Understanding Darknet Sites
The Darknet refers to a hidden part of the internet that is not indexed by traditional search engines and requires special software, configurations, or authorization to access. Darknet sites are often associated with anonymous communication and serve various purposes, from privacy-focused browsing to illicit activities. Understanding the nature of these sites is essential for recognizing their role in online security and privacy. Some darknet sites provide secure channels for journalists, activists, and whistleblowers to communicate safely, while others are exploited for illegal transactions. Exploring the structure and purpose of darknet sites can help users navigate this complex and often misunderstood digital space.
Definition and Accessibility
Darknet sites are websites that operate on overlay networks, which are intentionally hidden from standard search engines and typical browsing methods. These sites provide a layer of secrecy and security, often used for private communications, confidential transactions, or illicit activities. Their unique nature stems from the use of specialized software that enables access to these hidden networks, making them fundamentally different from regular websites.
Accessing darknet sites requires specific tools and knowledge, as they are designed to be difficult to find and reach through conventional web browsers. These sites often use encrypted and anonymized protocols to protect both the operators and users, ensuring privacy and reducing the risk of surveillance. Consequently, understanding how to access them and what they entail is essential for researchers, security professionals, or individuals interested in digital privacy.
The accessibility of darknet sites is limited by their underlying architecture and security measures. Typically, these sites are hosted on the Tor network or similar platforms, which provide anonymity by routing traffic through multiple servers worldwide. This layered encryption helps hide the true location of the sites and their visitors, making them resistant to censorship and monitoring. However, this also means that their content, while diverse, can include both legitimate activities and illegal enterprises.
Darknet sites can be characterized by the following features:
- Operated on hidden overlay networks using specialized software such as Tor or I2P.
- Designed to maintain user anonymity and site confidentiality.
- Often accessed through specific browsers configured to connect to these networks.
- May host a wide range of content, from privacy-focused forums to illegal marketplaces.
- Require knowledge of their domain or address, which is not available through mainstream search engines.
Understanding darknet sites is crucial for comprehending the broader landscape of internet privacy, cybersecurity threats, and the challenges posed by anonymous online environments. While they can serve legitimate purposes like secure communication for activists or journalists, they also pose risks due to their association with illicit activities. Awareness of their nature and accessibility helps in developing effective strategies for monitoring and safeguarding online security.
Use of Encrypted Browsers
The darknet is a part of the internet that is not accessible through traditional web browsers and requires specialized software to access. Known for its anonymous nature, it hosts a variety of sites that operate outside the reach of standard search engines and authorities. These darknet sites often serve as hubs for private communications, illicit activities, or information exchange, making them a subject of curiosity and concern for many online users.
Accessing darknet sites typically involves the use of encrypted browsers such as Tor or I2P, which provide enhanced privacy and anonymity. These browsers work by routing user traffic through a network of volunteer-operated servers, obscuring the user’s location and activity from potential surveillance. This encryption helps users protect their identities, especially when visiting sites that require a high level of anonymity or when discussing sensitive topics.
The use of encrypted browsers is crucial for maintaining security and privacy when navigating the darknet. They not only prevent tracking but also help protect users from potential surveillance or cyber threats. However, this same level of anonymity has led to concerns about illegal activities occurring on darknet sites, prompting ongoing discussions about balancing privacy rights with measures to prevent crime.
Understanding darknet sites and the use of encrypted browsers is essential for appreciating the complexities of online privacy and security. While they serve legitimate purposes for activists, journalists, and privacy-conscious individuals, they also pose challenges for law enforcement and cybersecurity. As technology advances, the importance of responsible usage and awareness of the risks associated with these platforms continues to grow.
Purpose and Functionality
Darknet sites are hidden parts of the internet that are not accessible through standard search engines or browsers. These sites operate on overlay networks, utilizing specialized software such as Tor or I2P to maintain user anonymity and site confidentiality. The primary purpose of darknet sites varies widely, ranging from maintaining privacy for journalists and activists to facilitating illegal activities. Despite their association with illicit endeavors, many legal and ethical uses exist, such as secure communications for whistleblowers or individuals in oppressive regimes.
The functionality of darknet sites relies heavily on encryption and anonymization techniques that obscure both the user’s identity and the server’s location. This level of privacy makes them a significant tool for sensitive communications but also attracts malicious actors. Darknet sites are often structured similarly to standard websites, with web pages and assets stored on hidden servers, but they are accessible only through specific networks and configurations. Their purpose extends beyond anonymity, offering platforms for secure message exchange, private transactions, and free expression where censorship or surveillance is prevalent.
Understanding darknet sites involves recognizing their dual nature: they serve as vital spaces for privacy-conscious users and a haven for illegal activities. Their design and operational principles emphasize security, anonymity, and resilience against shutdown efforts. As such, they present both opportunities and challenges in areas like cybersecurity, law enforcement, and digital rights. Awareness of their purpose and functionality is crucial for navigating the broader landscape of the internet’s hidden corners safely and responsibly.
Characteristics of Darknet Sites
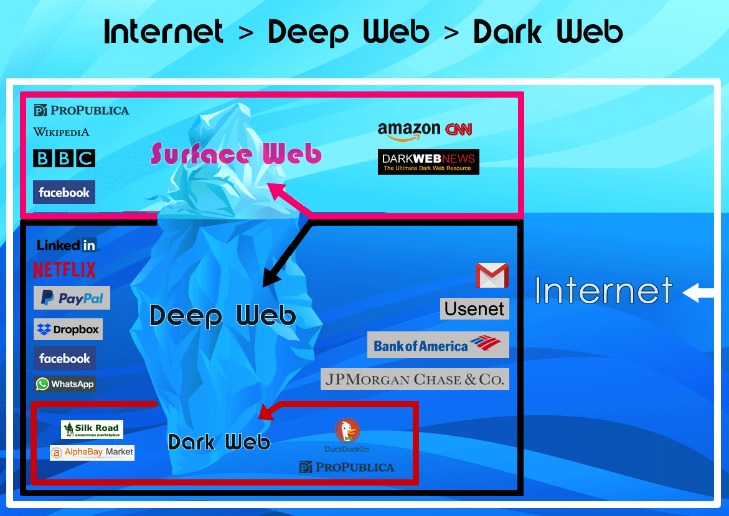
- Many also conflate the deep and dark web, which are entirely different in structure.
- Learn how Peraton continues to do the can’t be done and drive mission success on Earth and beyond on the Everyday Extraordinary podcast.
- Knowing how to safely use Tor means using it alongside other cybersecurity tools, so set up a VPN to benefit from end-to-end encryption.
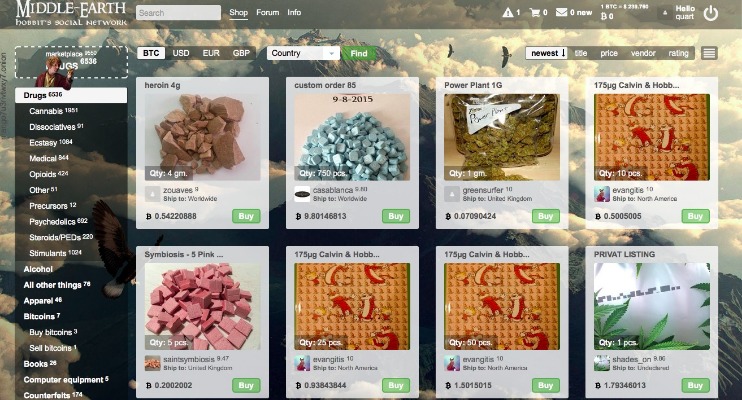
- Darknet websites look very similar to any other website but there are some key differences.
- In another infamous case, the administrator of the dark web-based Playpen child pornography site was sentenced to more than 30 years in jail.
Darknet sites are a distinct category of websites that operate on encrypted networks, often hidden from traditional search engines and accessible only through specific software. They are characterized by their anonymity features, including encryption, anonymizing networks, and specialized access methods. These sites frequently host a variety of content and services that are not easily found on the surface web, making them a unique digital landscape. For those exploring or researching the darknet, understanding the characteristics of these sites, including their structure and security protocols, is essential. Some darknet sites, such as those accessible via secure onion addresses, provide platforms for private communication, marketplaces, or data exchanges.
Deliberate and Private Nature
Darknet sites are specialized online platforms that operate within a hidden part of the internet, often utilizing anonymizing technology to conceal their identities and locations. These sites are characterized by their deliberate efforts to maintain privacy and security for both operators and users. Such sites are frequently accessed through tools that enable anonymous browsing, making it difficult to trace activities or identify participants.
One defining characteristic of darknet sites is their deliberate design to be private and untraceable. This privacy-centric approach ensures that conversations, transactions, and exchanges of information remain confidential. Many of these sites are built to resist surveillance and censorship, providing a secure environment for various activities that might be restricted or monitored elsewhere.
The nature of darknet sites often involves a focus on privacy, anonymity, and security, which shapes their content and the interactions that occur within them. While some serve legitimate purposes such as secure communications for journalists or activists, others may be involved in illicit activities. Regardless of their purpose, the private and deliberate architecture of these sites is what makes them notable in discussions about internet security and privacy.
Unindexed and Hidden
Darknet sites are a unique subset of online platforms that operate outside the traditional surface web, making them difficult to access and discover through standard search engines. These sites are often characterized by their use of specialized networks, such as the Tor network, which provide users with increased anonymity and privacy. As a result, many darknet sites remain unindexed by mainstream search engines, rendering them hidden from ordinary users and difficult to locate through conventional means.
One defining characteristic of darknet sites is their anonymity-focused architecture. They typically employ encryption and routing techniques that obscure both user identities and location data, ensuring that activities on these sites are difficult to trace. This anonymity, however, also means that such sites are less likely to be included in search engine indexes, contributing to their unindexed status. Consequently, access to these sites often involves knowledge of specific addresses or directories, rather than relying on search engine queries.
Another important aspect of darknet sites is their hidden status. Unlike most websites, which are stored on publicly accessible servers and indexed by search engines, darknet sites are intentionally concealed. They often use encrypted domain names or non-standard top-level domains that are not recognized by typical DNS lookup services. Their hidden nature makes it challenging for search engines to discover or crawl these sites, which is why they are typically categorized as unindexed or invisible to the general web audience.
Overall, the characteristics of darknet sites—such as their prioritization of privacy, use of specialized networks, and intentional concealment—make them fundamentally different from surface web websites. While this design facilitates anonymity and secure communication, it also results in their unindexed and hidden status, limiting their visibility to the broader online community. Understanding these features is essential for recognizing the unique landscape of the darknet and its applications.
Frequent Content Changes
Darknet sites are unique online platforms that operate within a hidden segment of the internet, often accessed through anonymizing networks such as Tor. These sites are characterized by their emphasis on privacy and anonymity, making them popular for both legitimate activities and illicit operations. One notable characteristic is their frequent content changes, which serve to enhance security and avoid detection by authorities. This constant fluctuation of content can make these sites difficult to track or archive, as their pages and information are regularly updated or replaced.
Another important feature is the use of dynamic content that adapts to different users and circumstances, often employing automated scripts and plugins to manage the frequent updates. Darknet sites tend to have a decentralized and fluid structure, enabling operators to modify, hide, or移除 content with ease, ensuring continued operational security. The rapid content changes also contribute to a sense of flux within these networks, making them resilient against shutdown efforts and enabling users to access fresh information or resources regularly.
Overall, the combination of strong privacy measures and continual content updates makes darknet sites a complex and evolving part of the internet landscape. While they can facilitate criminal activities, they also serve as platforms for privacy-focused communication and information sharing in a world increasingly concerned with digital privacy and security.
Activities on Darknet Sites
Darknet sites are hidden corners of the internet that operate outside the reach of conventional search engines and mainstream web browsing. They are often associated with a range of activities, both lawful and unlawful, due to their anonymity-preserving features. Users access these sites through specialized software and networks, providing a layer of privacy that can be exploited for various purposes. Understanding the various activities on darknet sites is essential for recognizing both the risks and potential benefits associated with these platforms. Some darknet sites, such as Nexusafe, are dedicated to legitimate privacy-focused exchanges, while others cater to more illicit transactions. The complex landscape of darknet activities underscores the importance of awareness and caution when exploring these hidden online realms.
Legitimate Uses
The darknet consists of a part of the internet that isn’t indexed by traditional search engines and requires specialized software or configurations to access. While often associated with illicit activities, many legitimate uses also take place on darknet sites. These platforms provide a secure environment for privacy-conscious users, journalists, activists, and researchers to communicate safely and share information without exposing their identities or locations.
One common activity on darknet sites involves securely exchanging sensitive information, such as political dissent or whistleblowing documents, which can be crucial in oppressive regimes. Activists utilize these platforms to organize protests, distribute news, and support human rights efforts while maintaining anonymity. Likewise, journalists use darknet services to communicate confidentially with sources who may face persecution if their identities were revealed.
Moreover, the darknet serves as a resource for those seeking privacy and freedom from surveillance. Many legitimate online marketplaces and forums operate on darknet sites, offering legal products or services that require discretion. Academic researchers and cybersecurity professionals also explore darknet environments to study cyber threats, gather intelligence, and better understand criminal networks, all in the interest of enhancing online security and developing protective measures.
In summary, while darknets are often linked to illegal activities, they also play a vital role in facilitating legitimate activities that prioritize privacy, security, and free expression. Understanding the diverse uses of darknet sites helps foster a balanced perspective on their significance in the digital landscape.
Illicit Activities
Darknet sites are part of an hidden segment of the internet that can only be accessed through specialized software, such as Tor or I2P. These sites are often associated with anonymous communication and privacy protection, but they are also known for hosting a variety of illicit activities. The anonymous nature of the darknet enables users to engage in activities that would be difficult to conduct on the regular web.
One prevalent activity on darknet sites involves the sale of illegal goods and services, including drugs, weapons, and counterfeit documents. Such transactions are facilitated by cryptocurrencies, which provide a degree of anonymity for both buyers and sellers. These illicit markets operate in a decentralized manner, often changing locations to evade law enforcement detection.
Besides commercial crimes, darknet sites are frequently used for illegal information sharing, including hacking tools, stolen data, and malware. Cybercriminals leverage these platforms to distribute malicious software or exchange hacking techniques, often staying behind the veil of anonymity to avoid prosecution. Such activities contribute significantly to the rise of cyber threats globally.
Other illicit activities that occur on darknet sites include human trafficking, child exploitation, and the promotion of illegal substances. These sites create a secure environment for criminals to coordinate and conduct their operations with reduced risk of exposure. Law enforcement agencies worldwide continuously work to monitor and shut down these dark web marketplaces and forums.
While the darknet provides a space for legitimate activities like privacy-focused journalism and political activism, its association with illegal operations remains a major concern. Understanding these activities is essential for developing effective strategies to combat crime on these hidden parts of the internet while respecting privacy rights.
Whistleblowing and Censorship Evasion
Darknet sites are often associated with a variety of activities that operate outside the boundaries of traditional internet regulations. These sites are accessible through specialized software and networks that provide anonymity, making them a preferred platform for sensitive and often illicit exchanges. Among the most common uses are whistleblowing, where individuals share confidential information to expose wrongdoing or corruption, and censorship evasion, allowing users to access information freely in restrictive environments. Such activities highlight both the potential for safeguarding free speech and the risks associated with illegal operations that can occur within these anonymous networks.
Whistleblowing on darknet sites plays a significant role in promoting transparency and accountability by enabling individuals to disclose information without fear of retribution. This secure environment is crucial for insiders seeking to reveal unethical practices in corporations or governments, especially when traditional channels are compromised or controlled. The anonymity provided by darknet sites ensures that whistleblowers can share sensitive data while protecting their identities from retaliation.
Censorship evasion is another critical activity associated with darknet sites. In countries with strict information control, users often turn to these platforms to access news, reports, or social discussions that are otherwise blocked or censored. By leveraging encrypted networks, individuals can maintain a free flow of information, ensuring their right to access diverse perspectives and participate in open dialogue. While these sites can facilitate positive activism, they are also exploited for illegal activities, emphasizing the need for balanced oversight and legal frameworks.
Overall, darknet sites serve as a complex space for both safeguarding fundamental freedoms and enabling illicit conduct. Recognizing these dual roles is essential for developing policies that protect privacy and expression while addressing misuse. As technology continues to evolve, understanding the activities on darknet sites and their implications remains a priority for policymakers, law enforcement, and civil society alike.
Navigational and Technical Aspects
Navigational and technical aspects play a crucial role in exploring and understanding darknet sites, which operate on a hidden part of the internet often used for various purposes. Efficient navigation ensures users can find the information or services they seek amidst the complex and often clandestine network of these sites. Technical considerations include security measures, anonymization techniques, and the underlying infrastructure that keeps these sites accessible only through specific tools, such as the Tor browser. Properly understanding these elements is essential for anyone interested in the darknet, whether for research, security analysis, or other legitimate inquiries. Some darknet sites, like those hosting marketplaces or forums, require careful navigation and technical knowledge to ensure safety and privacy while browsing.

Searching and Finding Darknet Sites
Navigating and understanding the technical aspects of searching for darknet sites can be complex due to the unique nature of the dark web. These sites often operate using specialized protocols and networks that differ significantly from the surface web, making access and discovery more challenging for everyday users. To effectively find darknet sites, users typically rely on specific search engines and directories designed for this purpose, utilizing particular keywords and trusted sources to enhance accuracy.
From a technical perspective, exploring darknet sites requires understanding the underlying infrastructure, such as the Tor network, which anonymizes user activity and protects site operators’ privacy. The dark web’s layered security measures often include encryption, anonymous hosting, and decentralized access points, all of which contribute to the difficulty and complexity of locating specific sites. Search engines tailored for the dark web often index a limited range of sites and use specialized crawling techniques to gather data while maintaining user anonymity.
Searching effectively involves employing specific strategies, such as utilizing well-known directories, forums, and community recommendations, as well as employing relevant keywords that match the content or purpose of the darknet sites you’re interested in. Given the clandestine nature of these sites, users should exercise caution to avoid malicious content or illegal activities. Awareness of the technical aspects and leveraging trusted sources can improve search results, helping users find what they need securely and efficiently in this hidden part of the internet landscape.
Security Precautions and Malware Risks
Darknet sites represent a hidden segment of the internet that operates outside the reach of standard search engines and regular browsing protocols. Navigating these sites involves unique technical and security considerations that differ significantly from conventional web browsing. Ensuring safe access requires a thorough understanding of the navigational and technical aspects, as well as awareness of potential security risks and malware threats.
From a navigational standpoint, accessing darknet sites typically involves specialized software such as the Tor browser, which provides anonymity by routing connections through multiple encrypted nodes. This process complicates the user’s ability to verify site authenticity and navigation pathways, making it essential to rely on trusted directories or community-guided links. Given the anonymous nature of these sites, users must be cautious of phishing and counterfeit sites that mimic legitimate platforms.
Technically, darknet sites use specific domain suffixes such as .onion, which are not accessible via standard browsers. Proper configuration of privacy settings and software updates is crucial to prevent exploits. Privacy-enhancing tools like VPNs may add an extra layer of security, but they do not eliminate all risks. Additional precautions include avoiding the download of files from unknown sources and steering clear of clicking suspicious links that could introduce malware or compromise anonymity.
Security precautions are paramount when dealing with darknet sites. Users should ensure their systems are protected with comprehensive security tools, including antivirus and anti-malware programs, and remain vigilant about potential threats. Employing strong, unique passwords and avoiding sharing personal information further mitigates risks. Regularly updating software and security patches helps close vulnerabilities that cybercriminals, who often target darknet sites, exploit to spread malware or conduct cyber-attacks.
Malware risks on darknet sites are significant, as malicious actors often deploy viruses, ransomware, or spyware designed to steal data or take control of devices. These sites can harbor malicious scripts embedded in seemingly innocuous pages, which can compromise security upon visit. Recognizing the signs of malware infection and maintaining secure browsing practices, such as using sandbox environments for testing unknown links, can help prevent compromise.
- Use trusted software like the Tor browser for access rather than unreliable third-party tools.
- Keep all security and privacy software up to date to guard against emerging threats.
- Be cautious of links and downloads, especially from unknown or unverified sources.
- Employ VPNs and other privacy-enhancing technologies to obscure your identity and location.
- Regularly scan for malware and vulnerabilities to maintain system integrity.
In conclusion, engaging with darknet sites requires careful consideration of navigational and technical challenges, along with diligent security precautions to mitigate malware risks. Adhering to best practices ensures safer browsing and helps protect personal information in this inherently risky digital environment.
Operational Challenges and Anonymity
Darknet sites operate within a complex ecosystem that presents numerous navigational and technical challenges, as well as operational hurdles and concerns about user anonymity. These sites, often accessed through specialized networks such as Tor, require users to navigate unique infrastructure that differs significantly from the surface web. The layered nature of the darknet demands a deep understanding of network configurations and security protocols to ensure safe and anonymous access.
One of the primary navigational challenges on darknet sites is the anonymous and decentralized structure, which often lacks a standardized indexing system. Users must rely on directories, forums, or word-of-mouth to discover new sites, making exploration more difficult than on regular websites. Additionally, these sites frequently employ complex encryption and routing techniques to obfuscate their locations and activities, adding to the navigational complexity.
From a technical perspective, darknet sites utilize sophisticated security measures to protect both the operators and users. These include layered encryption, hidden service protocols, and constantly changing domain identifiers to evade detection and shutdown efforts. Maintaining operational stability requires continuous updates and a robust infrastructure resistant to cyberattacks or takedown operations, which are common in the darknet environment.
Operational challenges on darknet sites encompass legal risks, resource management, and combating malicious activities. Because many of these sites host clandestine activities, operators must implement stringent security practices to avoid detection and infiltration. They often face resource limitations, including bandwidth constraints and server reliability issues, which can impact site accessibility and performance. Additionally, the presence of malicious actors necessitates rigorous moderation and security protocols to prevent scams, malware distribution, and other cyber threats.
Complexity around maintaining anonymity is a critical concern for both operators and users. While techniques such as using encryption tools and anonymous communication channels promote privacy, they also introduce vulnerabilities if not properly managed. Users and operators must continuously adapt to evolving surveillance techniques and law enforcement tactics, making anonymity a perpetual priority but also a persistent challenge in the darknet ecosystem.
- Darknet sites often depend on specialized routing and encryption methods to ensure user and operator anonymity.
- The decentralized and hidden nature of these sites complicates navigation and discovery processes.
- Technical infrastructure must be regularly updated to defend against cyberattacks and shutdown attempts.
- Operational security measures are critical to prevent detection and legal repercussions while managing resource constraints.
- Maintaining true anonymity requires continuous adaptation to new surveillance and infiltration techniques by law enforcement or malicious actors.
Law Enforcement and Intelligence Gathering
Law enforcement agencies and intelligence organizations play a crucial role in monitoring and investigating activities on darknet sites, which often serve as platforms for illicit transactions, information exchange, and other clandestine operations. These sites provide a level of anonymity that complicates efforts to track criminal activities and gather vital intelligence. By employing specialized tools and techniques, authorities can identify patterns, track individuals, and uncover networks operating behind the veil of encryption. Darknet sites are frequently targeted for surveillance because they can harbor a wide range of illegal activities, from drug trafficking to cybercrime. Effective intelligence gathering from these hidden corners of the internet is essential for maintaining security and combating criminal enterprises.
Monitoring Darknet Forums and Chatrooms
Darknet sites serve as discreet digital environments often used for a variety of activities, both legitimate and illicit. Law enforcement agencies and intelligence organizations actively monitor these sites to gather vital information, prevent criminal activities, and ensure national security. Due to the anonymous nature of the darknet, specialized techniques and tools are employed to identify, analyze, and track entities operating within these hidden networks. This process requires meticulous attention to digital footprints, patterns of communication, and online behavior.
Monitoring darknet forums and chatrooms is a complex task that involves a combination of technical expertise and strategic intelligence methods. Agencies typically utilize covert operations, such as setting up undercover accounts or deploying automated bots, to infiltrate these communities. These efforts help gather intelligence on ongoing illegal transactions, emerging threats, and criminal networks. The goal is to disrupt illicit activities such as drug trafficking, weapons trade, cybercrime, and human trafficking.
- Open-source intelligence (OSINT): Analysts collect publicly available data from darknet sites to identify patterns, key players, and evolving trends.
- Undercover operations: Law enforcement agencies create fake profiles to gain trust within forums and chatrooms, facilitating information exchange.
- Automated scraping tools: These tools scan forums and chatrooms for keywords, suspicious activity, and network links associated with criminal operations.
- Network analysis: Connecting digital footprints to physical locations or known suspects helps build comprehensive profiles for criminal investigations.
- Collaboration with international agencies: Sharing intelligence across borders enhances the effectiveness of monitoring activities and disrupts transnational criminal enterprises.
Through persistent effort and advanced technology, agencies aim to uncover illegal activities hidden beneath the anonymity of darknet sites such as darknet marketplaces and forums. These efforts are crucial in safeguarding public safety, maintaining legal order, and staying ahead of covert online threats.
Tracking and Identifying Participants
Law enforcement agencies play a crucial role in maintaining security and order by utilizing advanced techniques for intelligence gathering, tracking, and identifying participants on various platforms, including darknet sites. These hidden corners of the internet are often associated with illicit activities, making it essential for authorities to develop sophisticated methods to monitor and investigate related activities without compromising privacy and legal standards.
Intelligence gathering on darknet sites involves a combination of technical expertise and strategic analysis. Law enforcement agencies employ tools like network analysis, traffic monitoring, and undercover operations to identify key individuals and groups engaged in illegal activities. By analyzing patterns of communication and transaction flows, authorities can uncover networks operating behind anonymity layers designed to conceal identities.
Tracking and identifying participants on darknet sites requires a multi-faceted approach that includes digital forensics, surveillance, and cooperation with cybersecurity experts. Techniques such as device fingerprinting, IP tracing, and the analysis of transaction data help link online personas to real-world identities. Despite the privacy features inherent to darknet platforms, persistent investigation efforts can sometimes pierce through these layers of anonymity.
The ongoing challenge for law enforcement is balancing effective surveillance with respect for privacy rights, while continuously adapting to the evolving landscape of darknet sites. As criminal networks become more sophisticated, so too must the techniques used to track and identify participants to prevent illegal activities and uphold digital security.
Detection of Illegal Activities and Data Breaches
Darknet sites are a significant component of online activity that often operates outside the boundaries of traditional internet monitoring. Law enforcement agencies and intelligence organizations play a crucial role in detecting illegal activities and safeguarding digital spaces by employing advanced strategies for intelligence gathering. These efforts focus on uncovering illicit operations, such as drug trafficking, weapon trade, and cybercriminal activities, that frequently utilize darknet sites to facilitate anonymous transactions.
Effective detection of illegal activities on darknet sites requires a combination of technical expertise, sophisticated surveillance tools, and international cooperation. Agencies employ methods such as cyber infiltration, traffic analysis, and monitoring of cryptocurrency transactions to track offenders while respecting privacy laws and civil liberties. The goal is to identify patterns and connections that reveal illicit networks operating behind the anonymity of the darknet.
Data breaches often intersect with illegal activities on darknet sites, making detection a priority for law enforcement. Cybersecurity teams analyze compromised data, monitor dark web forums, and use advanced algorithms to identify breaches related to criminal enterprises. Early detection allows for swift action to dismantle criminal infrastructures and prevent further harm.
In the context of darknet sites, intelligence agencies also focus on identifying key players and understanding the operational methods used by illicit actors. This information is critical for disrupting ongoing criminal networks and preventing future crimes. The continuous evolution of technology necessitates adaptive strategies that incorporate artificial intelligence, machine learning, and open-source intelligence to stay ahead of malicious actors.
Overall, efforts to monitor darknet sites and detect illegal activities underscore the importance of collaboration among law enforcement, cybersecurity experts, and international partners to protect digital and physical communities from harm caused by unlawful acts concealed within the depths of the internet.
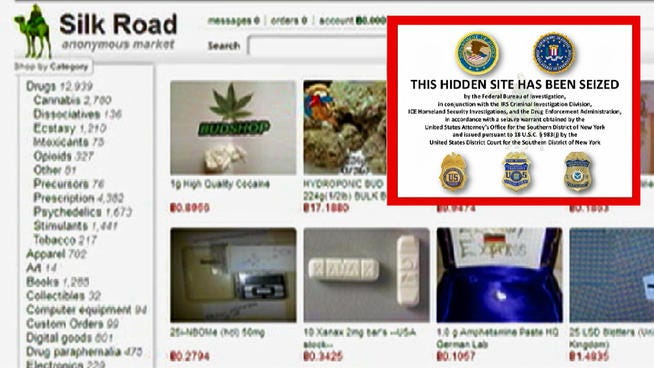
Risks and Legal Concerns
Engaging with darknet sites poses significant risks and legal concerns that should not be overlooked. These hidden parts of the internet are often associated with illicit activities and pose substantial dangers to unwary users. As the darknet offers anonymity, it attracts both individuals seeking privacy and those involved in illegal endeavors, making it essential to understand the potential legal implications before exploring these sites. Navigating this shadowy realm can lead to unintended exposure to unlawful content or activities, potentially resulting in severe legal consequences. For those interested in exploring darknet sites responsibly, it is crucial to stay informed about the legal landscape and exercise caution at all times, especially when accessing sites that may host questionable or prohibited material, such as darknet marketplaces. Ensuring compliance with laws and understanding the inherent risks is vital to avoid legal trouble and safeguard personal security.
Malware and Cybersecurity Threats
Darknet sites operate within a hidden segment of the internet, offering a degree of anonymity that can attract illicit activities alongside legitimate uses. However, navigating these sites involves significant risks and legal concerns that users must carefully consider. Many darknet sites are associated with illegal transactions, such as drug sales, weapons trading, or illicit data exchanges, making them targets for law enforcement efforts worldwide. Engaging with such sites can inadvertently lead to legal consequences, including criminal charges, even if the intent was benign. Additionally, the prevalence of malware and cybersecurity threats on darknet sites poses serious dangers. Malicious actors often use these platforms to distribute malware, phishing schemes, or ransomware attacks, which can compromise personal information, financial data, or entire systems. Users must remain vigilant and employ robust cybersecurity measures if they choose to access darknet sites, recognizing that the hidden nature of these platforms complicates efforts to ensure safety and legality. Ultimately, understanding the risks and legal concerns associated with darknet sites is essential to making informed decisions and avoiding potentially severe consequences.
Legal Implications of Access
Accessing darknet sites can pose significant legal risks and raise various legal concerns. The dark web often hosts content that operates outside the bounds of traditional regulations, making it a complex environment for users and operators alike. Understanding the legal implications of engaging with these sites is essential to avoid unintended violations of the law.
One primary legal concern is the potential for involvement in illegal activities, such as the sale of illicit goods or services, which are commonly associated with darknet sites. Users may unknowingly expose themselves to legal liabilities if they participate in or facilitate such transactions. Additionally, law enforcement agencies worldwide actively monitor and investigate illegal activities on the dark web, increasing the risk of legal action against individuals who access or conduct illegal operations.
Legal implications may also include issues related to privacy and data security. Accessing darknet sites can sometimes involve circumventing restrictions or using anonymizing tools, which might be scrutinized under laws governing unauthorized access or cybercrime statutes. Furthermore, hosting or operating darknet sites carries risks of being prosecuted for facilitating criminal behavior or conspiracy charges.
- Engaging in Illegal Transactions: Visitors who purchase or sell prohibited items on darknet sites may face criminal charges.
- Possession of Illegal Content: Downloading or possessing unlawful content can result in severe legal consequences.
- Facilitating Crimes: Operators or users involved in coordinating illegal activities could be held liable under the law.
- Using Anonymization Tools: While tools like Tor protect privacy, their misuse for criminal purposes can attract legal scrutiny.
Lastly, legal jurisdictions vary significantly regarding activities conducted on darknet sites, making it crucial for users to understand local laws and regulations. Ultimately, the risks associated with accessing darknet sites highlight the importance of cautious and informed behavior to navigate the legal landscape responsibly.
Potential for Exposure to Harmful Content
Engaging with darknet sites involves significant risks and legal considerations that users must carefully evaluate. The darknet, often associated with anonymous activities, hosts a variety of content that can be both legally permissible and unlawful, depending on the nature of the material accessed. Because of the hidden and unregulated environment, users are exposed to potential harm from illegal activities, scams, and malicious actors. Legal concerns arise when accessing or participating in activities that violate laws related to drug trafficking, illegal trading, or illicit services.
One of the primary risks associated with darknet sites is the potential exposure to harmful content that can have serious psychological or legal repercussions. Law enforcement agencies actively monitor and investigate illegal activities on these platforms, and involvement can lead to criminal charges. Additionally, the anonymous nature of the darknet makes it easier for malicious entities to exploit users through scams, hacking, and malware infections.
- Illegal Content: Many darknet sites host illegal materials, such as stolen data, counterfeit documents, or illicit drugs, which can result in legal consequences for users.
- Malware and Phishing: Accessing unsecured or malicious darknet sites can expose users to ransomware, viruses, or phishing attempts aimed at stealing personal or financial information.
- Law Enforcement Risks: Authorities continuously monitor illicit activities within the darknet, risking prosecution for individuals engaged in illegal behavior.
- Financial Loss and Scams: Users may fall victim to schemes promising illegal goods or services but ultimately result in financial theft or loss.
- Exposure to Harmful Content: Darknet sites may contain disturbing or violent material that can have psychological impacts on viewers.
It is crucial for anyone considering exploring darknet sites to be aware of these risks and to prioritize legal and safe online practices. Awareness and caution can help mitigate potential harms while understanding the serious legal ramifications associated with illicit activities on these platforms.
Use Cases for Organizations and Governments
Organizations and governments exploring innovative strategies for security, privacy, and intelligence gathering often consider the unique capabilities offered by darknet sites. These hidden online spaces provide a platform for confidential communication, clandestine operations, and the exchange of sensitive information. Leveraging darknet sites can enhance efforts in combating cyber threats, uncovering illicit activities, and protecting national security interests. Understanding the potential uses of darknet sites is essential for agencies seeking to adapt to the evolving digital landscape and employ discreet, encrypted channels to achieve their objectives.
Threat Intelligence and Vulnerability Management
Darknet sites serve as vital platforms for organizations and governments to explore a range of security-related use cases, particularly in the realms of threat intelligence and vulnerability management. These hidden areas of the internet offer unique insights into malicious activities, cyber threats, and emerging vulnerabilities that are not apparent on the surface web. By monitoring darknet sites, entities can gather valuable information about cybercriminal operations, trading of cyberattack tools, and discussions surrounding potential security breaches, enabling proactive defense strategies.
In threat intelligence, darknet sites function as a critical source for identifying new attack techniques, zero-day vulnerabilities, and malicious actor behaviors. Organizations and governments can leverage the intelligence gathered from these sites to enhance their situational awareness, anticipate potential threats, and develop timely countermeasures. These platforms often host forums and marketplaces where cybercriminals exchange stolen data, malware, or hacking services, providing early warning signs of upcoming attacks or data breaches.
Regarding vulnerability management, darknet sites are instrumental in revealing exploit kits, hacking tools, and vulnerabilities that criminals are actively exploiting. Continuous surveillance allows security teams to detect emerging threats and develop patches or mitigation strategies before widespread attacks occur. Additionally, insights gained from darknet monitoring support the strengthening of security posture by understanding attacker methodologies and adapting cybersecurity practices accordingly.
Overall, darknet sites are integral to comprehensive cybersecurity efforts, offering a window into illicit activities that threaten organizational and national security. Properly harnessed, they enable proactive threat intelligence and vulnerability management, reducing the risk of cyber incidents and fostering a more resilient digital environment.
Protection Against Data Leaks

Organizations and governments face growing challenges in safeguarding sensitive information and ensuring secure communication channels, especially when dealing with illicit activities on the darknet. Understanding the use cases for protecting against data leaks in such environments is crucial for maintaining national security, corporate integrity, and personal privacy.
Darknet sites often serve as platforms for illegal trade, cybersecurity threats, and other malicious activities. To combat these risks, organizations need robust measures to prevent unauthorized data disclosures and to monitor potential leaks that could compromise confidential data. These measures help in safeguarding intellectual property, safeguarding user data, and maintaining compliance with regulatory standards.
- Implementing Advanced Data Encryption: Encrypting sensitive information both in transit and at rest ensures that even if data is accessed through darknet activities, it remains unreadable and unusable by unauthorized parties.
- Monitoring Network Traffic: Continuous monitoring helps detect unusual activity or data exfiltration attempts that originate from or are connected to darknet sites, allowing for rapid response.
- Employing Threat Intelligence Platforms: Integrating real-time threat intelligence assists organizations in identifying emerging threats linked to darknet sites, enabling proactive defense strategies.
- Restricting Access to Sensitive Data: Limiting access based on roles and implementing strict authentication protocols minimize the risk of internal leaks that can be exploited via darknet channels.
- Educating Employees and Stakeholders: Raising awareness about darknet-related scams and methods used for data breaches helps prevent accidental disclosures and social engineering attacks.
Protection against data leaks is especially pertinent given that darknet sites can be used to facilitate data breaches or sell stolen information. Such incidents can lead to severe consequences, including financial loss, reputational damage, and legal penalties. Therefore, organizations and governments must adopt comprehensive security measures to detect, prevent, and respond to data leaks originating from or associated with these clandestine online environments.
Supporting Whistleblowers and Activists
Darknet sites serve as vital platforms for organizations and governments seeking to support whistleblowers and activists operating in sensitive environments. These sites provide a secure environment where individuals can share confidential information, reveal misconduct, or coordinate activism without exposing their identities or locations. By leveraging the anonymity features of darknet sites, entities can protect the privacy of those who challenge oppressive regimes, corporations, or unethical practices. Such platforms enable the dissemination of critical information while minimizing risks for the reporters or advocates involved.
Supporting whistleblowers through darknet sites enhances transparency and accountability across various sectors. Governments and organizations can establish trusted channels for submitting evidence related to corruption, human rights violations, or environmental abuse. These channels help ensure that information reaches the appropriate authorities or oversight bodies securely and discreetly. Furthermore, darknet sites facilitate international collaboration among activists and organizations by providing a resilient communication network resistant to censorship or surveillance efforts.
In addition to aiding whistleblowers, darknet sites are instrumental in broadening activism efforts, particularly in regions with limited press freedom or where dissent is heavily monitored. They enable real-time sharing of information, mobilization of support, and organization of campaigns without exposing participants to undue risk. Support systems integrated with darknet technology can also include tools for encrypted communication, anonymous tip submissions, and secure file sharing, which are crucial for safeguarding sensitive exchanges.
Overall, darknet sites play a critical role in empowering organizations and governments committed to transparency, human rights, and social justice. By providing a discreet venue for whistleblowers and activists, these platforms help protect individual safety while fostering a more open flow of important information across borders and barriers. As such, they remain an essential component of the digital ecosystem supporting social change efforts worldwide.