Darknet Marketplaces Onion Address Structure
Darknet marketplaces operate on a concealed infrastructure designed to maintain user anonymity and security, with their onion addresses serving as the primary identifiers within this hidden web. Understanding the structure of a darknet markets onion address is essential for anyone navigating this clandestine environment. These addresses are typically generated using complex cryptographic algorithms, resulting in a string of seemingly random characters that form unique identifiers for each marketplace. For example, a typical darknet market onion address might look like this, which can be used to access various anonymous trading platforms. Framing these addresses correctly and securely is crucial to ensure safe and private browsing within the dark web ecosystem.
Overview of Onion Addresses
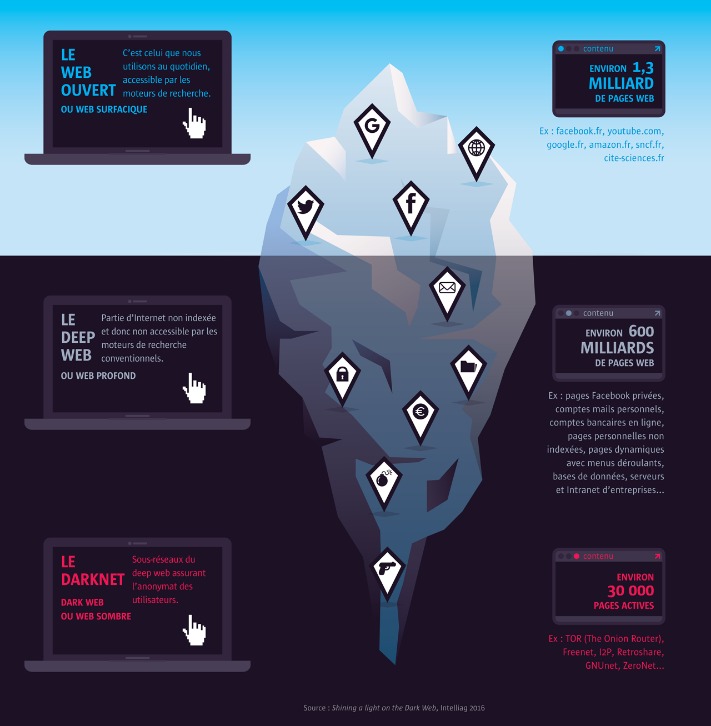
Darknet marketplaces operate on the hidden layers of the internet, providing a space for various goods and services that are often inaccessible through standard browsing. Central to their operation are onion addresses, which serve as unique identifiers for these secret platforms. These addresses are essential for maintaining anonymity and security within the darknet environment. Understanding the structure of onion addresses is crucial for users navigating darknet markets.
Onion addresses are distinguished by their characteristic format, which typically contains a series of random characters followed by the “.onion” suffix. The most common length of an onion address is 56 characters, though earlier versions may have 16 or 56 characters. The structure is designed to encode information related to the hidden service’s cryptographic keys, ensuring a secure and anonymous connection. This randomness helps to prevent traffic analysis and large-scale monitoring of these sites.
The composition of a darknet markets onion address begins with a string of alphanumeric characters, which are generated through a cryptographic process. This process ties the address directly to the specific hidden service, making it nearly impossible to spoof or counterfeit. Users must enter these addresses precisely, as even a slight error will lead to a non-existent or potentially malicious site. The security and privacy features embedded within the address structure play a vital role in the darknet ecosystem.
Overall, onion addresses in darknet marketplaces serve as both a locator and an identifier, ensuring that users can access these secretive platforms securely. Recognizing the structure and importance of darknet markets onion addresses is essential for anyone interested in understanding how these underground networks operate while maintaining user anonymity and data protection.
Format and Protocols
Darknet marketplaces utilize unique onion addresses to facilitate anonymous and secure transactions within their networks. These addresses are essential for accessing various hidden services and marketplaces on the Tor network, providing a layer of privacy that shields both vendors and buyers from detection. Understanding the structure, format, and protocols of darknet markets onion addresses is crucial for navigating this clandestine digital landscape safely and effectively.
Onion addresses used in darknet markets follow a specialized format designed to enhance privacy and security. These addresses are typically 16 or 56 characters long, consisting of random alphanumeric characters, followed by the “.onion” suffix. The shorter 16-character addresses are version 2, while the longer 56-character addresses are version 3, offering improved cryptographic security. These addresses function as the endpoints for accessing hidden services through the Tor network, ensuring that communications remain anonymous.
- Address Structure: The onion address is a hashed version of a public key, which ensures a secure and tamper-proof connection to a hidden service. The maximum length varies depending on the version, with version 3 addresses providing enhanced security and resistance to several types of attacks.
- Format: A typical onion address looks like a random string of characters, such as “abcdefghijklmnopqrstu1234567890abcdef.onion”. These addresses are not memorable by design but are cryptographically derived to ensure authenticity and security.
- Protocols: Darknet marketplaces predominantly use the Tor protocol to facilitate access to onion services. Tor provides an overlay network that anonymizes traffic, making it difficult to trace users or the hosting servers. The communication occurs over encrypted circuits, ensuring confidentiality and integrity of data exchanges.
Accessing a darknet market’s onion address requires configuring the Tor browser or a compatible network route that supports Onion routing. Once connected, users can browse, purchase, or sell products through these hidden marketplaces with a reduced risk of exposure. The onion address structure and the underlying protocols play a pivotal role in maintaining the anonymity and security features that characterize darknet marketplaces today.
How Onion Addresses Facilitate Anonymity
Darknet marketplaces operate within a hidden segment of the internet, often utilizing specialized addresses to maintain user privacy and security. Central to this infrastructure are onion addresses, which serve as unique identifiers for these clandestine sites. These addresses are essential for accessing darknet markets and are designed to facilitate a high level of anonymity for both users and operators. The structure of onion addresses typically consists of a 56-character alphanumeric string followed by the ‘.onion’ suffix, making them difficult to predict or track. This random-like configuration helps prevent third parties from easily discovering the site’s location or associating it with its real-world identity.
The complexity and randomness of darknet marketplaces onion address structure play a crucial role in protecting privacy. When users access these sites through the Tor network, their traffic is routed through multiple layers of encryption, further masking their location and activity. The unique addresses act as a digital fingerprint that enables users to connect securely without revealing their IP addresses. By leveraging such structures, darknet marketplaces can operate more discreetly, reducing the risk of detection by authorities or malicious actors. This design underscores the importance of onion addresses in maintaining the integrity and anonymity that define the hidden web ecosystem.
Accessing Darknet Markets via Onion Addresses
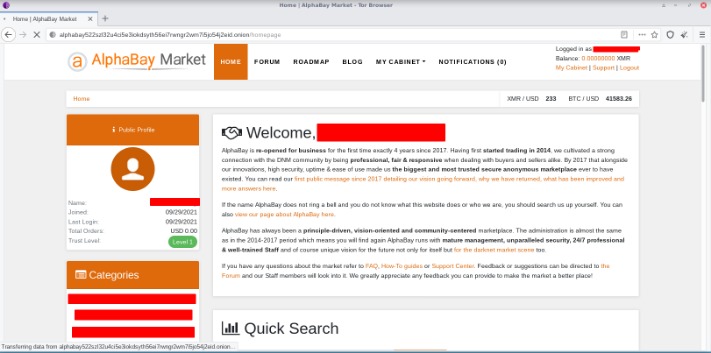
Accessing darknet markets requires understanding how to navigate their hidden infrastructure securely. These markets operate on the Tor network, utilizing special onion addresses that conceal both the location and identity of vendors and buyers. By using a Tor browser, users can access these anonymous marketplaces and explore a range of services and products. One essential aspect of this process is familiarizing oneself with trusted onion addresses, such as a reputable darknet market onion address, to ensure safe and reliable transactions. Always prioritize security and privacy when exploring these networks to avoid potential risks and scams.
Navigating the Tor Network
Accessing darknet markets through onion addresses involves connecting to specialized websites hosted on the Tor network, which provides users with anonymity and privacy. The Tor network, often referred to as “the dark web,” enables individuals to browse and access content without revealing their real IP addresses. Darknet markets operate exclusively on this network, utilizing unique onion addresses that are only accessible via the Tor browser. These addresses are typically long, alphanumeric strings ending with “.onion,” serving as site identifiers amid the hidden services.
To navigate the Tor network and access darknet markets, users must first download and install the Tor Browser, which is designed to route internet traffic through multiple relays, masking the user’s location and identity. Once connected to the Tor network, users enter the darknet market’s onion address into the browser’s address bar. It is crucial to verify the authenticity of match the official onion address to avoid scams or malicious sites. Many darknet markets also provide detailed guides for new users, emphasizing security practices such as using pseudonymous identities, avoiding personal information sharing, and employing additional encryption tools for communication.
While accessing darknet markets via onion addresses offers a degree of privacy, it is essential to remain cautious. The dark web hosts both legitimate and illicit activities, and navigating these sites carries inherent risks. Researchers and security experts advise users to adhere to best security practices and avoid engaging in any unlawful activities. Understanding how to properly and securely navigate the Tor network and darknet marketplaces can help users maintain their anonymity while browsing, but always with awareness of the risks involved. Discovering reliable onion addresses for darknet markets requires diligence and caution to ensure safe and secure access within this hidden online ecosystem.
Necessary Browser Configurations
Accessing darknet markets via onion addresses involves specific steps and configurations to ensure secure and anonymous browsing. These markets operate on the Tor network, which is designed to protect user privacy by anonymizing internet traffic through multiple relays. To access onion addresses safely, users must use specialized tools and follow best security practices.
First, a user should download and install the Tor Browser, a modified version of Firefox configured to connect to the Tor network. This browser is essential for accessing darknet markets with onion addresses securely. Once installed, launching the Tor Browser allows users to connect to the network seamlessly. When looking to visit a darknet market, such as a popular one with an onion address, ensure the URL is correct to avoid phishing sites or scams.
Prior to entering any market, it’s recommended to enhance security by adjusting certain browser configurations. Disabling scripts and plugins helps reduce vulnerability to malicious attacks. Additionally, using a VPN in conjunction with Tor can add another layer of privacy, although it is not mandatory. Always ensure that your device’s security software is up to date to prevent potential malware infections.
When accessing darknet marketplace onion addresses, it’s crucial to navigate carefully and avoid revealing personal information. Use pseudonymous credentials and consider maintaining separate identities for different activities. The darknet environment is inherently risky, so adherence to security best practices is essential for safeguarding privacy and assets. Proper browser configuration and cautious browsing enable safer exploration of darknet markets and their onion addresses.
Using Onion Addresses Safely
Accessing darknet markets through onion addresses allows users to explore hidden online marketplaces that operate on the Tor network, providing a layer of anonymity and security. These markets often utilize specialized onion addresses to conceal their locations, making it essential for users to understand how to access and utilize these addresses safely. The primary step involves installing the Tor Browser, which is designed to route internet traffic through the Tor network, effectively anonymizing your connection. Once the browser is set up, users can enter the specific onion address of a darknet market to access its platform. It is important to verify the authenticity of the market and their onion address, as numerous scams and fraudulent sites exist within the ecosystem. When browsing through onion addresses, avoid downloading unfamiliar files or providing personal data to minimize risks. Using a VPN in conjunction with the Tor Browser can further enhance privacy by encrypting traffic and masking your IP address. Remember to stay updated on security best practices, such as enabling multi-factor authentication and avoiding activities that could compromise your identity. By following these precautions, users can navigate the darknet markets via onion addresses more securely, ensuring a safer experience while maintaining your anonymity in these environments.
Locating and Verifying Onion Addresses of Markets
Locating and verifying Onion addresses of darknet markets is a crucial step for users seeking secure and anonymous access to these platforms. With the rise of the deep web, understanding how to identify authentic Onion addresses helps users avoid scams and malicious sites. Reliable verification involves cross-referencing multiple sources and ensuring the Onion address is official and active. For those interested in exploring various markets, visiting trusted directories or forums can provide direct links to verified Onion addresses, such as the darknet markets onion address http://abacusborncrffug2ytuqx3fczqbou4mrev56pfliv7ipjfi4uib7cad.onion. Ensuring the validity of these addresses is essential for safe browsing and transactions within the hidden web ecosystem.
Sources for Onion Addresses
Locating and verifying onion addresses of darknet markets is a crucial step for users seeking access to these hidden marketplaces securely and reliably. These markets operate on the Tor network, which provides anonymity and privacy for both buyers and sellers. To find trustworthy onion addresses, users often rely on community forums, encrypted communication channels, and trusted directories that share updated links. Since onion addresses can frequently change to avoid law enforcement detection or takedown, ensuring the authenticity of the address is vital. Verification methods include cross-referencing multiple sources, checking for active community discussions, and confirming the presence of recent activity on the listed onion site. A typical darknet markets onion address might be as simple as a string of alphanumeric characters ending with “.onion.” By staying informed through reputable sources, users can minimize risks and ensure they are accessing legitimate and secure markets. Always exercise caution when dealing with onion addresses, and verify their authenticity before proceeding with any transactions. Proper verification helps maintain safety and privacy in the complex landscape of the darknet.
Role of Market Forums and Darkweb News Sites
Locating and verifying onion addresses of darknet markets is a critical task for users seeking to access these hidden online marketplaces securely. These markets operate on the Tor network, utilizing onion addresses to maintain anonymity for both vendors and buyers. To find legitimate onion addresses of markets, users often rely on various online resources that compile current listings, although caution is essential to avoid scams and malicious sites.
Market forums play an influential role in the darknet ecosystem, offering a platform for community members to share updates, warnings, and verified onion addresses. By engaging with active and reputable forums, users can gain insights into the credibility of specific market addresses and stay informed about market availability or closures. These discussions help differentiate genuine onion addresses of markets from fraudulent ones designed to deceive users.
Darkweb news sites and reputable information portals also contribute significantly to the process of locating and verifying onion addresses. They regularly publish security updates, market shutdown notices, and new address listings, providing a curated source of trustworthy information. Users should cross-reference news reports with forum discussions to confirm the reliability of an onion address before attempting to access a market, reducing exposure to scams or malicious sites.
Overall, a combination of community-driven forums and dedicated news sites is essential for safely navigating the darknet markets’ onion addresses. Staying vigilant and verifying sources ensures a more secure experience when exploring these hidden marketplaces and helps users avoid potential risks associated with counterfeit or compromised onion addresses.
Methods to Verify Authentic Onion Links
Locating and verifying onion addresses of darknet markets is a critical step for users seeking secure and authentic access to these platforms. Due to the anonymous nature of the dark web, identifying genuine onion links requires careful attention and verification methods to avoid scams and malicious sites. Ensuring the authenticity of an onion address helps maintain security and privacy during browsing and transactions.

One effective way to locate legitimate darknet market onion addresses is through trusted community sources and forums. These platforms often share updated links and can help users avoid outdated or malicious addresses. Additionally, verifying onion links involves multiple steps to confirm their legitimacy and security. Users should be cautious when dealing with new or unverified links to prevent exposure to scams or malware.
- Check Multiple Sources: Cross-reference the onion address with reputable community forums, message boards, or trusted directories dedicated to darknet markets.
- Review Feedback and Comments: Read user feedback and reviews about the specific onion address or market to gauge its trustworthiness and operational status.
- Verify SSL/TLS Security: While traditional SSL certificates are not used on the dark web, ensuring the website uses typical security practices, such as onion service authentication, is important.
- Perform Hash Verification: Use checksum or cryptographic hashes if available to compare with official or known secure sources.
- Test Accessibility Safely: Use secure tools and methods to access the onion address, avoiding clicking on suspicious links or downloading unknown files.
By following these methods, users can improve their chances of accessing authentic darknet markets through verified onion addresses. This vigilance helps protect privacy and ensures a safer browsing experience in the complex landscape of the dark web.
Security and Safety Measures for Onion Market Addresses
Security and safety measures are of paramount importance when accessing and navigating darknet markets, particularly those hosted on onion addresses. These markets often involve sensitive transactions and private information, making robust protective protocols essential for users. Ensuring anonymity, encrypting communications, and verifying the authenticity of market platforms help mitigate risks associated with scams or malicious activity. It is advisable to rely on reputable sources and utilize secure browsing techniques to safeguard your digital footprint. For additional safety insights, consider exploring trusted onion sites such as darknet market onion addresses to understand best practices in maintaining security while engaging in online transactions on the dark web.
Importance of Secure Connections
- Each vendor selling within the marketplace displays the number of deals they have completed.
- After installation, you can use Tor to access the public internet as well as .onion websites.
- Watch our cyber team share their key insights from their investigations into the biggest dark web trends in 2022.
- All of this underscores Riseup’s prioritization of users’ rights over business interests.
- STYX Market focuses specifically on financial fraud, making it a go-to destination for cybercriminals engaged in this activity.
Ensuring security and safety on darknet markets, especially those utilizing onion addresses, is of paramount importance for both buyers and vendors. These markets operate in a context where anonymity and privacy are crucial, but without proper safeguards, users are vulnerable to various threats such as hacking, scams, and surveillance. Implementing robust security measures helps protect sensitive information and maintain the integrity of transactions on darknet platforms. By prioritizing security, users can confidently browse, buy, and sell within the ecosystem while minimizing potential risks.
One of the most essential security practices involves using secure connections when accessing onion market addresses. Utilizing the Tor network, which is designed to anonymize internet activity, ensures that users’ locations and activities remain hidden from outside observers. This layered encryption prevents eavesdropping and censorship, providing a safer environment for dealings. When connecting to an onion address, ensure the site employs HTTPS or similar encryption protocols to further secure communication channels. This prevents interception of data, maintaining confidentiality during transactions and interactions.
Regularly updating software, using strong passwords, and enabling multi-factor authentication are additional safety measures that contribute to a secure darknet market experience. Recognizing and avoiding phishing attempts and scams is equally vital for protecting assets and personal information. Moreover, genuine onion market addresses prioritize security features such as escrow services and open-source code audits, which enhance transparency and trust. Ultimately, maintaining secure connections and adhering to rigorous security protocols are critical in safeguarding users’ privacy and ensuring trustworthy operations within the darknet marketplace environment.
Preventing Phishing and Fake Onion Links

Cybersecurity measures are essential for safeguarding users and maintaining trust within darknet markets. The unique nature of onion addresses on the Tor network provides a level of anonymity, but it also requires additional security protocols to prevent malicious activities such as phishing and the spread of fake onion links. Implementing strict security practices helps ensure that users can access legitimate markets securely.
To prevent phishing attacks, it is crucial to verify the authenticity of onion addresses before visiting or transacting. Users should be cautious of links received through untrusted channels and avoid clicking on suspicious or unsolicited messages. Utilizing trusted sources and forums for confirmed onion addresses can significantly reduce the risk of falling victim to scams or fake sites. Recognizing the differences between legitimate onion addresses and malicious imitators is vital for safe browsing.
Market operators should employ robust security measures, including HTTPS encryption within the Tor network, to protect user data. Regular security audits and updates help identify vulnerabilities and reinforce the integrity of the marketplace. Additionally, employing multi-factor authentication and secure login procedures can defend against unauthorized access. Transparency about security practices builds user confidence and discourages malicious actors from impersonating legitimate onion addresses, such as the darknet markets onion address.
Education plays a crucial role in safety, encouraging users to stay informed about common scams and methods of securing their connection. By promoting best practices and being vigilant about link verification, darknet market users can minimize risks associated with phishing and fake onion links, maintaining a safer environment for all participants. Ultimately, a combination of technical safeguards and user awareness is key to safeguarding the integrity of onion market addresses and ensuring secure transactions.
Best Practices for Maintaining Anonymity
Operating a darknet market on the Tor network requires strict security and safety measures to protect both vendors and buyers, as well as to maintain the integrity of the platform. Given the sensitive and often illegal nature of darknet marketplaces, ensuring anonymity and safeguarding against potential threats are paramount. Proper security protocols help prevent hacking, law enforcement infiltration, and operational leaks that could compromise users’ identities and marketplace operations.
One of the most critical steps is to utilize a robust security infrastructure that prioritizes anonymity. Regularly updating software, using encrypted communications, and employing multi-factor authentication can significantly reduce vulnerabilities. Additionally, maintaining the marketplace’s onion address through a secure, isolated environment helps prevent unintended exposure of the site’s location and ensures ongoing accessibility via the Tor network.
- Use a dedicated, secure environment: Host the marketplace on a secure server with strong encryption and sandboxing techniques to prevent unauthorized access.
- Hide server details: Avoid revealing server information or software versions that could be exploited by attackers.
- Implement secure communication channels: Use encrypted messaging and data transfer protocols to protect user and marketplace interactions.
- Apply multi-layered authentication: Require multiple verification factors for admin access and user accounts to minimize potential breaches.
- Regularly update and patch software: Keep all software components up to date with the latest security patches.
- Rotate onion addresses periodically: Changing the onion address periodically enhances security by reducing exposure risk.
- Limit access permissions: Restrict internal access to sensitive data and controls, granting privileges only on a need-to-know basis.
- Monitor activity and logs: Continuously track marketplace activity for suspicious behavior or potential attacks.
Maintaining anonymity on a darknet market, especially one operating via an onion address such as the darknet markets onion address, requires a disciplined approach to security practices. Properly implemented, these measures help ensure the safety of all participants and the continuous operation of the marketplace within the boundaries of legal and safety considerations.
Market Operations and Onion Address Changes
Market operations within the context of the darknet involve managing various aspects of online marketplaces that often operate anonymously. A crucial component of these operations is the use of specialized addresses, such as onion addresses, which facilitate secure and private access to darknet markets. These addresses enable users to navigate marketplaces while maintaining anonymity, ensuring both security and confidentiality. Changes in onion addresses can occur for multiple reasons, including security upgrades or operational shifts, making it essential for users to stay informed to access the correct marketplace endpoints. For a comprehensive list of darknet market onion addresses, you can explore trusted sources that regularly update this information and provide secure access points such as an example marketplace onion address. Staying current with market operations and address changes is vital for safe and effective participation in these anonymous marketplaces.
Strategies for Address Rotation
Market operations on the darknet often involve managing stable access to onion addresses, which serve as the primary identifiers for marketplaces operating within the Tor network. Due to the inherently anonymous and decentralized nature of these markets, changes to onion addresses are common to ensure security, privacy, and operational continuity. Effective strategies for address rotation are essential for maintaining market stability and minimizing disruptions caused by law enforcement actions or network scanning activities.
Implementing a robust address rotation strategy involves understanding the risks associated with static onion addresses. Market operators should regularly update their addresses to prevent tracking and takedown attempts while maintaining user trust. This process includes planning transition periods, communicating changes securely to trusted vendors and customers, and ensuring that the new addresses are distributed carefully to prevent leaks that could compromise operational security.
- Establish a rotation schedule: Regularly changing onion addresses at predefined intervals helps reduce exposure. This schedule can be based on time or detected threats.
- Secure communication channels: Use encrypted messaging systems to inform trusted parties about address changes, avoiding public announcements that could attract unwanted attention.
- Implement seamless transitions: Ensure that redirection from the old address to the new one is possible temporarily to facilitate users’ access without interruption.
- Utilize multiple addresses: Maintaining several onion addresses allows operators to switch between them dynamically, distributing risk across multiple identifiers.
- Automate address management: Using scripts or tools to automate address updates and notifications decreases human error and enhances operational security.
For darknet market operators, understanding the importance of efficient address management and having strategic plans for onion address changes is crucial in safeguarding their operations and preserving user trust. With proactive address rotation, markets can mitigate risks associated with shutdowns or investigations, ensuring continuity and resilience in their market activities.
Escrow and Payment Address Management
Darknet markets operate through encrypted networks, often utilizing .onion addresses to ensure user anonymity and secure transactions. These specialized addresses serve as gateways to marketplaces that facilitate the exchange of goods and services beyond the reach of conventional authorities. Proper management of market operations requires a clear understanding of onion address changes, escrow procedures, and payment address handling to maintain trust and security within the community.
Market operators frequently update their onion addresses to enhance security or transition to new infrastructure. When an address change occurs, transparent communication with users is essential to prevent disruptions and ensure continued access. This involves securely redirecting traffic and verifying the new address before decommissioning the old one, minimizing the risk of phishing or malicious interference.
Escrow systems are a critical component of darknet market operations, providing an intermediary to hold funds until both parties fulfill their obligations. Managing escrow securely involves safeguarding the escrow addresses and monitoring transactions diligently. This process reduces fraud and enhances buyer and seller confidence in the marketplace.
Payment address management is equally vital, encompassing the handling of cryptocurrency addresses used for deposits and withdrawals. Properly generating, securing, and updating payment addresses ensures the integrity of transactions. Market creators typically rotate addresses regularly to prevent any potential compromise or tracing, adhering to best practices that protect user privacy and market stability.
Overall, effective management of onion address changes, escrow services, and payment addresses underpins the operational integrity of darknet markets. Ensuring these elements are handled securely and transparently fosters trust within the community and sustains the functionality of these encrypted marketplace environments.
Handling Market Seizures and Shutdowns
Darknet markets operate on the deep web using encrypted networks, primarily the Tor network, which allows users to access hidden services through .onion addresses. These markets frequently experience changes in their onion addresses due to security concerns, law enforcement actions, or operational decisions by market administrators. Such shifts can disrupt user access and impact ongoing transactions, making it essential for users to stay informed about the latest marketplace addresses and updates.
Market operations on the dark web are often unpredictable, especially when authorities target these platforms through seizures or shutdowns. When a darknet market is seized or forcibly shut down, it typically results in the loss of funds for many users and traders. Market operators may attempt to notify users of shutdowns or address changes through updated onion addresses or official communication channels, but such notices can be sporadic or unreliable.
Handling onion address changes involves monitoring trusted sources of information and community updates. Users rely on community forums, social media channels, and encrypted messaging services to receive the latest onion addresses and news regarding market status. It is crucial to verify the authenticity of these updates to avoid falling victim to scams or counterfeit sites that may emerge after a market shutdown.
In conclusion, effective management of marketplace operations and timely updates regarding onion address changes are vital for maintaining security and continuity in darknet market activities. Awareness and vigilance help users navigate the risks associated with market seizures and shutdowns, ensuring safer transactions on the dark web.
Law Enforcement and Onion Address Tracking
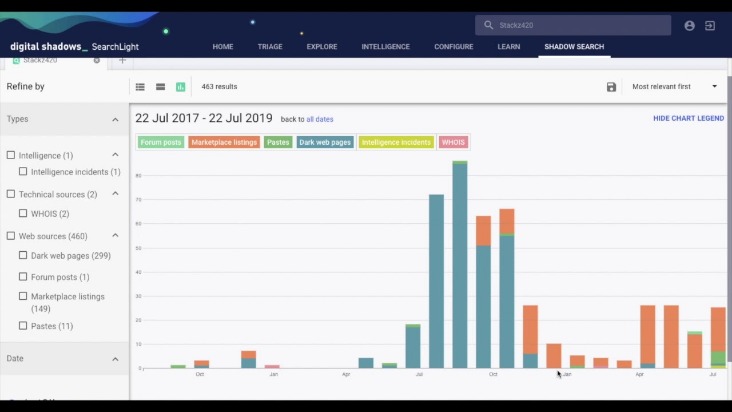
Law enforcement agencies face significant challenges when monitoring activities on the darknet, particularly when it comes to tracking onion addresses associated with underground markets. These encrypted networks are designed to preserve user anonymity, making it difficult to trace transactions and identify individuals involved in illegal operations. One of the key aspects of investigating darknet markets involves analyzing onion addresses, which serve as access points to these hidden platforms. The ability to identify and monitor onion addresses, such as those used for various darknet markets, is crucial for law enforcement efforts to combat illicit trade and disrupt illegal networks.
Techniques for Tracking Onion Addresses
Tracking onion addresses used by darknet markets presents significant challenges due to the inherent privacy features of the Tor network. Law enforcement agencies employ various specialized techniques to identify and monitor these concealed digital locations. One common approach involves analyzing publicly available information, such as marketplace leaks or user communications, which can sometimes reveal patterns or identifiers associated with specific onion addresses like darknet markets onion address. Additionally, investigators may utilize network analysis tools to detect traffic patterns or anomalies linked to hidden services.
Operational security measures taken by operators of darknet marketplaces often include using new onion addresses regularly, which complicates tracking efforts. To counter this, law enforcement may deploy infiltration strategies or work with cybersecurity companies to identify vulnerabilities. Techniques such as traffic correlation attacks, where they analyze entry and exit points of the Tor network, can sometimes expose the location or identity behind onion addresses.
Another method involves the exploitation of software vulnerabilities or server misconfigurations that expose gateway points to the hidden service. In some cases, physical or digital infiltration into infrastructure hosting these sites, or cooperation with service providers, can lead to breakthroughs in tracking onion addresses. Despite the complexities, ongoing advancements in cybersecurity and international cooperation continue to bolster law enforcement’s ability to trace and dismantle illicit activities associated with darknet markets and their onion addresses.
Risks Associated with Persistent Onion Links
Darknet markets operate on the basis of anonymity, utilizing onion addresses to facilitate secure and private transactions. While these encrypted addresses provide a layer of privacy for users, they also pose significant challenges for law enforcement agencies attempting to combat illegal activities. Tracking and shutting down these markets requires sophisticated technical expertise and persistent efforts, given the ever-changing nature of onion links. Darknet markets onion addresses are often designed to be temporary, but some persistent links remain active for extended periods, increasing the risks of illicit activities persisting online.
One major risk associated with persistent onion links is the potential for ongoing illegal transactions, such as the sale of drugs, stolen data, or counterfeit goods. These addresses can act as digital storefronts that operate covertly, making it difficult for authorities to identify or infiltrate them. Law enforcement agencies face the challenge of balancing privacy rights with the need to investigate criminal enterprises, which becomes even more complex when onion addresses stay active over time.
Another concern is that persistent onion links can undermine efforts to disrupt and dismantle darknet marketplaces. When these links are maintained or re-established quickly after takedown attempts, it prolongs illegal activities and complicates law enforcement efforts. Additionally, the use of onion addresses can facilitate the collection of digital evidence; however, the inherent privacy protections can also hinder investigations, creating a delicate balance between privacy and security.
Overall, the risks associated with persistent onion links in darknet markets highlight the ongoing struggle for authorities to effectively monitor and enforce laws within such anonymous environments. The evolving technology and the strategic use of onion addresses constitute significant obstacles in efforts to combat cybercrime and uphold legal standards in cyberspace.
Impact of Seizures on Market Accessibility
Darknet markets operating on the Tor network utilize onion addresses to ensure user anonymity and secure communication. Law enforcement agencies frequently target these markets to disrupt illicit activities, leading to various challenges related to tracking onion addresses and seizing servers. Such actions significantly impact the accessibility and operability of these markets, creating a complex landscape for both law enforcement and marketplace users.
Law enforcement agencies employ a range of tactics to track and identify onion addresses associated with illegal activities. These methods include network analysis, infiltration, and undercover operations designed to uncover the real identities behind the anonymized addresses. However, the robust encryption and decentralized nature of the Tor network often complicate these efforts, making it difficult to achieve continuous monitoring or pinpoint specific market locations.
The impact of seizures on marketplace accessibility is profound. When authorities successfully seize servers or disrupt services, it results in immediate market shutdowns, loss of customer trust, and disruption of supply chains. Such actions also influence user behavior, causing a shift to alternative platforms or temporary cessation of transactions. Importantly, these interventions can deter new users from entering the market while encouraging existing participants to adopt enhanced operational security measures.
- Disruption of illegal transactions and reduction of marketplace activity.
- Erosion of user confidence due to increased law enforcement scrutiny.
- Shift and proliferation of new onion addresses to evade detection.
- Potential destabilization of supply networks within the darknet ecosystem.
Ultimately, the ongoing cat-and-mouse dynamic between law enforcement and darknet markets underscores the importance of understanding how onion addresses function and the consequences of seizures. These efforts aim to diminish illicit activities, but they also influence the resilience and adaptability of darknet marketplaces, shaping the future of online anonymity and criminal enterprise management.
Decentralized Alternatives and Onion Addresses
Decentralized alternatives and Onion addresses have revolutionized the way individuals access and operate within the darknet marketplace ecosystem. These systems provide increased privacy and security, enabling users to browse and transact anonymously. Among the prominent features of these networks are .onion addresses, which serve as hidden portals to various darknet markets. For example, accessing a darknet markets onion address allows users to explore a wide range of goods and services while maintaining their anonymity. To discover more about secure and private marketplaces, you can visit this darknet markets onion address. The decentralized nature of these platforms ensures that no single entity controls the marketplace, promoting a more resilient and censorship-resistant environment for users worldwide.
OpenBazaar and Peer-to-Peer Market Platforms
Darknet markets operating on the Tor network utilize onion addresses to facilitate secure and anonymous transactions. These markets often leverage decentralized alternatives to traditional centralized platforms, offering users greater privacy and censorship resistance. Onion addresses serve as unique identifiers that enable access to hidden marketplaces without revealing physical locations or user identities, thus enhancing security for both buyers and sellers.
OpenBazaar and other peer-to-peer market platforms exemplify decentralized approaches that eliminate the need for intermediaries. These platforms enable direct transactions between users, fostering a peer-to-peer ecosystem that prioritizes privacy, censorship resistance, and control over personal data. By leveraging blockchain technology and decentralized hosting, these marketplaces aim to create more resilient and autonomous environments for secure trading activities.
The use of darknet markets onion addresses plays a crucial role in maintaining the anonymity and integrity of these decentralized platforms. Since they operate outside conventional oversight, onion addresses help users access these markets securely while minimizing exposure to potential surveillance or interference. As the landscape evolves, decentralized and peer-to-peer alternatives continue to grow in popularity, offering alternative pathways for conducting private transactions in a digital environment focused on privacy and security.
Onion Addresses in Decentralized Markets
Decentralized alternatives in the dark web offer a compelling alternative to traditional centralized markets, emphasizing privacy and resistance to censorship. These platforms operate without a single controlling entity, which enhances security for users seeking anonymity and protection from shutdowns. One of the key features of decentralized markets is the use of Onion addresses, which provide a layer of security by routing connections through multiple layers of encryption within the Tor network.
Onion addresses in decentralized markets serve as secure, anonymous entry points that help preserve user privacy and transaction confidentiality. These addresses are unique identifiers that direct users to specific marketplaces or services hosted within the Tor network’s hidden services. By utilizing Onion addresses, darknet markets can operate in a resilient manner, making it difficult for authorities or adversaries to disrupt their activities. Decentralized markets leveraging Onion addresses foster a more censorship-resistant environment, enabling users to access goods and services with greater anonymity.
One notable aspect of darknet markets with Onion addresses is their ability to maintain operational stability against attempts to shut them down. The decentralized architecture coupled with Onion routing ensures data is anonymized and distributed, reducing the risk of seizure or shutdowns. This setup makes Onion addresses a critical component for users seeking to engage with these platforms securely, ensuring that transactions remain private and identities concealed. Overall, Onion addresses in decentralized markets strengthen the foundation for secure and private interactions in the challenging landscape of darknet commerce.
Benefits and Limitations of Decentralized Onion Marketplaces
Decentralized alternatives and onion addresses play a significant role in the landscape of darknet markets, primarily offering users a more匿名 and secure environment for conducting transactions. These markets operate over the Tor network, utilizing onion addresses to obscure user identities and location data, thereby enhancing privacy and resistance to censorship. Decentralized darknet markets aim to reduce reliance on centralized servers, making them more resilient to shutdowns and takedowns. The use of onion addresses allows these platforms to maintain operational integrity, even in adversarial environments, by distributing data across multiple nodes.
One of the primary benefits of decentralized onion marketplaces is increased security. Since there is no single point of failure, these markets are less susceptible to hacking or government intervention. Additionally, the anonymity provided by onion addresses fosters privacy for both buyers and sellers, enabling confidential transactions. Decentralized architectures also promote censorship resistance, allowing the marketplace to continue functioning despite external pressures or attempts to shut down the platform.
However, there are limitations associated with these decentralized onion marketplaces. The lack of central oversight can lead to increased risks of scams, fraud, and illegal activities, as there are fewer mechanisms for accountability. Moreover, navigating decentralized markets can be technically challenging for inexperienced users, requiring familiarity with the Tor network and onion addresses. Despite their advantages, these platforms may also face legal challenges, as authorities continuously adapt their strategies to monitor and disrupt illicit online activities. While onion addresses provide significant privacy benefits, they are not entirely foolproof, and users must remain cautious when engaging with these marketplaces.