmarkets. This can include analyzing patterns of malicious behavior, identifying common scams, and recognizing indicators of compromise associated with specific links, such as darkmarket links. By leveraging threat intelligence, individuals and organizations can better anticipate potential dangers, refine their operational security measures, and minimize exposure to cyber threats.
Ultimately, navigating darkmarket links with a focus on best practices, continuous monitoring, and threat intelligence gathering can significantly enhance security protocols. This proactive approach helps to mitigate risks, protect personal and organizational data, and maintain awareness of the complex and dynamic environment of the darkweb.