Understanding Onion Dark Websites
Understanding onion dark websites requires delving into the hidden corners of the internet known for their anonymity and privacy features. These sites, accessible only through specialized browsers, form a complex web of digital spaces where users can communicate, trade, and share information securely and privately. The concept of onion dark websites is often associated with illicit activities, but they also serve as vital platforms for journalists, activists, and whistleblowers operating under oppressive regimes. Exploring this world offers a glimpse into the importance of privacy in digital communication and the challenges of regulating online spaces that are intentionally concealed.
Onion dark websites operate within the dark web, a part of the internet not indexed by standard search engines. They use the Tor network, which anonymizes user identities and locations, enabling secure access to these sites. While many associate these websites solely with illegal transactions, there are legitimate uses that promote free speech and human rights. For those interested in exploring further, a reputable onion dark website(http://nexusafejew45osqaawl2xqjwmincsfvjwuwtm2fums2kjeon7tbmlid.onion) offers insights into secure browsing and digital privacy.
Definition and Access Requirements
Onion dark websites are a subset of hidden online platforms accessible through specialized networks that prioritize privacy and anonymity. These websites operate on the Tor network, which uses onion routing to mask users’ locations and prevent tracing by third parties. The unique structure of onion dark websites ensures that both visitors and site operators can maintain a high level of confidentiality, making them popular for various legitimate and illicit activities alike.
Accessing onion dark websites requires specific configurations such as installing the Tor browser, which enables users to connect securely to the Tor network. Unlike traditional websites, these sites use “.onion” domain extensions that are not accessible through standard web browsers. To visit an onion dark website, users must enter the site’s unique onion address into their Tor browser, ensuring that their connection remains encrypted and anonymized throughout the process.
The appeal of onion dark websites lies in their ability to provide a platform for anonymous communication, free from censorship and surveillance. However, this same feature also attracts illicit activities, including black markets, illegal content, and cybercriminal operations. Therefore, understanding the access requirements and the underlying technology behind onion dark websites is essential for navigating this complex and often hidden segment of the internet safely and responsibly.
Use of .onion Domains and Onion Routing Technology
Onion dark websites are part of a hidden segment of the internet that operates beyond traditional search engines and standard web accessibility. These sites are hosted on a special network known as the Tor network, which ensures user privacy and anonymity. Accessing these pages typically requires specific software and configurations, making them less accessible to the general public but valuable for privacy-conscious individuals and those seeking secure communication channels.
The core technology behind these sites involves the use of .onion domains, which are unique to the Tor network. Unlike conventional domain names, .onion addresses are not registered through standard DNS systems but are generated cryptographically, providing a high level of security and anonymity. When navigating to a .onion site, the request is routed through multiple network nodes, effectively cloaking the origin and destination of the user and hosting server, which enhances privacy and protection against censorship or surveillance.
Onion routing technology is fundamental to the existence of onion dark websites. This method involves encrypting data multiple times and sending it through a series of network relays called onion routers. Each relay decrypts a layer of encryption to reveal where the data should go next, ultimately reaching its intended destination. This layered encryption and multi-hop routing create a secure pathway, making it extremely difficult for external parties to trace the activity back to the user or the hosting server.
By leveraging these technologies, onion dark websites serve various purposes, ranging from secure communication and anonymous publishing to more illicit activities. Despite their reputation, they play a crucial role in safeguarding privacy and facilitating free expression under oppressive regimes or in situations where anonymity is essential. Understanding the use of .onion domains and onion routing technology underscores the significance of these hidden web spaces in the broader context of internet privacy and security.
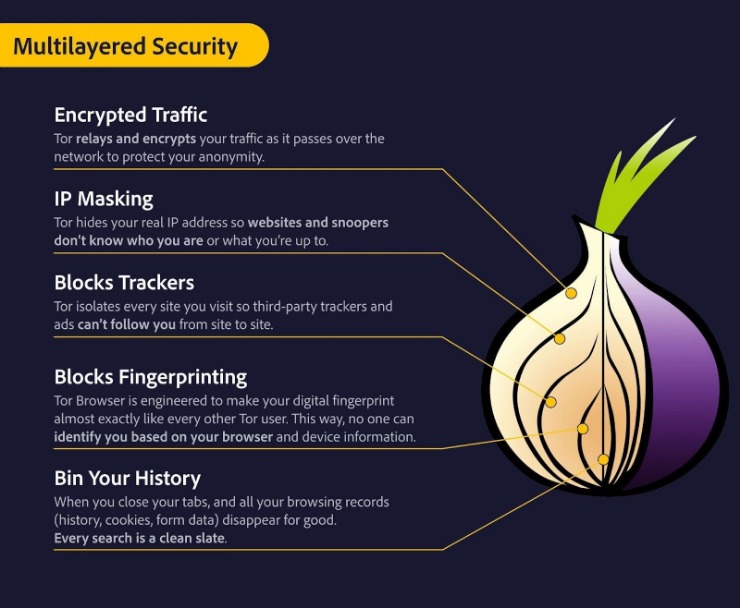
Purpose and Common Uses of Onion Sites
Onion dark websites are specialized online spaces that operate on the Tor network, providing users with enhanced privacy and anonymity. These websites are accessible through the Tor browser, which masks user identities and encrypts internet traffic to protect against surveillance and tracking. The unique “.onion” domain extension signifies sites hosted on the Tor network, making them difficult to locate or monitor from standard internet infrastructure. Onion dark websites serve various purposes, ranging from secure communication to underground marketplaces, due to their ability to offer a degree of confidentiality not available on the surface web. Many users turn to these sites for safe activism, whistleblowing, or avoiding censorship, while others may engage in illicit activities. The purpose of onion sites extends beyond illegality; they are vital for privacy-conscious individuals and organizations requiring secure channels for sensitive information. Overall, understanding onion dark websites requires recognition of their dual role in fostering both legitimate privacy needs and facilitating less lawful behaviors.
Features of Onion Dark Websites
Onion dark websites are often associated with hidden online networks that operate beyond the reach of traditional internet monitoring. These sites are characterized by their use of the Tor network, which provides users with anonymity and privacy. Features of onion dark websites include encrypted connections, decentralized hosting, and access through specialized browsers. Many of these sites prioritize privacy above all else, making them attractive for various purposes ranging from secure communications to illicit activities. For those interested in exploring these sites securely, it is essential to understand the unique features that set them apart from regular websites, such as their persistent use of encrypted onion addresses and the requirement for specialized access methods. One example of such a site can be found through this onion dark website, which showcases how these hidden networks function in practice.
Anonymous Hostings and Encrypted Connections
Onion dark websites are a unique segment of the internet that operate on the Tor network, offering enhanced privacy and anonymity for both users and hosted content. These websites utilize specialized features such as encrypted connections and anonymous hosting services to ensure that both the location of the server and the identity of users remain concealed. This infrastructure makes onion dark websites popular among individuals seeking privacy for legitimate reasons, as well as those involved in activities that require a high degree of discretion.
One defining characteristic of onion dark websites is their use of layered encryption, which provides secure communication channels between users and the website. This encrypted connection not only protects data from eavesdropping and tampering but also helps in maintaining the anonymity of visitors. Additionally, the Tor network supports anonymous hosting, where sites are hosted on servers that do not reveal their physical location or ownership details, further enhancing privacy and security.
The features of onion dark websites extend to their resilient architecture, which often employs decentralized hosting and complex routing techniques. This makes it difficult for surveillance or censorship efforts to take down or monitor these sites effectively. Combined with encrypted connections, these features create a robust environment for sensitive communications, free from the prying eyes of external parties.
Overall, onion dark websites exemplify the principles of privacy and security through their specialized infrastructure, characterized by anonymous hosts and encrypted connections. These features are crucial in enabling safe and private access to information while protecting the identities of both content providers and users in the digital ecosystem.
Levels of Encryption and User Anonymity
Onion dark websites are a significant part of the hidden web, operating over the Tor network to provide increased privacy and security for users and content providers. These sites are characterized by their unique features that prioritize anonymity and confidentiality, making them appealing for various privacy-sensitive activities. One notable feature of onion dark websites is their use of multiple levels of encryption to safeguard communications and data exchanges, ensuring that both users and operators remain protected from surveillance and tracking.
The levels of encryption in onion dark websites typically involve three key layers. The first layer encrypts data between the user and the entry node of the Tor network. The second layer secures communications between the entry node and the exit node, while the third layer encrypts data from the exit node to the destination server. This multi-layered encryption process, often referred to as “onion routing,” helps to obscure the origin, destination, and content of the data, significantly enhancing user privacy.
User anonymity is a fundamental feature of onion dark websites. Tor’s architecture routes user traffic through a series of volunteer-operated relays, making it exceedingly difficult to trace a user’s identity or location. This decentralized network ensures that no single point holds enough information to compromise privacy. Furthermore, the use of .onion domains and layered encryption reinforces this anonymity, allowing users to access content without exposing their IP addresses or personal identifiers. Consequently, onion dark websites provide a secure environment for whistleblowers, journalists, and individuals seeking privacy from intrusive surveillance or censorship.
Design and Content Presentation
Onion dark websites are specialized online platforms that operate within the Tor network, offering users a high level of privacy and anonymity. These websites are distinguished by their unique features, which include encrypted communication channels and hidden service addresses, making them difficult to discover and access through conventional means. The design of onion dark websites often emphasizes simplicity and security, prioritizing functionality over aesthetic appeal to prevent unintended disclosure of identifying information.
Typically, onion dark websites feature minimalistic layouts, focusing on clear navigation and straightforward content presentation. They often utilize plain text or simple graphics to reduce loading times and avoid unnecessary scripts or tracking mechanisms that could compromise user anonymity. Content is carefully organized to serve specific purposes, such as information sharing, marketplace transactions, or forums, with strict moderation to maintain privacy and security standards.
When it comes to content presentation, onion dark websites tend to be more direct and utilitarian. They often employ plain HTML and basic styling to minimize vulnerabilities and reduce suspicion. This approach also helps in resisting censorship and detection by authorities. The overall design philosophy revolves around maintaining confidentiality and ensuring users can access the information or services they seek without exposing their identity or location.
In essence, onion dark websites are characterized by their focus on security, anonymity, and straightforward design, making them a unique segment of the internet where privacy is paramount. Their features, layout, and content strategies all reflect a commitment to safeguarding user privacy while providing essential or sensitive information securely.
Common Types of Content on Onion Dark Websites
Onion dark websites are a hidden part of the internet that host a wide variety of content not accessible through standard search engines. These sites operate on the Tor network, providing anonymity and privacy for both visitors and content creators. Understanding the common types of content found on onion dark websites can offer insight into their purpose and functionalities. From black markets and illicit trade to forums and information sharing platforms, the range of content is diverse. Onion dark websites often serve as underground hubs where users seek anonymity for sensitive activities. One example of such content includes marketplaces featuring illegal goods, as well as cryptic forums discussing confidential topics. For more detailed information about the kinds of content on these sites, exploring onion directories can be informative, such as this onion directory. Understanding these common content types is essential for appreciating the complexities and risks associated with browsing the onion dark web.
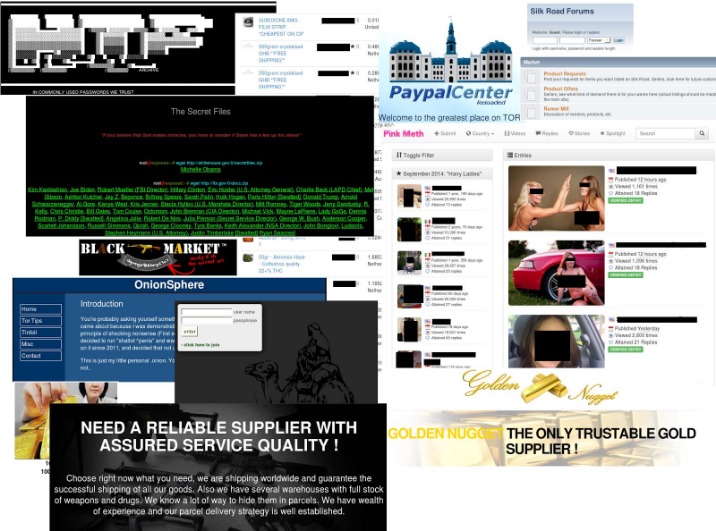
Illicit Marketplaces and Black Markets
Onion dark websites are hidden parts of the internet that operate on the Tor network, offering a range of illicit and underground content. These sites are often accessed through specific browsers designed for anonymity, making them a hub for various types of illegal activities. Understanding the common types of content found on these sites can provide insight into their operations and the challenges they pose to law enforcement.
One prevalent type of content on onion dark websites involves illicit marketplaces that facilitate the buying and selling of illegal goods. These marketplaces often feature listings for narcotics, firearms, stolen data, and counterfeit items. Such marketplaces operate similarly to legitimate e-commerce platforms but are hidden from standard search engines, making them accessible only through specialized tools.
Another common category includes black markets dealing with sensitive and prohibited services. These can range from hacking services and illegal document forging to illicit financial transactions. The anonymous nature of onion dark websites allows vendors to offer services that would be heavily restricted or illegal in the open web.
Additionally, these sites host various forms of illegal content such as counterfeit currencies, child exploitation material, and pirated digital media. The clandestine environment makes it difficult to regulate or remove such content, leading to significant challenges for authorities worldwide.
Furthermore, onion dark websites are used for communication among criminal organizations, providing secure channels for coordination, planning, and sharing of illegal information. These communications often involve encrypted messaging and forums dedicated to specific illicit activities.
Overall, the onion dark website ecosystem encompasses a wide range of criminal content, from illegal markets and services to harmful media. Its concealed nature underscores the importance of ongoing efforts to combat cybercrime and protect lawful internet users from exposure to such illicit materials.
Illegal Content and Child Exploitation
Onion dark websites are a part of the deep web that utilize the Tor network to provide users with enhanced privacy and anonymity. These sites often host a variety of content that is not accessible through conventional means, some of which is legal and legitimate, but many contain illegal material. The range of content found on these platforms can be quite diverse, reflecting both the technological capabilities of the network and the motivations of their users.
Common types of content on onion dark websites include marketplaces, forums, and repositories for various goods and services. Some sites facilitate the exchange of legal products or information in privacy-sensitive areas. However, a significant portion of the content is illegal, such as illicit drug markets, weapons trading, and counterfeit currency services. These sites thrive on the anonymity provided by the Tor network, making law enforcement efforts more challenging.
One of the most concerning categories of content found on onion dark websites involves child exploitation materials. Such content is strictly illegal and profoundly harmful. Despite ongoing efforts by authorities to shut down and monitor these sites, it remains accessible on some parts of the dark web. The presence of child exploitation material is a critical issue, as it perpetuates severe abuse and exploitation, and combating this kind of content is a top priority for law enforcement agencies worldwide.
- If privacy is your goal, it’s best to avoid logging into any identifiable accounts while using Tor.
- The moment you log into your email, social media, or other personal accounts, you’re no longer anonymous.
- Our crawling found 55,828 different onion domains, but only 8,416 were observed to be live on the Tor network during our crawl.
- To advance human rights and freedoms by creating and deploying free and open source anonymity and privacy technologies, supporting their unrestricted availability and use, and furthering their scientific and popular understanding.
- While many dark websites appear sketchy, The New York Times is an exception.
It is important for internet users to be aware of the darker aspects of onion dark websites and to understand the dangers involved in accessing or engaging with illicit content. The existence of illegal material such as child exploitation content highlights the need for continued vigilance and robust legal measures to protect vulnerable populations and uphold law and order in digital spaces.

Political Dissidence and Whistleblowing Platforms
Onion dark websites are hidden parts of the internet accessible only through specialized browsers that prioritize user anonymity and privacy. These platforms host a variety of content, catering to different interests and needs, often operating outside the reach of traditional authorities. Among the most prominent types of content on onion dark websites are those related to political dissidence and whistleblowing platforms, which serve as critical outlets for expression and reform.
One of the common types of content found on onion dark websites revolves around political dissidence. Activists and individuals opposing oppressive regimes or policies utilize these platforms to share information, coordinate actions, and voice dissent without fear of surveillance or retaliation. This content often includes underground news, encrypted messages, and forums for debate that challenge prevailing narratives and advocate for change.
Whistleblowing platforms constitute another significant category of onion dark website content. These sites provide secure channels for individuals to disclose confidential information about corruption, abuse of power, or illegal activities within organizations or governments. By leveraging encryption and anonymization techniques, they ensure the protection of whistleblowers, enabling transparency and accountability in environments where such disclosures might be dangerous or suppressed.
- Encrypted communication channels for secure messaging and data sharing.
- Anonymous forums for discussion and strategic planning related to activism.
- Information repositories that document covert operations or misconduct.
- Platforms facilitating the safe release of sensitive documents and evidence.
The presence of these diverse content types on onion dark websites underscores their importance as sanctuaries for free expression, whistleblowing, and political activism. They provide essential tools for users seeking to expose wrongdoing, challenge authority, and advocate for societal change while maintaining their anonymity and safety. As technology and security measures evolve, such platforms continue to play a vital role in fostering transparency in environments where free speech is severely restricted.
Cybercriminal Services and Hacking Markets
Onion dark websites are platforms that operate on the Tor network, providing a level of anonymity for both users and operators. These sites host a wide variety of content, often associated with illicit activities due to the privacy they afford. Among the most common types of content found on these sites are cybercriminal services and hacking markets, which facilitate illegal transactions and the exchange of hacking tools and exploits.
Cybercriminal services on onion dark websites offer a range of illicit offerings, including malware development, ransomware, phishing kits, and other malicious software. These services may be sold or rented to individuals seeking to carry out cyber attacks while concealing their identity. Hacking markets function as online marketplaces where users can purchase hacking tools, credentials, or access to compromised systems. These markets often operate with escrow services to ensure transaction safety, making it easier for cybercriminals to buy and sell malicious resources.
The content on onion dark websites extends beyond hacking markets and cybercriminal services. They also contain forums, marketplaces for stolen data, illegal pharmaceuticals, counterfeit documents, and black market goods. The anonymity provided by these platforms complicates law enforcement efforts to combat cybercrime, enabling ongoing illegal activities that threaten individuals and organizations alike. As these sites evolve, so too do the methods used by cybercriminals to evade detection, continually posing challenges for cybersecurity efforts worldwide.
Operational Aspects of Onion Dark Web
The operational aspects of the Onion dark web present a complex landscape characterized by unique technical and security considerations. This hidden segment of the internet operates through encrypted layers, ensuring user anonymity and data protection. Managing access, maintaining security protocols, and ensuring the integrity of websites hosted on the dark web require specialized tools and expertise. Entities involved must also address challenges related to law enforcement oversight and the illicit activities often associated with dark web platforms. For those interested in exploring more about dark web operations, there are resources available that provide insights into the technical infrastructure and security measures necessary to operate securely in this environment.
Marketplaces and Financial Transactions (Bitcoin and Cryptocurrencies)
The onion dark web is a hidden layer of the internet that operates anonymously through the Tor network, making it a complex environment for various operational activities. Marketplaces on the dark web facilitate the trade of illicit goods and services, often relying heavily on digital currencies to maintain transactional secrecy. These marketplaces are designed with robust security measures to protect both buyers and sellers, including encrypted communications and anonymized logins. Understanding the operational aspects of these platforms provides insight into their functionality and the financial transactions that sustain them.
Financial transactions on the onion dark web predominantly utilize cryptocurrencies such as Bitcoin, which are favored for their pseudonymous nature and ease of transfer across borders without traditional banking systems. The use of Bitcoin and other cryptocurrencies enables users to conduct transactions with a higher degree of privacy compared to conventional payment methods. These digital currencies are often stored in secured digital wallets, and transactions are processed through blockchain technology that offers transparency and traceability, though often obscured by techniques like mixing or tumbling services.
- Market Infrastructure: Onion dark web marketplaces operate through decentralized networks with layered security measures. They often implement escrow services to hold funds until buyers confirm satisfactory receipt of goods or services, reducing the risk of fraud.
- Operational Security: Sellers and buyers employ various anonymity techniques, including the use of pseudonyms, disposable addresses, and encrypted communication channels, to avoid detection and preserve operational integrity.
- Financial Transactions: Cryptocurrency payments are initiated through secure, encrypted platforms. Bitcoin wallets are often anonymized through the use of mixing services that break transaction linkages, ensuring that the flow of funds remains difficult to trace.
- Legal and Compliance Challenges: Due to the anonymous nature of operations and financial transfers, enforcing legal compliance remains challenging, and authorities frequently attempt to monitor and disrupt these marketplaces by analyzing blockchain activity and infiltration efforts.
Overall, the operational aspects of the onion dark web, especially concerning marketplaces and financial transactions, involve a delicate balance of security protocols, privacy protections, and technological sophistication. These elements make it a resilient environment for various underground activities, despite ongoing law enforcement efforts to identify and shut down malicious operators.
Market Dynamics and Price Comparisons
The onion dark web represents a hidden segment of the internet that operates using anonymizing protocols, primarily through the Tor network. This platform allows users to access specialized websites that are not indexed by traditional search engines, providing a degree of privacy and anonymity for both site operators and visitors. The operational aspects of the onion dark web involve dedicated servers, encrypted communications, and complex routing systems designed to evade detection and censorship. These technical features enable a wide range of illicit and legal activities to coexist in a clandestine environment.
Market dynamics within the onion dark web are characterized by a unique ecosystem where products and services are exchanged in a largely unregulated environment. This environment fosters rapid innovation, while also creating fluctuations in supply and demand. Markets on the dark web often see seasonal trends and periodic shifts based on law enforcement activity, technological changes, or geopolitical events. Sellers and buyers rely heavily on reputation systems, escrow services, and encrypted communications to facilitate transactions securely and maintain trust amid challenging operational circumstances.
Price comparisons on the onion dark web can vary significantly depending on the type of goods or services offered. Factors such as rarity, security risks, and regional demand influence pricing structures. For example, certain illegal substances or cybercrime tools may command premium prices due to their scarcity or complexity. Conversely, some markets see competitive pricing that encourages volume sales. Navigating these price disparities requires an understanding of market nuances and the underlying risks involved in transactions conducted through anonymous platforms like onion dark websites.
Law Enforcement Challenges and Tactics
The onion dark web serves as a hidden part of the internet that operates on layered encryption, providing users with increased anonymity and privacy. This unique environment hosts a variety of content, including both legitimate and illicit activities. Due to its anonymous nature, the onion dark web has become a focal point for law enforcement agencies, which face significant challenges in monitoring and regulating these platforms. Understanding the operational aspects of such sites is crucial for developing effective strategies to combat illegal activities while respecting privacy concerns.
Law enforcement agencies encounter numerous challenges when investigating onion dark web sites. The primary obstacle is the high level of privacy and encryption used to conceal user identities and site locations. This makes tracing activities and identifying perpetrators difficult. Additionally, the decentralized nature of the onion dark web, coupled with the frequent use of anonymizing tools like Tor, complicates efforts to gather evidence and conduct undercover investigations. Jurisdictional complexities further hinder coordinated responses across borders.
Despite these challenges, authorities have adopted several tactics to combat illegal activities on onion dark websites:
- Technical Surveillance: Utilizing specialized software and cyber forensics tools to analyze traffic patterns and identify vulnerabilities in site infrastructure.
- Undercover Operations: Deploying trained officers to infiltrate illegal marketplaces and forums, gathering intelligence on buyers and sellers.
- Legal and Diplomatic Measures: Working with international partners to issue warrants, facilitate takedown operations, and share intelligence to dismantle criminal networks.
- Disruption and Takedown: Coordinating efforts within the legal framework to seize servers, shut down sites, and disrupt prohibited operations.
- Public Awareness and Education: Informing users about the risks associated with dark web activities and encouraging safe browsing practices to prevent victimization.
In conclusion, the clandestine operations of onion dark websites present significant operational and legal challenges for law enforcement. While technologically sophisticated tactics are employed to investigate and dismantle illegal activities, ongoing adaptation and international cooperation are essential for effective management. As the dark web continues to evolve, understanding its operational dynamics is key to developing sustainable strategies that balance privacy rights with security concerns.
Exploit and Scam Sites
The onion dark web is a hidden segment of the internet that operates beyond the reach of traditional search engines and standard web browsers. It is characterized by its use of the Tor network, which provides anonymity for both users and website operators. This environment facilitates various activities, ranging from legitimate privacy-focused communications to malicious operations. Understanding the operational aspects of these sites is crucial for cybersecurity professionals and law enforcement agencies working to combat illegal activities.
Onion dark web sites are often exploited by malicious actors to host scam, exploit, and illicit marketplaces. These sites typically employ advanced encryption methods to conceal their identities and locations, making investigation and takedown challenging. Exploit sites may distribute malware, perform phishing campaigns, or sell stolen data, while scam sites often deceive users through fake reviews, false advertisements, or counterfeit products. The anonymity provided by the onion service attracts cybercriminals looking to conduct operations without fear of detection.
Operationally, managing onion dark web sites requires specialized knowledge of the Tor network and cybersecurity protocols. Operators often use layered security measures, including encryption, obfuscation techniques, and operational security practices, to evade law enforcement and detection. These sites frequently change their domain addresses or shut down temporarily to avoid shutdowns and investigations. The decentralized nature of the dark web complicates efforts to monitor, regulate, and dismantle malicious infrastructure hosted on onion sites.
The dark web’s exploit and scam sites pose significant threats to individuals and organizations. They can lead to financial loss, privacy breaches, and identity theft. Understanding their operational aspects helps security professionals develop better detection and prevention strategies to protect users and disrupt illegal activities. Continuous monitoring, technological innovation, and international cooperation are essential in addressing the challenges associated with onion dark web sites.
Security and Risks Associated with Onion Dark Websites
Accessing and exploring the world of onion dark websites presents a unique set of security concerns and risks. These hidden networks, often utilized for anonymous communication and illegal activities, can expose users to malicious threats such as hacking, scams, and data theft. The *onion dark website* environment is notorious for its lack of regulation, making it a hotspot for cybercriminals and illicit transactions. Users must exercise extreme caution and implement robust security measures to protect their identity and digital assets when venturing into these anonymous online spaces. To better understand the intricacies and potential dangers, you can explore various onion sites, such as this secure onion link.
Malware, Trojans, and Backdoors
The onion dark website network operates as a hidden part of the internet, providing anonymity and privacy for its users. While this anonymity can serve legitimate purposes such as protecting free speech and privacy, it also creates a fertile ground for various security threats and risks. Users accessing these hidden sites often encounter a higher likelihood of malware, Trojans, and backdoors that can compromise their privacy and security.
Malware on onion dark websites can be particularly malicious, designed to infect devices silently when users visit compromised or malicious sites. These malicious software programs can steal sensitive information, monitor user activity, or even take control of the infected device. Trojans are a common form of malware found on such sites; they masquerade as legitimate files or software but secretly perform harmful actions once executed, often remaining hidden from the user’s detection.
Backdoors are another significant threat associated with onion dark websites. Attackers may install backdoor mechanisms to gain persistent and unauthorized access to computers or networks. These backdoors can lead to further exploitation, data breaches, or the use of infected systems for malicious activities such as launching attacks or hosting illegal content.
Because of these risks, navigating onion dark websites requires caution. Users should ensure they have robust security measures in place, including updated antivirus software, strong firewalls, and secure communication protocols. Recognizing the risks associated with these hidden sites underscores the importance of maintaining vigilant cybersecurity practices to prevent falling victim to malware, Trojans, or backdoors that can compromise personal and organizational security.
Scam Operations and Fraudulent Sites
Onion dark websites are part of the deep web that utilize the Tor network to offer anonymity to users and operators alike. While this hidden segment of the internet can host legitimate activities, it is also frequently associated with significant security risks and illegal operations. The inherent secrecy of these sites makes them attractive for malicious actors seeking to evade law enforcement and engage in unlawful activities.
One of the primary security concerns surrounding onion dark websites is the prevalence of scam operations and fraudulent schemes. These sites often impersonate legitimate businesses or services to deceive users into providing sensitive information, making payments, or downloading malicious software. Because these websites operate with high levels of anonymity, it becomes challenging to track and prosecute offenders, leading to a higher incidence of scams and fraud.
Additionally, users visiting onion dark websites face numerous risks, including exposure to malware, hacking attempts, and theft of personal data. Cybercriminals frequently use these platforms to distribute ransomware, spyware, or other malicious tools. In many cases, scammers create convincing fake sites designed to look authentic, enticing visitors to reveal confidential information or make financial transactions that are ultimately fraudulent.
Law enforcement agencies worldwide continue to monitor these sites to combat illegal activities, but the clandestine nature of onion dark websites complicates their efforts. For individuals, engaging with these sites carries the risk of legal repercussions, financial loss, and exposure to harmful content. Therefore, it is vital for users to exercise caution and remain aware of the potential security threats associated with visiting or interacting with onion dark websites.
Data Breaches and Compromised User Information
The onion dark web hosts a variety of sites that operate beyond the reach of traditional internet infrastructure, offering anonymity and privacy for their users. While these features can be beneficial for privacy advocates and activists, they also pose significant security risks. One of the primary concerns associated with onion dark websites is the heightened potential for cyber threats, including data breaches and compromised user information.
Due to the anonymous nature of onion dark websites, malicious actors often exploit this environment to conduct illegal activities, such as the dissemination of illicit goods or services. These activities increase the likelihood of cyberattacks targeting both users and site operators. Data breaches are common in this space, where hackers may infiltrate sites to steal sensitive information, including login credentials, payment details, or personal data. Once compromised, this information can be sold or misused, leading to identity theft or financial fraud.
Users accessing onion dark websites often operate under a false sense of security provided by anonymity, but this can be misleading. The security measures in place may not be sufficient to prevent breaches, and vulnerabilities in website architecture or user behavior can be exploited. Additionally, law enforcement agencies often monitor these sites, and infiltration efforts can lead to legal consequences or exposure of user identities.
It is crucial for users and operators to understand the risks associated with engaging with onion dark websites. Employing strong security practices, such as using secure and updated software, enabling multi-factor authentication, and avoiding sharing personal or sensitive information, can mitigate some risks. However, the inherently risky environment of the onion dark web means that complete security cannot be guaranteed, and users should remain cautious to avoid falling victim to cyberattacks or data compromises.
Risks of Exposure to Illegal Content
Accessing and exploring onion dark websites presents significant security challenges and risks, particularly related to exposure to illegal content. These websites operate on the Tor network, providing anonymity to users and hosts, which unfortunately also facilitates illegal activities and malicious behavior. Engaging with such sites can inadvertently expose users to harmful content, scams, and cyber threats.
One major risk associated with onion dark websites is the potential exposure to illegal or malicious content. Due to the anonymous nature of these sites, illegal activities such as drug trafficking, weapons sales, and counterfeit currency exchanges are often conducted here. Users may unintentionally come across disturbing or illegal materials, which could have legal or moral consequences.
Security concerns on the dark web extend beyond illegal content. Users face increased risks of malware infections, hacking, and identity theft. Cybercriminals frequently use these platforms for scams, phishing, and distributing malicious software designed to compromise personal information and devices. Without proper cybersecurity measures, browsing these sites can leave users vulnerable to significant harm.
Furthermore, attempting to access onion dark websites can lead to exposure to law enforcement operations targeting illegal activities. Law enforcement agencies monitor these sites to combat illicit trade and cybercrime. Consequently, users involved in or merely browsing these sites may inadvertently attract attention, risking legal repercussions.
In summary, while the dark web provides a layer of anonymity, exploring onion dark websites carries substantial security risks, especially regarding illegal content exposure. Users should exercise extreme caution, prioritize cybersecurity, and be aware of the legal and ethical implications associated with browsing these sites to mitigate potential dangers.
Law Enforcement and Monitoring of Onion Sites
Law enforcement agencies around the world are increasingly focused on monitoring and regulating onion dark websites due to their association with illicit activities and anonymous communication. These hidden networks pose unique challenges for authorities seeking to maintain security and uphold legal standards. Effective monitoring of onion dark websites requires specialized techniques to identify and investigate illegal content while respecting privacy and legal boundaries. For those interested in exploring secure and privacy-focused platforms, there are legitimate onion sites that offer valuable resources and services. One such example is a trusted onion address that provides access to encrypted and anonymous communication channels, supporting lawful activities and research.
Operations and Tactics for Takedown
Law enforcement agencies globally have developed specialized strategies for monitoring and addressing activities on onion dark websites, which are often used for illicit operations due to their enhanced privacy features. These operations involve a combination of technical tactics and investigative techniques aimed at identifying, tracking, and dismantling illegal marketplaces, forums, and services hosted on the Tor network. Due to the encrypted and anonymous nature of onion sites, authorities often deploy advanced digital forensics, network analysis, and undercover operations to gather intelligence and build cases against operators and users involved in unlawful activities.
To effectively combat criminal activity on onion dark websites, law enforcement agencies employ a variety of operational tactics including site infiltration, controlled takedown operations, and collaboration with cybersecurity experts. These operations may involve deploying malware, monitoring traffic patterns, or setting up sting operations to identify key players and their associates. The goal is to disrupt illegal marketplaces that facilitate drug trafficking, weapons sales, cybercrime, and other illicit pursuits, ultimately aiming to reduce the prevalence of such activities on the dark web.
Operational tactics for takedown often begin with meticulous intelligence gathering, followed by coordinated efforts to seize hosting infrastructure or identify operators behind onion sites. Once identified, agencies may execute legal and technical measures to shut down or take control of these sites, often working with international partners to broaden the scope of enforcement. Despite the challenges posed by the anonymized environment, proactive monitoring and tactical interventions continue to be essential tools in maintaining law and order within this clandestine digital realm.
Understanding the complexity and evolving nature of onion dark websites is crucial for law enforcement to adapt their tactics and stay ahead of criminal networks. Continuous research, technological innovation, and international cooperation are fundamental components of successful operations aimed at dismantling online illegal enterprises and safeguarding public safety in the digital age.
Open Source Intelligence (OSINT) Applications
Law enforcement agencies utilize advanced techniques to monitor and investigate activities on onion dark websites, which are commonly accessed through the Tor network to maintain anonymity. These hidden sites often host illicit content and facilitate illegal transactions, making their surveillance critical for national security and crime prevention efforts. Open Source Intelligence (OSINT) tools play a vital role in these investigations by aggregating publicly available information from various sources to support law enforcement efforts in identifying and tracking malicious actors operating on the dark web.
Effective monitoring of onion dark websites involves a combination of technical skills, specialized tools, and strategic intelligence gathering. OSINT applications enable investigators to analyze digital footprints, track suspicious transactions, and identify patterns indicative of illegal operations. These methods are crucial in building cases against individuals or groups involved in illicit activities on the dark web.
- Network Monitoring: Agencies deploy nodes and sensors within the Tor network to collect metadata and traffic analysis data, helping locate criminal activities without compromising user anonymity.
- Content Analysis: Automated tools scan and categorize content hosted on onion sites, flagging illegal content such as drugs, weapons, or stolen data.
- Transaction Tracking: By monitoring cryptocurrency transactions associated with dark web marketplaces, investigators can trace financial flows pertinent to criminal enterprises.
- Open Source Data Aggregation: OSINT tools compile information from forums, social media, and leaks related to onion sites, offering insights into user activities and network structures.
- Undercover Operations: Law enforcement sometimes employs undercover agents or infiltration tactics within these dark networks to gather intelligence firsthand.
Despite the challenges posed by the anonymity-focused infrastructure of onion dark websites, the combination of sophisticated monitoring techniques and OSINT applications enhances law enforcement capabilities. Continual advancements in digital forensics and intelligence analysis are vital to combating cybercrime and ensuring that illicit activities on the dark web are identified and prosecuted effectively.
International Collaboration and Training Programs
Law enforcement agencies play a critical role in monitoring and addressing activities on onion dark websites, which are often associated with illegal operations and illicit trade. These agencies utilize specialized techniques and tools to track and gather intelligence on criminal entities operating within encrypted and anonymous environments. The inherently covert nature of onion sites presents unique challenges, requiring a combination of technical expertise, cyber intelligence, and strategic surveillance to identify and disrupt unlawful activities.
International collaboration is essential in combating illegal activities on onion dark websites. Law enforcement organizations across different countries share intelligence, coordinate operations, and develop unified strategies to tackle transnational crimes. This cooperative approach enhances the effectiveness of investigations and helps close jurisdictional gaps, ultimately reducing the prevalence of illegal marketplaces and services hosted on these hidden networks.
To improve the efficacy of monitoring and enforcement, various organizations promote training programs aimed at equipping law enforcement personnel with the skills necessary to investigate onion dark websites. These programs include workshops on digital forensics, anonymization techniques, and cyber operational tactics. Continuous education ensures that investigators stay abreast of rapidly evolving technologies and methodologies, enabling them to effectively counter threats emerging from the onion dark web landscape.
Overall, the combined efforts of law enforcement, international agencies, and specialized training initiatives are vital in addressing the complexities of onion dark websites. By enhancing investigative capabilities and fostering global cooperation, authorities can better combat cybercrime and uphold legal standards within the digital realm.
Legal Implications and Challenges of Regulation
The dark web, accessed through specialized networks such as the Tor network, hosts a variety of websites including onion dark websites that operate with a high level of anonymity. Law enforcement agencies face significant challenges when it comes to monitoring and regulating these sites, as their design prioritizes user privacy and concealment of identities. This creates a complex environment where illegal activities, such as drug trafficking, arms trading, and illicit services, can prosper outside the reach of traditional oversight.
Monitoring activities on onion dark websites requires advanced technological tools and considerable expertise. Agencies often employ methods such as traffic analysis, undercover operations, and cyber forensics to gather intelligence. However, the encrypted and anonymous nature of these sites complicates efforts to identify perpetrators and collect evidence suitable for prosecution. This ongoing cat-and-mouse game poses profound legal and ethical questions about the balance between privacy rights and the need for law enforcement to combat crime.
The regulation of onion dark websites also raises complex legal implications. International jurisdictional issues arise since the dark web’s global reach makes it difficult to enforce national laws uniformly. Efforts to regulate or shut down illicit activities often involve intricate legal procedures and cooperation between different countries’ authorities, which can be hindered by conflicting legal standards and concerns over privacy infringements. Moreover, there are debates about civil liberties and the potential for overreach in surveillance practices targeting the dark web.
The challenges faced by law enforcement highlight the need for a nuanced approach to regulation—one that respects individual privacy while effectively addressing criminal conduct. Enhancing digital forensic capabilities, fostering international cooperation, and establishing clear legal frameworks are critical steps in tackling the illicit uses of onion dark websites. As technology advances, so too must strategies for balancing security concerns with the fundamental rights of users in the digital landscape.
Emerging Trends and Future of Onion Dark Websites
The landscape of onion dark websites is continuously evolving, driven by technological advancements and shifting user needs. As security and anonymity remain paramount, new trends are emerging that enhance privacy, accessibility, and content diversity within this hidden part of the internet. The future of onion dark websites will likely see increased integration of decentralized systems and innovative encryption methods, making them more resilient against censorship and surveillance. Exploring these emerging trends can provide valuable insights into the potential developments of this secretive digital domain, exemplified by platforms like onion dark websites that serve a broad spectrum of uses from secure communication to illicit trade. For those interested in understanding the structure and security features of onion sites, visiting specialized resources can offer deeper knowledge, such as the platform at this link.
Development of Social Media Platforms
The landscape of onion dark websites is continuously evolving, driven by technological advancements and changing user behaviors. These hidden parts of the internet have historically been associated with illicit activities, but they also serve legitimate purposes such as ensuring privacy and free expression. As encryption methods improve and anonymity tools become more sophisticated, the future of onion dark websites is poised for greater security, resilience, and versatility.
Emerging trends indicate a shift toward more secure and user-friendly interfaces within dark web environments. Innovations in decentralized architecture and blockchain technology could offer enhanced privacy and control, making these platforms more robust against censorship and takedown efforts. Additionally, the development of specialized search engines and indexing tools tailored for onion sites will facilitate safer and more efficient navigation, broadening access to legal and educational resources.
The development of social media platforms on the onion network is a notable trend, aiming to provide secure communication channels for users worldwide. These platforms are increasingly adopting end-to-end encryption and anonymous user verification methods to protect identities while fostering free exchanges of ideas. The future may see a rise in decentralized social networks that are resistant to censorship, promoting open dialogue and community building in a safe environment.
Overall, the future of onion dark websites and related social media platforms is characterized by a focus on enhanced privacy, security, and decentralization. As technology advances, these platforms are likely to become more accessible and trusted, enabling users to navigate the digital underground with greater confidence and safety.
Innovations in Anonymity Technologies
The landscape of onion dark websites is continuously evolving, driven by advancements in technology and changing user needs. These hidden sites, accessible only through specialized browsers, serve a variety of purposes ranging from privacy preservation to hosting illicit activities. As the digital environment shifts, new trends are emerging that significantly shape the future of the dark web, especially on onion networks. Innovations in anonymity technologies are at the forefront of this transformation, enhancing both security and user privacy.
One of the key emerging trends is the integration of decentralized architectures within onion dark websites. These architectures leverage blockchain and peer-to-peer networks to decentralize hosting, reducing reliance on centralized servers and making it more difficult for authorities to shut down sites. Additionally, there is a growing adoption of novel encryption protocols which improve data security and user anonymity. Technologies such as advanced cryptographic algorithms and privacy-preserving communication channels are being implemented more frequently in onion dark websites to prevent tracking and surveillance.
Furthermore, the development of automated and AI-powered tools is transforming the way dark web sites are managed and accessed. These tools can help hide IP origins more effectively, detect potential threats, and facilitate secure communication. Innovations like ephemeral hosting instances, which are temporary and automatically self-destruct after use, increase the difficulty in tracking and prosecuting illicit activities while maintaining user privacy.
Looking ahead, the future of onion dark websites will likely see increased use of innovations designed to enhance anonymity, resilience, and secure communication channels. Enhancements in traffic obfuscation techniques, such as mimicry of regular internet traffic, help evade detection by monitoring entities. As these technologies evolve, the onus is on users and developers to ensure that such advancements are used responsibly, balancing privacy needs with legal and ethical considerations.
- Decentralized hosting and peer-to-peer networks
- Advanced encryption and cryptography protocols
- AI-driven security and anonymity tools
- Ephemeral and self-destructing hosting instances
- Traffic obfuscation and mimicry techniques
Growing Use by Cybercriminals and Terrorists
The landscape of onion dark websites is continuously evolving, shaping the future of online anonymity and illicit activities. As technology advances, these hidden sites are becoming more sophisticated, offering enhanced security features that appeal to both legitimate users seeking privacy and malicious actors engaging in illegal operations. The increasing deployment of encryption protocols and decentralized hosting methods is making it harder for authorities to track and shut down these sites, contributing to their persistent presence on the dark web.
Emerging trends indicate a rise in the use of onion dark websites by cybercriminals and terrorists for conducting covert communications, trading illicit goods, and spreading propaganda. These sites often operate as secure marketplaces or forums, avoiding traditional censorship and monitoring. The anonymity provided by the Tor network allows perpetrators to evade law enforcement, complicating efforts to combat cybercrime and terrorism networks. As these threats grow, there is a corresponding push for improved detection and surveillance techniques to understand and disrupt illegal activities on these hidden platforms.
Looking ahead, the future of onion dark websites hinges on innovations in both offensive and defensive cybersecurity. While malicious actors refine their methods for maintaining secrecy and circumventing detection, security agencies and researchers are developing more advanced tools for monitoring and analyzing dark web activities. The continuous arms race highlights the importance of adopting comprehensive cybersecurity strategies that balance privacy rights with the need for security. Ultimately, understanding the emerging trends in onion dark websites is crucial for shaping policies and technological solutions to mitigate their negative impact while respecting individual privacy rights.
Potential for Legitimate and Civil Liberties Uses
The landscape of onion dark websites is continuously evolving, driven by technological advancements and shifting user needs. As these hidden sites become more sophisticated, they present both challenges and opportunities in various sectors. Emerging trends suggest a future where security, privacy, and legitimate uses could reshape the perception and function of dark web platforms. Understanding these developments is crucial for anticipating how onion dark websites might adapt and serve society in new ways.
One significant trend is the increased focus on enhanced security protocols to protect user anonymity and data integrity. Innovations such as decentralized architectures and improved encryption methods are making it harder for malicious actors to exploit these networks, while simultaneously enabling legitimate users to operate with greater privacy and safety. Furthermore, the development of tools aimed at reducing illicit activities is helping to legitimize and normalize the use of onion dark websites for lawful purposes.
Potential future uses of onion dark websites extend beyond clandestine activities, offering promising avenues for civil liberties and transparent communication. These sites could serve as platforms for whistleblowers, journalists, and activists to share information securely without fear of censorship or retaliation. Moreover, encrypted communication channels on onion sites could foster freedom of expression in regions with oppressive regimes, supporting human rights and democratic movements.
- Security and Privacy Enhancements: Ongoing improvements in encryption and decentralized technology aim to bolster user safety while deterring misuse.
- Legitimate Content and Services: Increasingly, onion dark websites are being used for secure correspondence, confidential research, and privacy-focused communications.
- Support for Civil Liberties: The future of onion dark websites may see greater utilization for activism, whistleblowing, and safeguarding free speech in restrictive environments.
- Technological Innovation: Adoption of emerging innovations such as blockchain or zero-knowledge proofs could further enhance the functionality and legitimacy of these platforms.
Overall, the future of onion dark websites appears to be marked by a potential shift towards greater legitimacy and societal benefit. As technology advances and awareness grows around privacy rights, these platforms might evolve from tools associated with illicit activities to vital resources for civil liberties, secure communication, and digital privacy.

