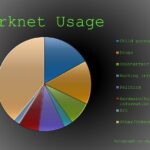
Understanding the Dark Web
The dark web is a hidden part of the internet that is not accessible through standard search engines or browsers. It is often associated with anonymous activities and serves as a platform for various online communities. Understanding the structure of the dark web, including darknet sites, helps to distinguish between malicious activities and legitimate uses such as privacy protection. Darknet sites are specialized websites that operate within this concealed network, offering a range of services and information while maintaining user anonymity. Exploring these sites provides insight into a complex digital landscape that is both fascinating and cautionary.
Definition and Characteristics of the Dark Web
The Dark Web refers to a concealed part of the internet that is not indexed by standard search engines and requires specific software or configurations to access. It is often associated with anonymous activities and hosts various types of content, including forums, marketplaces, and private communications. This hidden segment of the internet operates on overlay networks, which are layered on top of the surface web, providing heightened privacy and encryption for users. Darknet sites, a common component within the Dark Web, are specialized websites that utilize anonymizing technology to maintain user anonymity and secure transactions. These sites often operate using encrypted protocols, making tracking and monitoring difficult for outsiders.
The characteristics of the Dark Web include its decentralized nature, high level of anonymity, and the use of encryption tools that shield user identities and locations. It is distinguished from the Surface Web, which is accessible through standard web browsers, and the Deep Web, which contains unindexed but usually legitimate content such as private databases and personal accounts. The Dark Web, however, is often linked with illicit activities, including illegal trade, hacking forums, and other covert operations, although it also serves as a platform for privacy-focused communication and activism. Accessing darknet sites typically requires specialized software like Tor or I2P, which helps preserve the anonymity of users and site operators alike.
Differences Between the Dark Web, Darknets, and Deep Web
The dark web is a hidden part of the internet that operates separately from the surface web accessible through standard search engines. It is often associated with anonymous activities and can include a variety of sites, some of which are legitimate while others may involve illegal operations. Exploring the dark web requires understanding the distinctions between related terms such as the dark web, darknets, and the deep web, especially when considering darknet sites and their unique characteristics.
The dark web is a subset of the larger deep web, which encompasses all parts of the internet not indexed by traditional search engines. The deep web includes private databases, password-protected websites, and confidential information that isn’t intended for public access. In contrast, the dark web consists of encrypted networks and sites that require specific software, configurations, or authorization to access. Darknet sites are a common way to access content on the dark web, often utilizing specialized protocols to ensure anonymity and privacy.
Darknets are overlay networks that are built on top of the internet infrastructure, facilitating anonymous communication. They are designed to protect users’ identities and activity, making them popular for various purposes, including privacy-focused activities and illicit dealings. The Tor network is one of the most well-known darknets, hosting a range of websites known as darknet sites. These sites are often accessed through special browsers that route traffic through multiple relays to obscure users’ locations and identities.
Differences Between the Dark Web, Darknets, and Deep Web
- Deep Web: Comprises all internet content that is not indexed by search engines, such as private emails, banking pages, and confidential data. It is generally legal and includes benign or sensitive information not meant for public view.
- Dark Web: A small portion of the deep web that is intentionally hidden and accessible only through specific software like Tor or I2P. It hosts various sites, including darknet sites, often used for both legitimate privacy reasons and illegal activities.
- Darknets: Encrypted overlay networks that enable anonymous communication and browsing. They serve as the infrastructure for access to darknet sites and other hidden services. Darknets provide a platform where users can operate with a lower risk of surveillance or censorship.
Understanding these distinctions is essential when exploring the dark web and darknet sites. While many sites on the dark web offer privacy and secure communication, some are involved in illegal activities, making it crucial to approach this area with caution and awareness of legal boundaries. Overall, darknet sites serve as a critical component of the dark web, enabling anonymity for users seeking privacy, free speech, or niche communities.
Purpose and Uses of the Dark Web for Privacy and Anonymity
The dark web refers to a segment of the internet that is not indexed by standard search engines and requires specialized software to access. It exists within the broader deep web, which includes all web content not visible to traditional search engines. The dark web is often associated with anonymous communication and private activities, making it a place where users can browse, share information, and conduct transactions with a higher level of privacy. Darknet sites, which are specific websites accessible only through anonymity-preserving networks like Tor, serve as gateways to this hidden part of the internet.
The primary purpose of the dark web is to provide a space for privacy and anonymity. It is widely used by journalists, activists, and individuals living under restrictive regimes to communicate and share information without fear of censorship or persecution. For many users, the dark web offers a means to protect their identity and maintain confidentiality, especially when discussing sensitive or controversial topics. It also hosts darknet sites that cater to various interests, including marketplaces, forums, and information-sharing platforms, all designed to preserve user anonymity and security.
Additionally, the dark web is often utilized for legitimate purposes such as protecting whistleblowers, facilitating confidential communications, or ensuring privacy for vulnerable populations. However, it has also gained notoriety due to illegal activities, including illicit marketplaces, illegal trade, and cybercrime. Despite this, many users value the dark web for its role in safeguarding privacy and enabling free expression in environments where online safety is at risk. Overall, understanding the dark web highlights its dual role as a tool for both protection and potential misuse, emphasizing the importance of responsible and informed use of darknet sites.
Accessing the Dark Web
Accessing the dark web involves navigating a hidden part of the internet that is not indexed by traditional search engines and requires specialized tools to access. This section of the internet houses various sites, including darknet sites, which are often associated with anonymous communication and privacy-focused activities. Understanding how to safely and securely access these sites is essential for researchers, journalists, and individuals seeking privacy. By using a specific network such as the Tor network, users can explore onion sites that provide anonymity and security. To experience the dark web, some users may utilize portals to trusted darknet sites, ensuring they follow safety protocols and respect legal boundaries.
Required Software: Tor Browser and Its Functionality
Accessing the dark web, a hidden part of the internet not indexed by standard search engines, requires specialized software to ensure privacy and anonymity. One of the most popular tools for this purpose is the Tor Browser, which enables users to browse dark web sites securely and anonymously. Darknet sites often operate on the Tor network, which provides a layered encryption system to protect user identity and location.
The Tor Browser functions by routing your internet traffic through a series of volunteer-operated servers called nodes. This process, known as onion routing, encrypts and de-crypts data multiple times, making it extremely difficult for anyone to trace the activity back to the user. When accessing darknet sites, the Tor Browser provides a way to explore content that isn’t accessible through conventional browsers, often starting with “.onion” addresses that signify their presence on the Tor network.
While the dark web hosts legitimate content and serves as a platform for free expression and privacy advocacy, it also contains sites that are associated with illegal activities. Using the Tor Browser to access darknet sites offers a layer of privacy, but users should always exercise caution and adhere to legal guidelines. The software’s functionality ensures that users maintain anonymity, making it an essential tool for journalists, activists, and others seeking secure communication channels in sensitive environments.
Steps to Safely Enter the Dark Web
Accessing the dark web, particularly darknet sites, requires careful preparation and caution to ensure safety and privacy. The dark web hosts a variety of content accessible only through specialized software, which can be both a valuable resource and a risky environment. Understanding the proper steps to enter the dark web securely is essential for users seeking anonymity and protection from surveillance.
Follow these steps to safely access the dark web:
- Use a Secure and Trusted Device: Ensure your device is free from malware and up-to-date with the latest security patches. Avoid using personal devices for dark web activities to minimize the risk of exposing your identity.
- Install a Reliable VPN: Before accessing the dark web, connect to a reputable Virtual Private Network (VPN) to hide your IP address and encrypt your internet traffic. This adds an extra layer of security and anonymity.
- Download the Tor Browser: The most common tool for accessing darknet sites is the Tor Browser. Download it from the official website to ensure authenticity and prevent malicious modifications.
- Configure Security Settings: Once installed, adjust the security level to the highest setting, disabling scripts and plugins that could compromise your privacy. Be cautious with extensions or add-ons.
- Access Darknet Sites Carefully: Use known directories and search engines specialized for darknet sites to find reputable and safe links. Avoid clicking on unknown or suspicious links to reduce exposure to malicious content.
- Maintain Anonymity Throughout: Never provide personal information or engage in activities that could compromise your identity. Use pseudonyms and avoid logging into personal accounts while on darknet sites.
- Stay Informed About Risks: The dark web contains illegal and harmful content. Stay aware of the potential dangers, and avoid engaging with content or activities that infringe on laws or ethical standards.

By following these steps, users can navigate the dark web, including darknet sites, more safely and securely. While it provides access to a variety of information and communication channels, it is vital to prioritize privacy and caution during browsing to protect yourself from potential threats.
Enhancing Security: Combining Tor with VPNs
- Although primarily a surface web search engine, it can also access the dark web through its .onion site, making it a great choice for users who want to explore both the surface and dark web more securely.
- The dark web can help protect users’ privacy in ways the surface web often fails to do.
- Using DuckDuckGo over Tor will also let you see onion sites and normal pages in your search results.
- While not strictly a search engine, OnionLinks provides a directory-style resource that helps users discover various .onion sites across different categories.
Accessing darknet sites requires careful measures to ensure both safety and privacy. The darknet, a part of the internet not indexed by traditional search engines, is often accessed through specialized tools that obscure user identity. One of the most popular methods is using the Tor network, which anonymizes your internet traffic by routing it through multiple servers across the globe. This helps protect your identity when visiting sites on the dark web, making it difficult for third parties to track your activity.
Enhancing security while exploring the darknet involves combining the use of Tor with a reliable VPN service. A VPN encrypts all internet traffic before it reaches the Tor network, adding an extra layer of protection. This dual approach helps prevent your internet service provider from knowing that you’re accessing the dark web, and also shields your connection from potential eavesdroppers. When configured correctly, accessing darknet sites through Tor with a VPN ensures a higher level of anonymity and security, reducing exposure to malicious threats.
It’s important to exercise caution when navigating the dark web to avoid illegal activities and malicious content. Always keep your software updated, disable scripts for additional security, and be vigilant about the sites you visit. Using a combination of Tor and VPNs creates a safer environment for those exploring darknet sites, allowing users to maintain privacy and security in an environment where threats are prevalent. Proper precautions can help safeguard your digital footprint while accessing sensitive or private information on the dark web.
Dark Web Domains and Navigation
The dark web is a hidden part of the internet that requires specific tools and techniques to access. Domains on the darknet often utilize .onion addresses, which provide an extra layer of privacy and anonymity for both site operators and visitors. Navigating these sites can be complex due to their unique structure and the necessity of specialized browsers, such as Tor. For those interested in exploring darknet sites securely, it is important to understand how to access and identify legitimate domains, such as the darknet site. Proper navigation not only ensures safety but also helps in finding trustworthy resources within the clandestine online world.
Understanding .onion URLs and Their Structure
The dark web is a hidden part of the internet that is not accessible through standard search engines and requires specialized software to access. Darknet sites, often hosted on .onion domains, utilize unique URL structures that ensure privacy and anonymity for users and site operators. Understanding the structure and navigation of these URLs is essential for anyone exploring the darknet safely and responsibly. A key component of darknet site navigation involves recognizing the distinctive features of .onion URLs and how they are used to maintain privacy and security.
.onion URLs are a specialized type of website address used exclusively within the Tor network, which provides a layered approach to anonymity. These URLs typically consist of a 16- or 56-character alphanumeric string followed by the .onion suffix. The structure of these addresses is generated through cryptographic algorithms and serves as a sort of digital fingerprint for the site. This complexity makes them difficult to remember, which is why many darknet site operators use directory services or search tools within the Tor network to locate specific sites.
Navigation within the dark web mainly relies on:
- Direct URL Access: Users often access darknet sites by entering the exact .onion address into their Tor browser’s address bar.
- Indexing and Directories: Since search engines do not index dark web content, directories and forums often serve as guides to discover new sites and resources.
- Community Recommendations: Trusted communities and forums share links to reputable darknet sites, providing a roadmap for navigation.
Due to the encrypted and privacy-focused nature of the darknet, site structures and navigation methods are designed to prioritize anonymity. The complex, cryptographic structure of .onion URLs means users typically rely on trusted directories or community recommendations rather than traditional search engines. Navigating darknet sites requires understanding these URL structures and employing secure browsing practices to maintain safety and privacy at all times.
Tools for Searching Dark Web Content
The dark web represents a hidden part of the internet that requires specialized tools and knowledge to access. Darknet sites are often associated with anonymous communication and private transactions, making them both an intriguing and risky area for users. Navigating this concealed network involves understanding the unique domains and methods used to reach these sites securely.
Dark web domains typically use a variety of top-level domains, with .onion addresses being the most common for accessing darknet sites via the Tor network. These domains are not registered through traditional domain authorities and often feature randomized or specific alphanumeric addresses that enhance user privacy. Accessing a darknet site requires familiarity with Tor or other anonymity-preserving tools designed to mask user identities and locations.
To effectively search for content on the dark web, specialized tools and techniques are essential. Browsers like the Tor Browser enable users to connect to darknet sites securely. Additionally, there are specific search engines designed to index darknet content, providing more straightforward ways to find relevant information. These tools often compile directories, indexes, or summaries of available darknet sites, simplifying navigation in an environment that is inherently complex.
Navigation on the dark web can be challenging due to its decentralized and often unindexed nature. Users should exercise caution, verify the authenticity of sites, and use security measures such as VPNs and encrypted communication channels. Understanding how to locate and explore darknet sites safely is crucial for anyone seeking to understand this hidden segment of the internet.
Popular Dark Web Resources and Indexes
The darknet is a part of the internet that isn’t indexed by traditional search engines and requires special software to access. Within this hidden network, dark web domains operate on unique, often anonymous domain extensions that facilitate privacy and security for users. Navigating this environment can be challenging due to its concealed structure and the necessity of using tools like Tor browser. These tools help users reach darknet sites safely while maintaining their anonymity.
Popular darknet resources include marketplaces, forums, and information hubs that serve various purposes, from privacy-focused communications to illegal activities. Several indexes and directories exist to help users discover available darknet sites, organizing links and resources in ways that aid in exploration. These indexes serve as gateways, guiding users toward reputable and frequently visited sites, though caution is always advised given the potential risks associated with certain content.
Understanding how to navigate the dark web involves familiarity with its domain practices and indexing tools. Since many sites on the darknet operate under distinct domain extensions and may frequently change addresses, staying updated through trusted directories and community forums is crucial. While exploring, users should prioritize security measures to protect their anonymity and avoid malicious content, making the experience safer and more manageable. This knowledge about darknet site operations and resources helps users access valuable information while minimizing potential hazards.
Types of Content and Websites on the Dark Web
The dark web hosts a diverse array of content and websites that operate outside the mainstream internet, providing platforms for a variety of activities and information sharing. These sites range from private forums and marketplaces to encrypted blogs and resource hubs, often utilizing special browsers that ensure anonymity and privacy. Understanding the different types of content and websites on the darknet is essential for navigating this underground digital landscape securely. Some darknet sites, such as darknet sites, serve specific communities and purposes, highlighting the complex nature of this hidden internet realm. Whether seeking secure communication channels or exploring the shadow economy, users must be aware of the various site types and their functions within the darknet ecosystem.
Legitimate Uses: Journalism, Activism, and Privacy
The dark web hosts a wide variety of content and websites that serve different purposes, often operating beyond the reach of traditional search engines. These sites are accessed through specialized software such as Tor, providing a layer of anonymity for both visitors and operators. The types of content on the dark web range from illicit activities to legitimate endeavors, highlighting its complex nature. Understanding the different uses and the importance of these platforms helps demystify the dark web’s role in the digital landscape.
Some common types of content and websites found on the dark web include:
- Darknet Marketplaces: These are platforms where users can buy and sell goods, often illegal or restricted, such as drugs, weapons, or counterfeit documents.
- Private Forums and Communities: Spaces for discussion on sensitive topics, including political activism, privacy rights, and support groups for marginalized individuals.
- Whistleblower Platforms and Secure Communication Sites: Sites that enable anonymous reporting of misconduct or government wrongdoing, facilitating transparency and accountability.
- News and Journalism Outlets: Certain media organizations operate on the darknet to reach audiences in oppressive regimes or to protect sources’ identities.
- Research and Educational Resources: Resources dedicated to cybersecurity, cryptography, and digital privacy, used by researchers and enthusiasts.
While the dark web is often associated with criminal activity, it also serves legitimate purposes such as journalism, activism, and maintaining privacy. Many journalists utilize darknet sites to communicate confidentially with sources or publish sensitive information without risking exposure. Similarly, activists and human rights organizations leverage these platforms to protect their identities while advocating for change. Privacy-focused users rely on these sites to browse, communicate, and share information securely in regions where censorship or surveillance is prevalent. Overall, the dark web provides a vital space for free expression and safeguarding privacy, despite its notoriety for illicit activities.
Illegal Activities: Marketplace for Illicit Goods and Services
The dark web hosts a variety of websites that operate outside the reach of traditional search engines and standard internet infrastructure. These sites often fall into different categories based on their purpose and content. Among these, some are dedicated to illegal activities, creating a marketplace for illicit goods and services. Darknet sites like darknet site often provide platforms where users can buy and sell items that are prohibited or heavily regulated in many countries.
Various types of content can be found on the dark web, including forums, marketplaces, private messaging services, and information repositories. While many sites serve legitimate purposes such as privacy protection and anonymous communication, a significant portion are involved in illegal activities. These include drug trafficking, weapon sales, stolen data, counterfeit documents, and hacking services.
Markets on the darknet provide a wide array of illicit goods and services, making it a hub for traffickers and criminals. These marketplaces operate in a semi-anonymous environment, often using cryptocurrencies for transactions to enhance security and privacy. Such platforms facilitate quick, discreet exchanges that would be difficult to conduct on the surface web, thus fostering an environment conducive to illegal transactions.
The prevalence of illegal activities on these darknet sites raises numerous safety and legal concerns. Law enforcement agencies worldwide continually work to monitor and dismantle these platforms to combat crime and protect public safety. Nonetheless, the dark web remains a complex landscape where illegal marketplace transactions persist, driven by demand, anonymity, and the challenges of enforcement.
Examples of Dark Web Marketplaces and Services

The darknet hosts a wide variety of content and websites that serve different purposes, often operating anonymously and outside traditional internet regulations. These sites can range from informational resources to marketplaces and service providers, attracting users seeking privacy or unregulated services. Understanding the different types of content and websites on the darknet is essential for recognizing its diverse ecosystem.
Darknet sites can be categorized into several main types, including informational portals, marketplaces, service providers, forums, and illicit content platforms. Each serves a distinct function and caters to varying user needs. For instance, some sites provide news or educational material that is hard to access otherwise, while others facilitate commerce or communication under the cover of anonymity.
Some common examples of darknet marketplaces and services include:
- Marketplaces for Goods and Services: These platforms facilitate the trade of various products, from legal items like digital goods and software to illicit products such as drugs, stolen data, or firearms. They operate with strict anonymity protocols to protect buyers and sellers.
- Financial and Crypto Services: Including anonymous cryptocurrency exchanges, wallets, and escrow services that enable transactions without revealing identities.
- Communication Platforms: Encrypted messaging services and forums where users can discuss topics, share information, or coordinate activities securely and privately.
- Hacking and Cybercrime Services: Specialized sites offering hacking tools, tutorials, or assistance in illegal activities, often run by organized groups or individual hackers.
- Data Breach and Stolen Data Markets: Platforms selling sensitive information obtained through cyberattacks, such as login credentials, financial information, or personal identities.
Many darknet sites are designed to provide a level of anonymity and privacy that isn’t typical on the surface web, making them appealing for various activities, both legal and illegal. Whether for research, privacy protection, or illicit purposes, the dark web continues to evolve as a complex network of diverse sites and services.
Legal and Ethical Aspects of the Dark Web
The dark web presents a complex landscape where legal and ethical considerations are often intertwined. Operating within this hidden realm requires a nuanced understanding of the laws governing privacy, cybersecurity, and illicit activities. Many darknet sites serve legitimate purposes such as protecting whistleblowers or ensuring privacy for users in oppressive regimes, yet they can also host illegal transactions and content that challenge ethical boundaries. Navigating this environment responsibly involves awareness of the risks and responsibilities associated with engaging with darknet sites, emphasizing the importance of legality and morality in online conduct. For those interested in exploring this clandestine domain, accessing a reputable darknet site can provide insights into its structure and functions, such as through this darknet platform.
Legal Risks and Consequences of Dark Web Activities
The dark web, often associated with anonymous browsing and hidden marketplaces, presents a complex landscape of legal and ethical challenges. Engaging with darknet sites can expose individuals to significant legal risks, especially when illegal activities such as drug trafficking, weapon sales, or illicit data exchange are involved. It is essential to understand the legal boundaries and ethical considerations when exploring or dealing with content hosted on the dark web.
The use of darknet sites raises several legal concerns. Many activities conducted on these platforms, including the sale of illegal goods or services, are prosecuted under national and international laws. Law enforcement agencies continually monitor such sites to combat crime, and participation in illegal transactions can lead to severe penalties, including fines and imprisonment. Legal risks are heightened for users who inadvertently access or purchase illegal items, which can be considered complicity or conspiracy to commit a crime.
Ethically, the dark web presents dilemmas involving privacy, security, and morality. While some advocates argue that the dark web provides a safe space for whistleblowers, journalists, and dissidents under oppressive regimes, the proliferation of criminal activity undermines these noble intentions. Conducting activities on darknet sites without regard for legality or ethical standards contributes to a climate where illicit operations flourish, further complicating efforts to promote justice and safety.
- Engaging in illegal transactions
- Facilitating or supporting cybercrime
- Distributing illicit content
- Compromising personal or others’ security
The consequences of participating in dark web activities can be devastating. Individuals may face criminal charges, damage to reputation, and loss of privacy. Law enforcement agencies have advanced tools and international cooperation mechanisms to detect and prosecute illegal activities on darknet sites. Consequently, exploring or engaging with such sites carries a high risk of legal repercussions, emphasizing the importance of adhering to legal and ethical standards when using the internet.
Legitimate Reasons for Using the Dark Web
The dark web is a segment of the internet that is not indexed by standard search engines and requires specialized software to access, such as the Tor browser. While often associated with illicit activities, there are legitimate reasons for individuals and organizations to utilize the dark web, especially for protecting privacy and ensuring secure communications in sensitive situations.
From a legal and ethical perspective, accessing the dark web is not inherently unlawful. It becomes problematic only when it involves engagement in illegal activities such as trafficking, hacking, or illegal drug sales. Ethical considerations emphasize the importance of using the dark web for purposes that uphold privacy rights, safeguard free expression, and support journalism and activism in oppressive regimes.
Numerous organizations, journalists, and whistleblowers utilize darknet sites to communicate securely and share information without risking exposure. For example, investigative journalists may access darknet forums to gather intelligence or distribute sensitive reports while protecting their sources. Similarly, human rights organizations use darknet platforms to help vulnerable populations communicate safely and seek assistance without fear of surveillance or retaliation.
It is crucial to recognize that the dark web also plays a role in protecting privacy and facilitating free speech in environments where restrictions are severe. Engaging with darknet sites for these legitimate purposes aligns with ethical standards and complies with legal frameworks that safeguard privacy rights and prevent misuse of technology for malicious intents.
Risks Associated with Illegal Activities
The dark web, accessible through specialized browsers, provides a hidden layer of the internet where anonymity is prioritized. While this infrastructure supports privacy rights and confidential communications, it also facilitates a range of illegal activities that raise significant legal and ethical concerns. Engaging with darknet sites can expose users to unlawful behavior, including trafficking, cybercrime, and financial fraud, posing serious risks for those involved or affected.
Legal issues surrounding the dark web are complex, as many activities conducted through darknet sites violate national and international laws. Authorities continue efforts to investigate and shut down illegal operations hosted on these platforms, emphasizing the importance of complying with legal standards to avoid severe penalties. Ethical considerations also come into play, as the dark web’s potential for misuse can undermine trust in digital privacy and freedom, especially when it enables harmful activities or exploits vulnerable populations.
One of the primary risks associated with illegal activities on darknet sites is exposure to criminal networks engaged in trafficking, drug trade, and cyberattacks. Users or operators of these sites risk legal repercussions if they partake in or facilitate such activities. Additionally, covert illegal transactions often involve compromised financial or personal data, heightening concerns about identity theft and financial loss. For law enforcement, monitoring darknet sites is crucial to combating criminal enterprises and protecting public safety.
In conclusion, while the dark web offers avenues for privacy and freedom of expression, it also presents significant legal and ethical challenges. It is important for individuals to understand the risks linked to illegal activities on darknet sites and to adhere to legal standards to mitigate personal and societal harm. Maintaining awareness of these issues helps promote responsible use of the internet and supports efforts to combat unlawful conduct online.
Cybersecurity and Safety on the Dark Web
Cybersecurity and safety on the dark web are critical concerns in today’s digital landscape. The dark web, a hidden part of the internet accessible through specialized browsers, hosts a variety of anonymous marketplaces and forums, including darknet sites that often facilitate illicit activities. Users exploring this area must be cautious, as threats such as scams, malware, and data breaches are prevalent. Understanding how to navigate the dark web securely, including utilizing trusted resources and encryption techniques, can help protect personal information and reduce risks. For example, some darknet sites provide encrypted communication channels aimed at safeguarding user privacy and security. Staying informed and vigilant is essential for anyone venturing into or researching this clandestine segment of the internet to ensure online safety and cybersecurity integrity.
Common Threats and Scams Encountered
Darknet sites, often accessed through specialized networks such as the Tor network, are known for providing anonymous platforms for various activities. While these sites can be used for legitimate purposes like privacy protection and free expression, they are also frequently associated with cyber threats and scams. Users of darknet sites should be aware of the potential dangers to protect their cybersecurity and personal safety.
One common threat encountered on darknet sites is the presence of malicious actors engaging in illegal activities such as drug trafficking, weapon sales, and hacking services. These actors often utilize sophisticated methods to evade detection, making it difficult for law enforcement and users to identify malicious intent. Additionally, darknet sites are hotspots for scams, including fake marketplaces, phishing schemes, and fraudulent investment opportunities designed to steal sensitive information or money from unsuspecting visitors.
Another significant concern is the distribution of malware and viruses through darknet sites. These malicious programs can infect devices, leading to data theft, ransomware attacks, or device hijacking. Cybercriminals frequently deploy these tactics to maximize profit and maintain anonymity, which increases the risk for users who access darknet sites without proper security measures.
To safeguard against these threats, users should adopt robust cybersecurity practices such as using strong, unique passwords, enabling multi-factor authentication, and keeping software up to date. Recognizing common scams, avoiding suspicious links or downloads, and maintaining anonymity practices are vital steps when browsing darknet sites. Being vigilant and cautious can significantly reduce the risk of falling victim to cyber threats and scams prevalent on these anonymous platforms.
Protecting Personal Data and Identity
The darknet is a hidden part of the internet that operates on encrypted networks, making it difficult for outsiders to access or monitor. While it offers privacy and anonymity for users, it also presents significant cybersecurity risks, particularly concerning personal data and identity protection. Accessing or exploring darknet sites can expose users to malicious actors who seek to steal sensitive information or commit fraud. Therefore, understanding how to stay safe while navigating this shadowy online space is essential in safeguarding one’s digital identity.
One of the primary concerns related to the darknet is the prevalence of scams, malware, and illegal activities that can compromise personal data. Cybercriminals often use darknet marketplaces or forums to conduct illicit transactions, which can involve stolen credit card details, hacking tools, or personal information. Users must exercise caution and avoid sharing any personal or financial details on such platforms to prevent potential exploitation or identity theft.
Protecting personal data on the darknet requires the use of strong security practices. This includes employing robust, unique passwords, enabling two-factor authentication where possible, and utilizing Virtual Private Networks (VPNs) to anonymize online activity. It is also advisable to keep software and security tools up to date, reducing vulnerabilities that cybercriminals may exploit. Additionally, avoiding clicking on suspicious links and refraining from downloading files from unknown sources can help prevent malware infections that could compromise sensitive information.
Despite the anonymity that the darknet provides, users should be aware of the lurking dangers and the importance of cybersecurity vigilance. Employing encryption tools, maintaining strict privacy settings, and being cautious with the information shared online are crucial steps to defend against identity theft and data breaches. Remember, while the darknet can serve as a haven for privacy-focused individuals, it also attracts cybercriminals looking to exploit vulnerabilities.
In conclusion, navigating the darknet responsibly entails a thorough understanding of cybersecurity measures and a vigilant approach to personal safety. Protecting your identity and data from malicious actors on such platforms is vital in maintaining control over your digital presence and avoiding costly consequences associated with cybercrime.
Tools and Best Practices for Safe Browsing
Browsing the dark web requires a thorough understanding of cybersecurity and safety measures to protect your personal information and maintain anonymity. Darknet sites often operate outside the reach of conventional security protocols, making users vulnerable to malicious actors, scams, and data breaches. Ensuring safe browsing practices is essential for anyone exploring this hidden part of the internet, especially when visiting darknet sites that may host sensitive or illicit content.
To maintain security on the dark web, it is crucial to use specialized tools designed for anonymity and encrypted communication. Such tools include virtual private networks (VPNs), the Tor browser, and security-focused operating systems. These tools help conceal your location and online activity, reducing the risk of detection and interception by potential cyber threats.
Best practices for safe browsing include avoiding the download of suspicious files, not sharing personal information, and being cautious with links and attachments. Regularly updating software and security patches is also vital to protect against emerging vulnerabilities. When accessing darknet sites, always verify the authenticity of the site to prevent falling victim to scams or phishing attacks. Remember, security begins with awareness and cautious browsing behavior.
Here are key tools and practices to enhance cybersecurity on the dark web:
- Use the Tor browser for anonymous access to darknet sites while maintaining privacy.
- Utilize VPN services in conjunction with Tor to add an additional layer of security.
- Employ security-focused operating systems like Tails or Qubes OS for safer browsing environments.
- Maintain updated antivirus and anti-malware software to detect and prevent malicious threats.
- Implement strong, unique passwords for different accounts and enable two-factor authentication whenever possible.
- Avoid sharing identifiable or sensitive information on any darknet site.
- Be vigilant about the links you click and the files you download from darknet sites, especially those that seem suspicious or unverified.
Practicing these cybersecurity measures can significantly reduce risks and help ensure safe browsing experiences on the dark web, allowing users to explore darknet sites confidently while protecting their digital footprint and personal safety.
Monitoring and Protecting Personal Data
Monitoring and protecting personal data is a critical component in maintaining privacy and security, especially within the context of darknet sites where sensitive information may be exposed. Darknet platforms, often associated with anonymous transactions and communications, require heightened vigilance to prevent data breaches and misuse. Ensuring robust security measures and vigilant oversight can help safeguard user information from malicious actors. For those seeking reliable resources on darknet security, exploring trusted sites like Nexusafe can provide valuable insights and protections. Recognizing the importance of monitoring and active defense can significantly reduce risks associated with personal data exposure in these complex online environments.
Dark Web Data Breach Monitoring Solutions
Monitoring and protecting personal data in today’s digital landscape is more critical than ever, especially with the increasing prevalence of data breaches on darknet sites. Darknet site activities often involve illegal trading of sensitive information, making it essential for individuals and organizations to be vigilant in safeguarding their private data. Implementing robust data breach monitoring solutions can help detect unauthorized disclosures early, minimizing potential damage.
Darknet data breach monitoring solutions utilize advanced scanning and alert systems to identify compromised personal information across various underground platforms. These tools continuously scan dark web forums, marketplaces, and other clandestine networks for leaked credentials, financial details, or health records. Once a breach is detected, immediate action can be taken to change passwords, notify affected users, and reinforce security measures.
Effective protection of personal data involves not only monitoring but also proactive measures such as encryption, multi-factor authentication, and regular security audits. Organizations should also educate employees on cybersecurity best practices to reduce the risk of breaches originating from phishing or malware attacks. By integrating comprehensive darknet site monitoring solutions, entities can stay ahead of potential threats and respond swiftly to data breaches before they escalate.
Specialized darknet site monitoring services often include dark web surveillance tools that scan for specific keywords related to an individual’s or company’s data. This targeted approach ensures rapid identification of relevant threats, enabling timely intervention. Staying vigilant against dark web activities is vital for maintaining trust and security in an increasingly interconnected digital economy.
Indicators That Personal Data Has Been Compromised
Monitoring and protecting personal data is crucial, especially when dealing with the risks associated with darknet sites. These clandestine parts of the internet often host malicious activities where personal information can be targeted for theft or misuse. Implementing robust security measures and continuous monitoring helps safeguard sensitive data from unauthorized access or breaches.
One of the key indicators that personal data has been compromised includes unexpected notifications of data breaches or alerts from security tools. These can manifest as increased login attempts, unfamiliar login locations, or sudden account lockouts. Additionally, recipients might notice spam emails, phishing attempts, or fraudulent activities linked to their personal identity, signaling potential misuse of their data.
Darknet sites pose unique challenges in monitoring data security due to their anonymous nature, but vigilance remains essential. Signs that a breach has taken place may also include unexplained changes to account information or suspicious activities on financial accounts linked to the compromised data. Regularly reviewing access logs, utilizing intrusion detection systems, and being alert to unusual patterns are effective strategies to identify early signs of compromise.
Protecting personal data requires not only technological defenses but also awareness of emerging threats within the dark web where stolen information often appears for sale or dissemination. If you suspect that your data has been compromised on a darknet site or elsewhere, immediate action such as changing passwords, enabling two-factor authentication, and monitoring financial statements can help mitigate damage and prevent further exploitation.
Steps to Take If Data Is Found on the Dark Web
Monitoring and protecting personal data is essential in today’s digital landscape, especially with the increasing presence of darknet sites where illegally accessed information may be bought and sold. Being proactive about data security can help minimize risks and safeguard your identity from malicious actors.
One of the first steps to protecting personal data is to regularly check whether any of your information has been compromised. Use reputable monitoring services that track data breaches and alert you if your details, such as email addresses, passwords, or social security numbers, appear in known breach databases or on concealed darknet sites. This early detection enables swift action to prevent further misuse.
If you discover that your personal data is found on a darknet site, immediate steps should be taken. Change your passwords for affected accounts and enable two-factor authentication where possible to add an extra layer of security. Notify your financial institutions and relevant authorities if sensitive financial information has been compromised.
It is also advisable to place fraud alerts or credit freezes with credit bureaus to prevent identity theft. Monitoring your financial statements and credit reports regularly can help detect unauthorized transactions or activities. Consider reaching out to cybersecurity professionals who specialize in dark web monitoring to comprehensively assess the scope of the breach and receive tailored advice.
Protecting your personal data from the dark web is an ongoing process that includes practicing good digital hygiene, staying informed about emerging threats, and taking rapid action if your information surfaces on dark web marketplaces. Being vigilant helps you maintain control over your personal information and minimizes potential harm from cybercriminal activities.
Conclusion: Navigating the Dark Web Safely and Responsibly
Exploring the darknet can be a complex and often risky endeavor, requiring careful navigation and a strong understanding of safety practices to ensure personal security. Navigating these anonymous networks demands awareness of potential threats, such as malicious actors or illegal content, and taking appropriate precautions to avoid harm. When engaging with **darknet sites**, it’s crucial to use secure tools like specialized browsers and employ end-to-end encryption to safeguard your identity and information. Additionally, staying informed about the latest security updates and best practices can help users avoid common pitfalls and unauthorized data exposure.
For those seeking to explore this hidden part of the internet responsibly, it is advisable to start with reputable sources and avoid sites that promote illegal activities. There are legitimate reasons to access parts of the darknet, such as protecting privacy or accessing information censorship in oppressive regimes. As with any online activity, practicing caution and skepticism is essential. Consulting comprehensive guides on darknet safety can significantly reduce risks and help maintain a secure browsing environment. For example, you might find it helpful to check out resources or communities dedicated to secure darknet browsing, such as trusted darknet marketplaces(http://xv3dbyu75coadsrwlbofnsg3dj5axfzcxh5v4nrvtcn3ey7uv6vrf5yd.onion), which emphasize responsible usage and safety protocols.
In conclusion, navigating the darknet safely and responsibly involves prioritizing security, staying informed, and maintaining ethical practices. While exploring these networks can offer valuable insights and privacy benefits, it must be done thoughtfully and cautiously to protect oneself from potential risks. Knowledgeable users who follow best practices and remain vigilant can uncover valuable information while minimizing exposure to dangers associated with the darknet. Always remember: responsible browsing is key to a safe experience in this clandestine and often unpredictable digital realm.